Home » security career
Articles Tagged with ''security career''
How is a Security Systems Management Platform the next frontier in enterprise security risk management?
Read More
The Most Influential People in Security 2018
Who’s leading the way for security professionals? These 17 thought-leaders are making a difference.
September 1, 2018
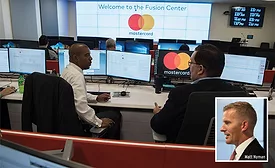
A Nucleus of Information-Sharing: Mastercard’s Fusion Center
When it comes to addressing global fraud and security in the financial sector, it takes a network to defeat a network.
August 8, 2018
In a Day’s Work: The Fight to End Workplace Violence
How are Cox Enterprises and others effectively reducing the risk of workplace violence in their organizations?
August 2, 2018
Sign-up to receive top management & result-driven techniques in the industry.
Join over 20,000+ industry leaders who receive our premium content.
SIGN UP TODAY!Copyright ©2026. All Rights Reserved BNP Media.
Design, CMS, Hosting & Web Development :: ePublishing