Product Spotlight
Cybersecurity threat monitoring and risk assessment solutions

Image by Freepik
Security leaders rely on a number of threat monitoring and risk assessment tools and solutions to understand, identify and mitigate threats to the enterprise. From security vulnerability scanning to supply chain and third-party risk monitoring, Security magazine spotlights cybersecurity threat monitoring and risk assessment solutions that can help improve security posture at various organizations.
BlackBerry
Protects Private Cloud and On-Premises Applications
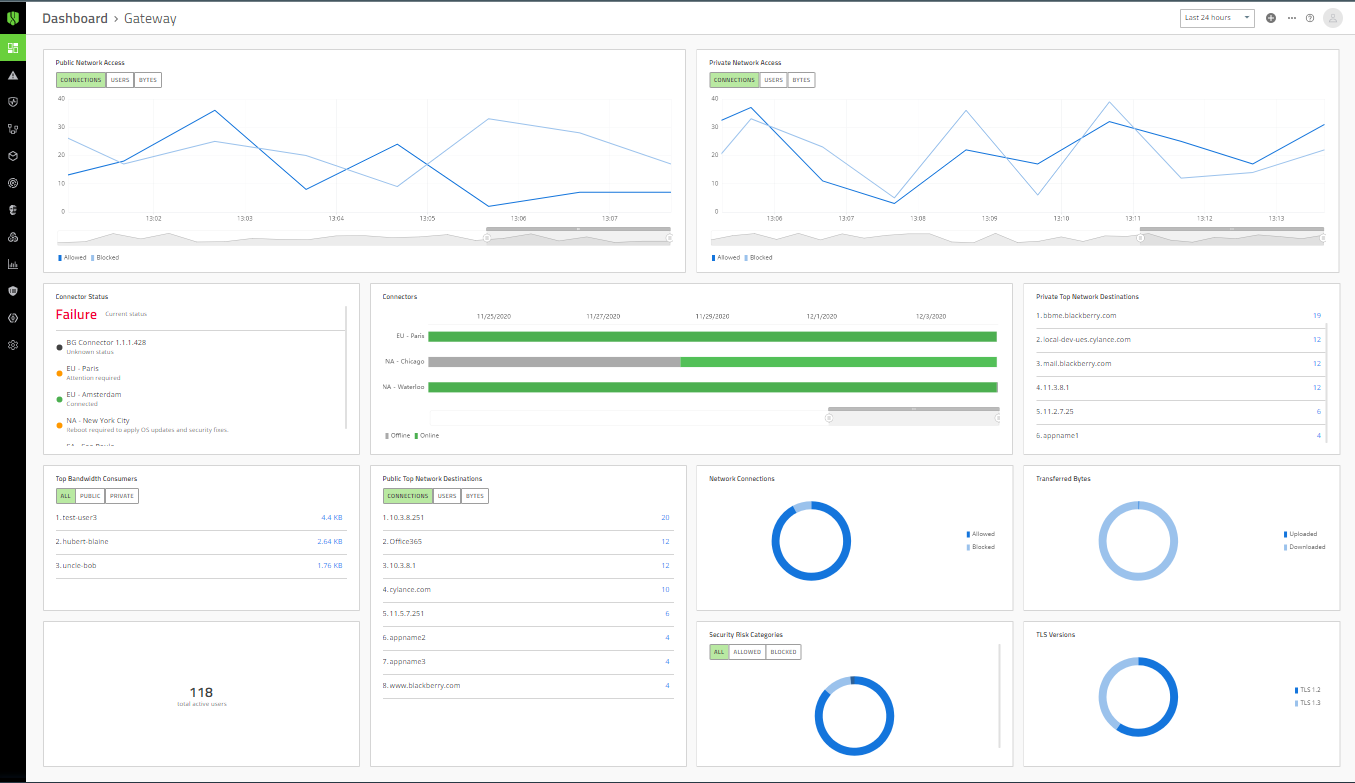
Designed to support work-from-anywhere deployment models while helping to remediate and automate network risk for both managed and BYO unmanaged devices, CylanceGATEWAY is BlackBerry’s Zero Trust Network Access (ZTNA) as a Service solution. ZTNA is a component of the company’s Managed Extended Detection and Response (XDR), which searches for and addresses cyber threats across an enterprise’s entire digital environment, including its network, cloud storage, applications and endpoints. CylanceGATEWAY helps enhance user activity visibility, protecting users against the prolific growth of ransomware and other advanced cybersecurity threats by delivering access to private applications hosted on-premises or Software as a Service (SaaS) apps in the public cloud. Image courtesy of BlackBerry
Find out more at www.blackberry.com
Black Kite and LogicGate
Enhances Third-Party Risk Capabilities
LogicGate partnered with Black Kite to enhance its risk quantification solution for third parties. The integration of Black Kite’s cyber ratings, Open factor analysis of information risk (FAIR) financial risk quantification, compliance correlation and Ransomware Susceptibility Index into LogicGate’s Risk Cloud platform offers organizations insights into their risk posture to better help them manage cyber risks with suppliers and partners, as well as share findings with stakeholders. With this integration, organizations can incorporate security ratings into their cyber risk programs and scale their third-party risk programs while helping eliminate silos between risk, compliance and audit teams. Image courtesy of LogicGate and Black Kite
Find out more at www.logicgate.com and www.blackkite.com
Codenotary
Monitors Supply Chain Security
Codenotary’s latest Codenotary Cloud version now includes vulnerability scanning, as well as the ability to integrate with other vulnerability scanners to provide software supply chain security and DevSecOps – from checking for vulnerabilities to cryptographic verification and tracking verified software artifacts in a Software Bill of Materials (SBOM) for compliance with the U.S. Executive Order on Improving the Nation’s Cybersecurity. The solution provides tools for notarization and verification of the software development lifecycle attesting to the provenance and safety of the code. Codenotary Cloud can be integrated with popular cloud-native continuous integration/continuous delivery (CI/CD) systems. Image by user6164906 via Freepik
Find out more at www.codenotary.com
Cybersixgill
Threat Intelligence for Cyber Decision-Making

Cybersixgill partnered with Snowflake Data Marketplace to integrate its deep, dark and clear web threat intelligence into the Snowflake security data lake. With this integration, organizations have access to critical information around risk vulnerabilities, can determine if they’re being targeted, and take action before a breach occurs to help strengthen security posture. The Snowflake Data Marketplace gives data scientists, business intelligence, and analytics professionals access to more than 800 data sets from over 200 third-party data providers and data service providers. Organizations have access to malware insights, compromised sites and endpoints, and an automated feed of data about malicious indicators of compromise (ICOs). Image by bioncoblue via Freepik
Find out more at www.cybersixgill.com
Digital Element
Helps Protect Infrastructure and Data

Digital Element’s Nodify is a threat intelligence solution designed to help security professionals respond to virtual private network (VPN) threats to corporate and government networks and data. Nodify provides critical context surrounding VPN traffic, enabling cybersecurity teams to understand the level of threat such traffic poses, as well as set policy around that traffic. To help security professionals assess VPN traffic, Nodify delivers contextual insight, including VPN classification (masked, public, private), provider's name/URL, whether the provider allows for user anonymity and logs user activity, IP addresses related to a provider, languages of the target market of the VPN provider, and more to prevent bad actors from infiltrating or hijacking their systems by identifying anonymized connections. Image by your photo via Freepik
Find out more at www.digitalelement.com
Digital Shadows
Scans for Security Vulnerabilities

Digital Shadows’ Vulnerability Intelligence module within SearchLight helps security teams identify common vulnerabilities and exposures (CVEs) to prevent criminals from exploiting them. The module is combined with continuous monitoring of code repositories, paste sites, social media, vendor websites, and advisories to provide a view of real-world interest and exploitation. A team of analysts provides additional research, removes unnecessary noise, and provides a source assessment for each related event. The capability improves several existing workflows, as users can search for evidence of exploitation and other risk factors, ensuring they are scanning for the vulnerabilities that can pose the biggest risk. Image by Freepik
Find out more at www.digitalshadows.com
Effectiv
Fraud and Risk Management for FinTech

A no-code orchestration platform, Effectiv’s enterprise-grade fraud and compliance solution can be integrated into existing systems with little to no configuration for mid-sized banks, credit unions and financial institutions. Using advancements in artificial intelligence (AI), the solution helps organizations adapt to new security trends to reduce and manage fraud and risk, as well as detect suspicious behavior. With the platform’s capabilities, security leaders can conduct automated fraud and compliance checks. Image by rawpixel.com via Freepik
Find out more at www.effectiv.ai
Fortress Information Security
Offers Insight Into Supply Chain Security
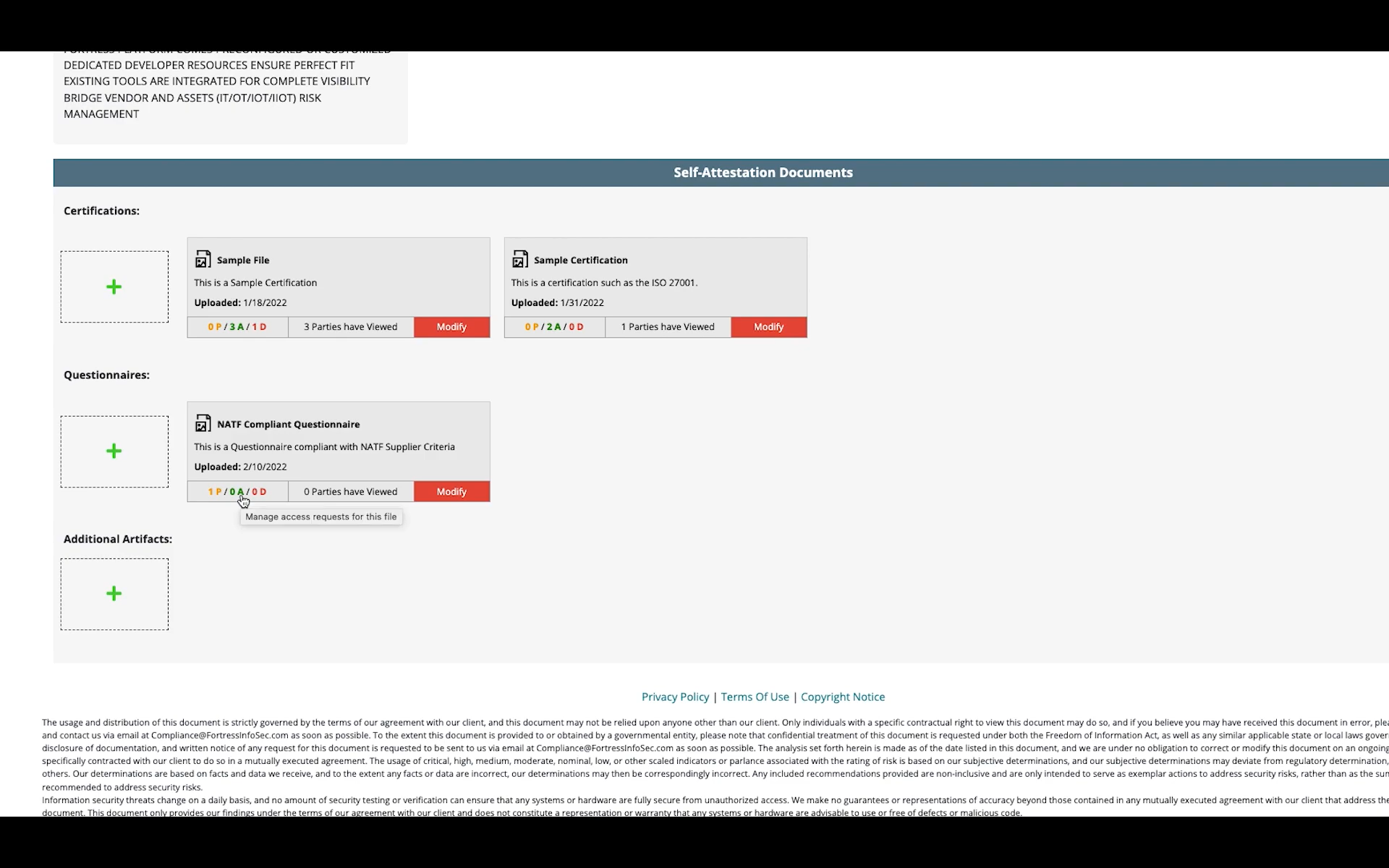
Fortress Information Security’s Asset to Vendor (A2V) Library Trust Center is a supplier-centered marketplace that can share and update cybersecurity information and provide product marketing materials for patrons. The A2V Library enables vendors and Original Equipment Manufacturers (OEMs) to control the information provided to users, such as security attestations, completed North American Transmission Forum (NATF) questionnaires, and third-party certifications. The supplier Trust Center provides users with other capabilities, including: compliance management and audit preparation questionnaires and surveys pattern to meet regulatory standards; data-driven risk ranking that employs AI and open-source intelligence to determine the criticality and cyber maturity of supplier assets; and insights into the geopolitical relationships of suppliers, their products, and their fourth-party suppliers. Image courtesy of Fortress Information Security
Find out more at www.fortressinfosec.com
Netenrich
Secures Digital Security Operations

Netenrich’s Resolution Intelligence platform analyzes real-time security data to determine which high-impact organizational resources are most vulnerable, at critical risk and need an immediate response. To rank the most critical issues and behaviors, the platform aggregates and correlates security and operations data across networks, clouds and applications. The platform integrates with Google Chronicle to bring security data into the platform’s data lake, as well as other data assets for analysis. With the platform, users and their security operations can anticipate risky behaviors, disrupt threats and ensure business resilience. Image courtesy of Netenrich
Find out more at www.netenrich.com
Ostrich Cyber-Risk
Helps Understand Cyber Risk
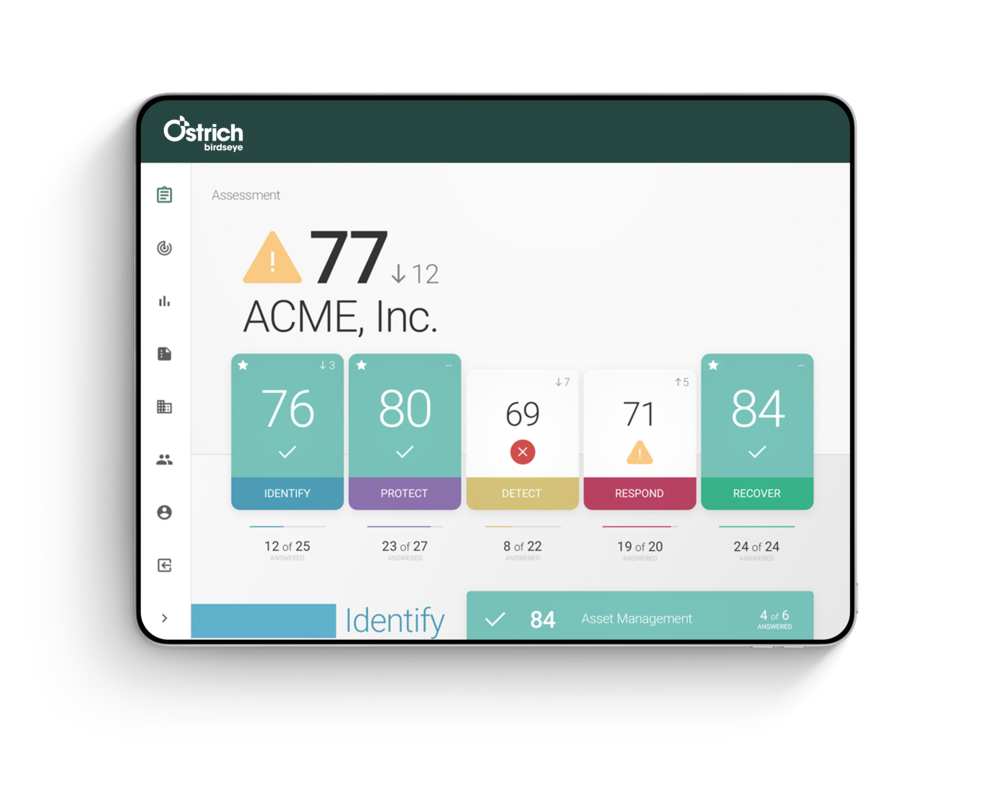
Ostrich Cyber-Risk’s Birdseye is a solution for cyber risk analysis and reporting, which organizations can use to assess their unique risk fingerprint and generate actionable and shareable insights to help develop a strategic approach to cybersecurity. The platform can help identify their unique areas of financial and operational risk and accurately convey that information to key stakeholders. With Birdseye, leaders can track risk reduction over time with analysis of current and planned behaviors; compare their approach to industry peers; and ensure compliance by benchmarking against established security standards. At every stage, users are able to easily produce board-level reports and dashboards with real-time, transparent scoring designed to encourage effective dialog with users and executives. Image courtesy of Ostrich Cyber-Risk
Find out more at www.ostrichcyber-risk.com
Pactera EDGE
Protects From Online Retail Fraud

Pactera EDGE’s Digital Fraud Protection solution uses AI and machine learning (ML) models to detect and combat new forms of e-commerce fraud. The solution offers purchase protection, account protection, and post purchase dispute resolution to help control digital fraud risks. In addition to helping prevent revenue and reputational losses from such breaches, the platform also inserts humans in the loop to improve business intelligence and operational efficiencies for users. Pactera EDGE’s solution leverages fraud detection platforms such as Microsoft’s DFP, and helps ensure General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) compliance offering to further mitigate the risk of experiencing criminal loss. Image by biancoblue via Freepik
Find out more at www.pacteraedge.com
ReliaQuest
Pinpoints Gaps in Risk Management Programs

ReliaQuest has expanded its GreyMatter platform with support for MITRE ATT&CK v10 and Risk Scenarios that visually map and measure a security program’s detection coverage in terms of threats and cyber risks. This new feature enables security leaders to close the communications gap with business leaders. With the ability to map coverage against Risk Scenarios, GreyMatter helps security leaders have a real-time view of how they perform against individual threats or cyber risks of concern. The solution can pinpoint any gaps in coverage and make informed decisions on how best to proceed with investments and actions to close these gaps. Breakdowns by cyber risk categories and subcategories help security leaders focus on areas of concern at a granular level. Image by biancoblue via Freepik
Find out more at www.reliaquest.com
For more articles on threat monitoring and risk assessments, visit:
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!







