Cybersecurity solutions roundup 2021
.webp?t=1639772182)
Security magazine spotlights cybersecurity solutions released in 2021, covering everything from insider risk mitigation to improved threat monitoring.
Aqua Security
Protects Cloud Native Security Goals
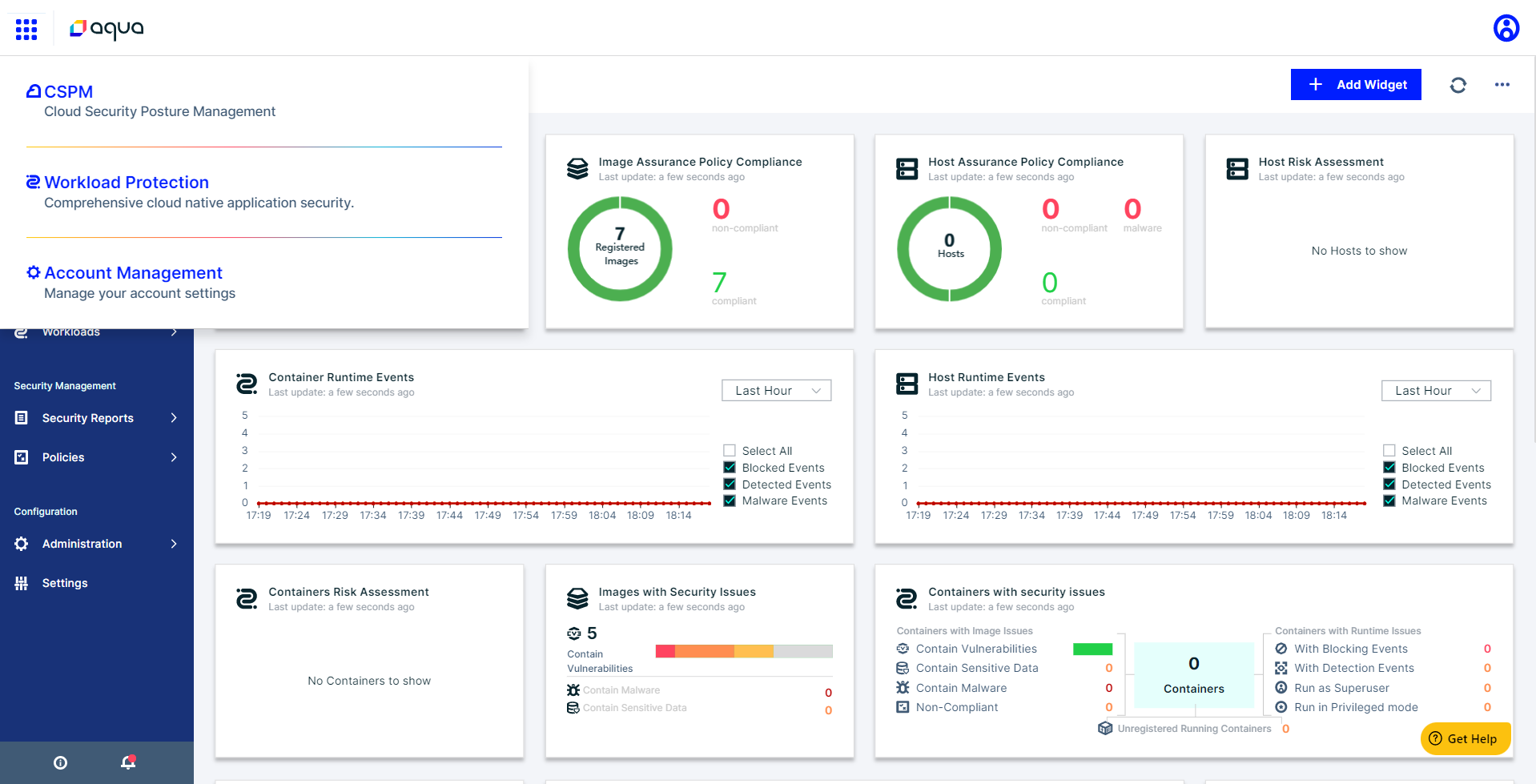 The Aqua Platform is a unified console that can help organizations transition from scanning and visibility to workload protection in cloud-native environments. The platform allows security teams to start with scanning and cloud security posture management (CSPM) capabilities and then add in sandboxing capabilities and workload protection as needed. The Aqua Platform is scalable and available in a Software as a Service or self-hosted deployment format. Image courtesy of Aqua Security
The Aqua Platform is a unified console that can help organizations transition from scanning and visibility to workload protection in cloud-native environments. The platform allows security teams to start with scanning and cloud security posture management (CSPM) capabilities and then add in sandboxing capabilities and workload protection as needed. The Aqua Platform is scalable and available in a Software as a Service or self-hosted deployment format. Image courtesy of Aqua Security
Find out more at www.aquasecurity.com
BitTrap
Uses Cryptocurrency to Identify Cyberattackers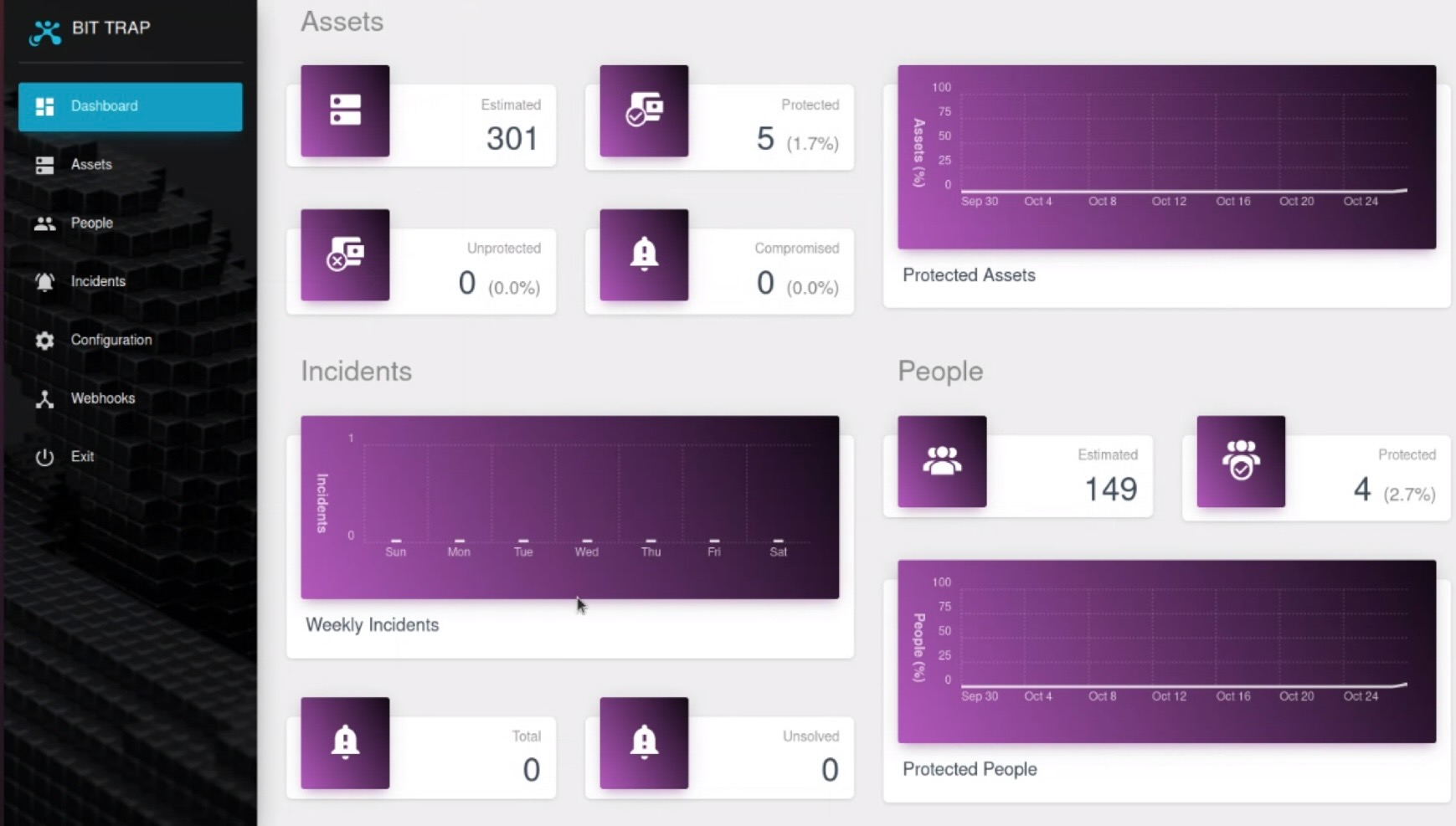
BitTrap employs a blockchain-based cybersecurity solution that leverages attackers’ motivations to provide singular detection capabilities. The BitTrap solution deploys a network of wallets in every endpoint or cloud instance. Each wallet contains a risk-adjusted bounty of cryptocurrency assets, the amounts of which are calibrated based on research from the BitTrap Attacker Behavioral Labs aiming to ensure the wallet will capture an attacker’s attention. Collecting the bounty triggers an incident-response operation that alerts the organization of the breach, allowing them to mitigate damage or loss. Image courtesy of BitTrap
Find out more at www.bittrap.com
BlackBerry Limited
Protects Businesses From Mobile Cyberattacks
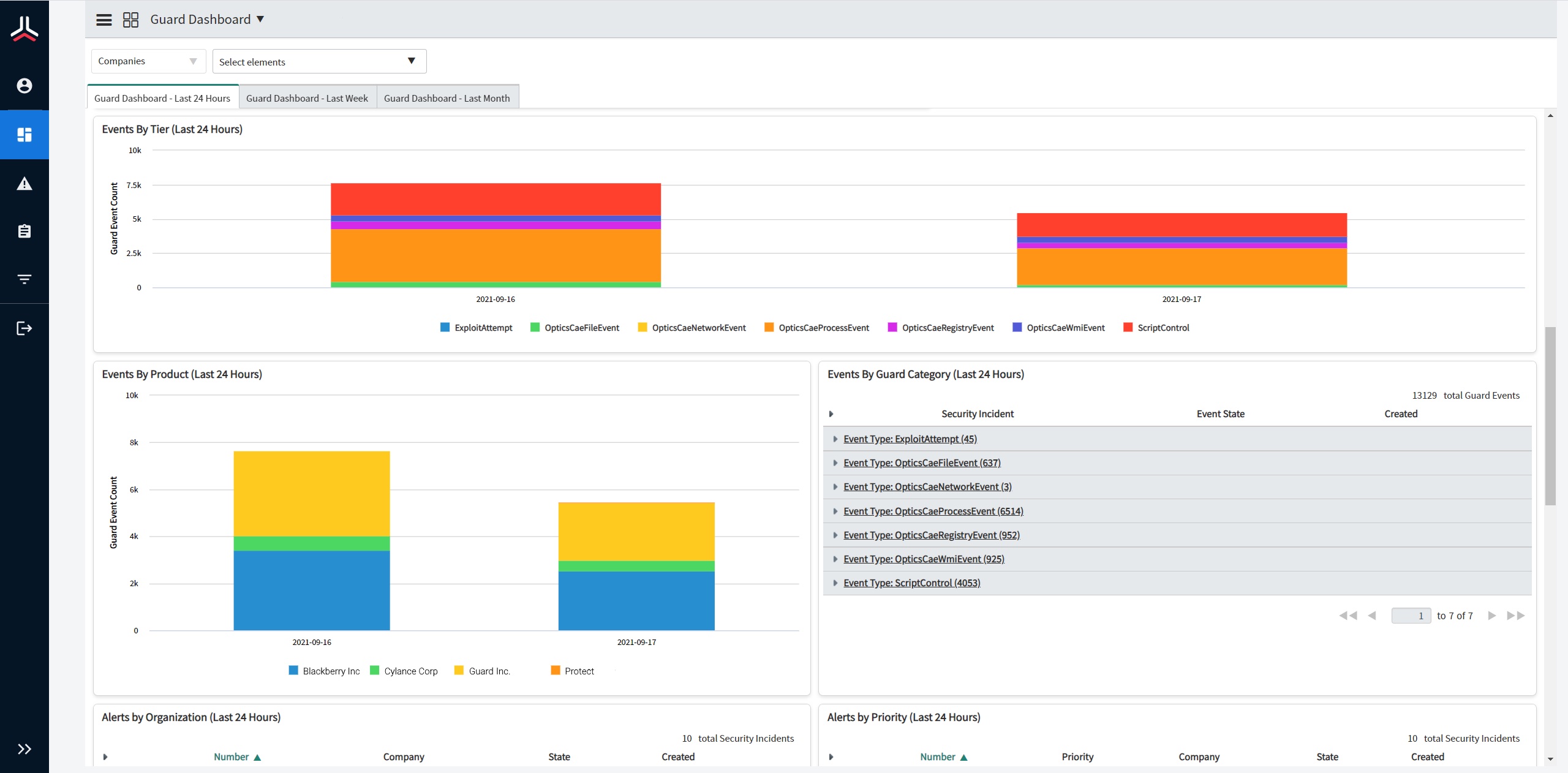
BlackBerry Limited has updated its BlackBerry Guard 2.0 solution, a managed detection and response service, to include artificial intelligence (AI)-powered mobile threat defense, user behavior risk analytics and network analytics technology. BlackBerry Guard 2.0 is a subscription-based managed service that leverages security experts and the Cylance AI platform for threat protection, detection and response. The BlackBerry Guard 2.0 includes a user and analyst portal, multi-regional support and data insights gathered from BlackBerry Protect Mobile, BlackBerry Gateway and BlackBerry Persona for visibility across an organization’s endpoint ecosystem. Image courtesy of BlackBerry
Find out more at www.blackberry.com
Code42
Educates Security Teams and Organizations on Insider Risk
Code42 Instructor is an insider risk education solution that focuses on the creation of holistic, security-oriented cultures. The solution delivers actionable, hyper-targeted lessons on insider risk to end users. Code42 Instructor can be used directly with Code42 Incydr to decrease accidental risk with situational guidance relevant to specific end users at the moment of impact. The education solution builds upon the principle that every organization has a different risk tolerance. By aligning security teams’ responses to risky employee behavior with organizational risk tolerance, Code42 can help reduce alert fatigue and improve the scalability of automated responses. Image courtesy of Code42
Find out more at www.code42.com
Gigamon
Focuses Threat Intelligence in SOCs
ThreatINSIGHT Guided-SaaS NDR (network detection and response) aims to improve security operations center (SOC) effectiveness and reduce analyst burnout. ThreatINSIGHT can increase network visibility, aid with tool maintenance, and provide user support to information technology (IT) and security practitioners in SOCs. The network detection and response technology aims to deliver guided visibility to adversary network activity not observable by EDRs and SIEMs via the Security as a Service software. Image courtesy of Gigamon
Find out more at www.gigamon.com
Jamf
Notifies Apple Users of Threats to Devices
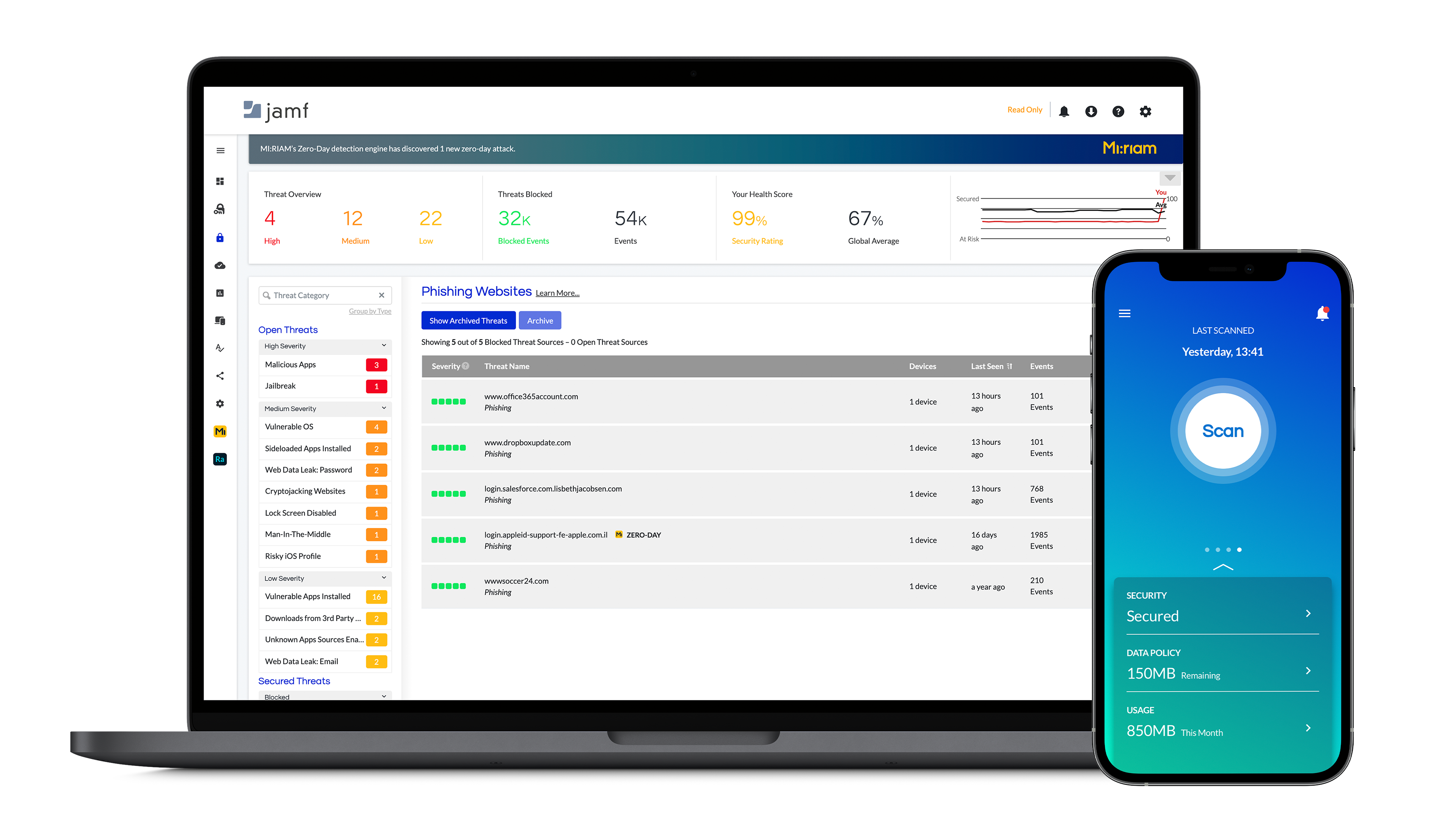 Jamf Threat Defense is a mobile security solution that can protect endpoints from being compromised through mobile threat detection and zero-day phishing prevention with a web-based dashboard for real-time notifications and remediation. Threat Defense includes in-network protection, aiming to block phishing sites and malicious domains before devices are impacted. The security solution is compatible with any device or workplace ownership model, including BYOD. Image courtesy of Jamf
Jamf Threat Defense is a mobile security solution that can protect endpoints from being compromised through mobile threat detection and zero-day phishing prevention with a web-based dashboard for real-time notifications and remediation. Threat Defense includes in-network protection, aiming to block phishing sites and malicious domains before devices are impacted. The security solution is compatible with any device or workplace ownership model, including BYOD. Image courtesy of Jamf
Find out more at www.jamf.com
Quantum
Stores Inactive Data
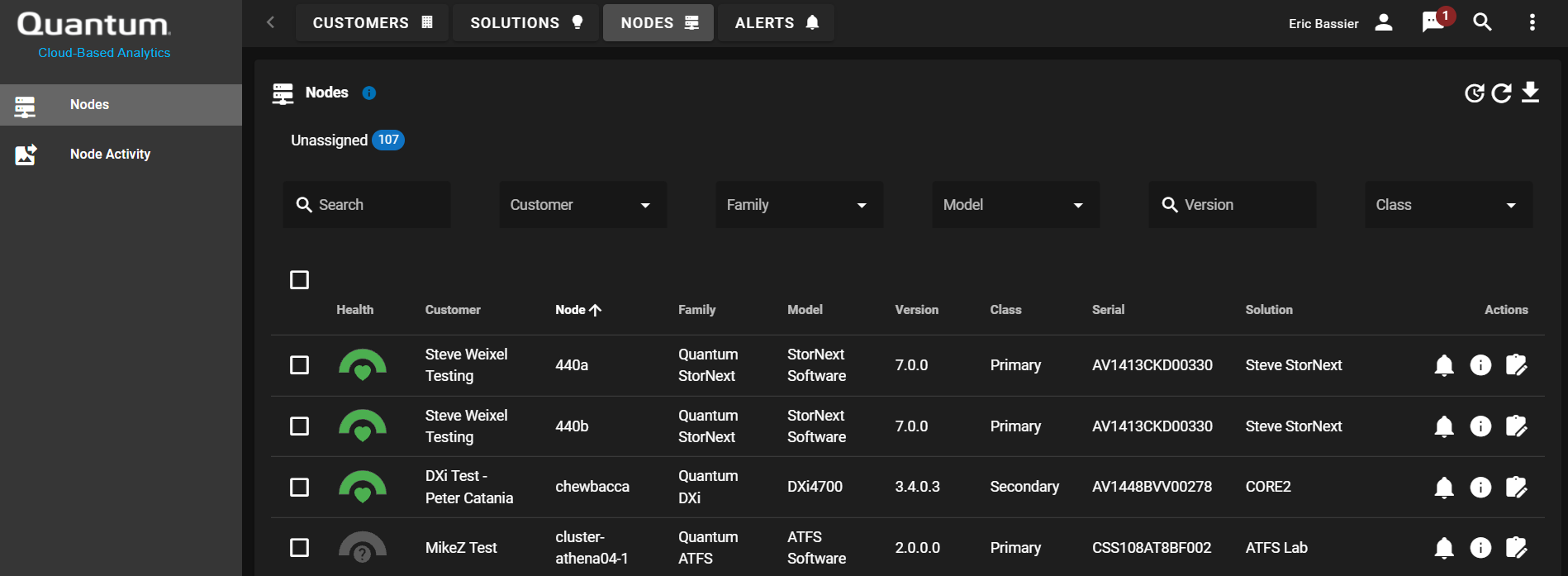
ActiveScale Cold Storage combines object storage software with two-dimensional erasure coding and Quantum Scalar tape storage. ActiveScale Cold Storage introduces patent-pending two-dimensional erasure coding (2D EC) software, which encodes data within and across tapes, tape drives, tape libraries and geo-dispersed data centers and can improve data access performance, durability and storage efficiency. The software can be deployed as a fully managed service at the customer’s data center, a third-party data center or at a combination of the two to build geo-dispersed, hybrid cloud archive storage. Image courtesy of Quantum
Find out more at www.quantum.com
NTT Ltd.
Monitors Threats to AWS Applications
NTT Ltd.’s Cyber Threat Sensor AI (CTS-AI) ensures scalable security for user applications and workloads hosted on Amazon Web Services (AWS) through a mobile application. CTS-AI is an NDR solution developed to protect AWS applications and data directly in the cloud. The solution includes human-validated threat intelligence scanning internet traffic and curating threat data from over 100 intelligence and 50 partner feeds. Image courtesy of NTT Ltd.
Find out more at hello.global.ntt
Orion Labs
Adapts Monitoring and Communication Platform to Many Deployment Methods
 Orion Labs’ voice-first monitoring and collaboration platform is available with three deployment methods to fit each user’s business needs. The first method, Orion-Hosted Deployment, uses Orion’s Engineering and Product teams to manage the hosting, maintenance and implementation of Orion software via AWS so organizations can scale the solution quickly with minimal friction. The second method, Private SaaS Deployment, allows enterprises to integrate Orion software with different cloud environments and still receive support from Orion’s Engineering and Product teams. Orion’s private SaaS deployment aims to allow organizations to meet logging, audit or regulatory compliance requirements. The third method, On-Premise Deployment, uses local servers and air-gapped options with support from Orion. The on-premise deployment supports organizations with limited connectivity or a requirement for complete control of all aspects of their Orion deployment. Image courtesy of Orion Labs
Orion Labs’ voice-first monitoring and collaboration platform is available with three deployment methods to fit each user’s business needs. The first method, Orion-Hosted Deployment, uses Orion’s Engineering and Product teams to manage the hosting, maintenance and implementation of Orion software via AWS so organizations can scale the solution quickly with minimal friction. The second method, Private SaaS Deployment, allows enterprises to integrate Orion software with different cloud environments and still receive support from Orion’s Engineering and Product teams. Orion’s private SaaS deployment aims to allow organizations to meet logging, audit or regulatory compliance requirements. The third method, On-Premise Deployment, uses local servers and air-gapped options with support from Orion. The on-premise deployment supports organizations with limited connectivity or a requirement for complete control of all aspects of their Orion deployment. Image courtesy of Orion Labs
Find out more at orionlabs.io
Salt Security
Secures GraphQL APIs Using AI and Machine Learning
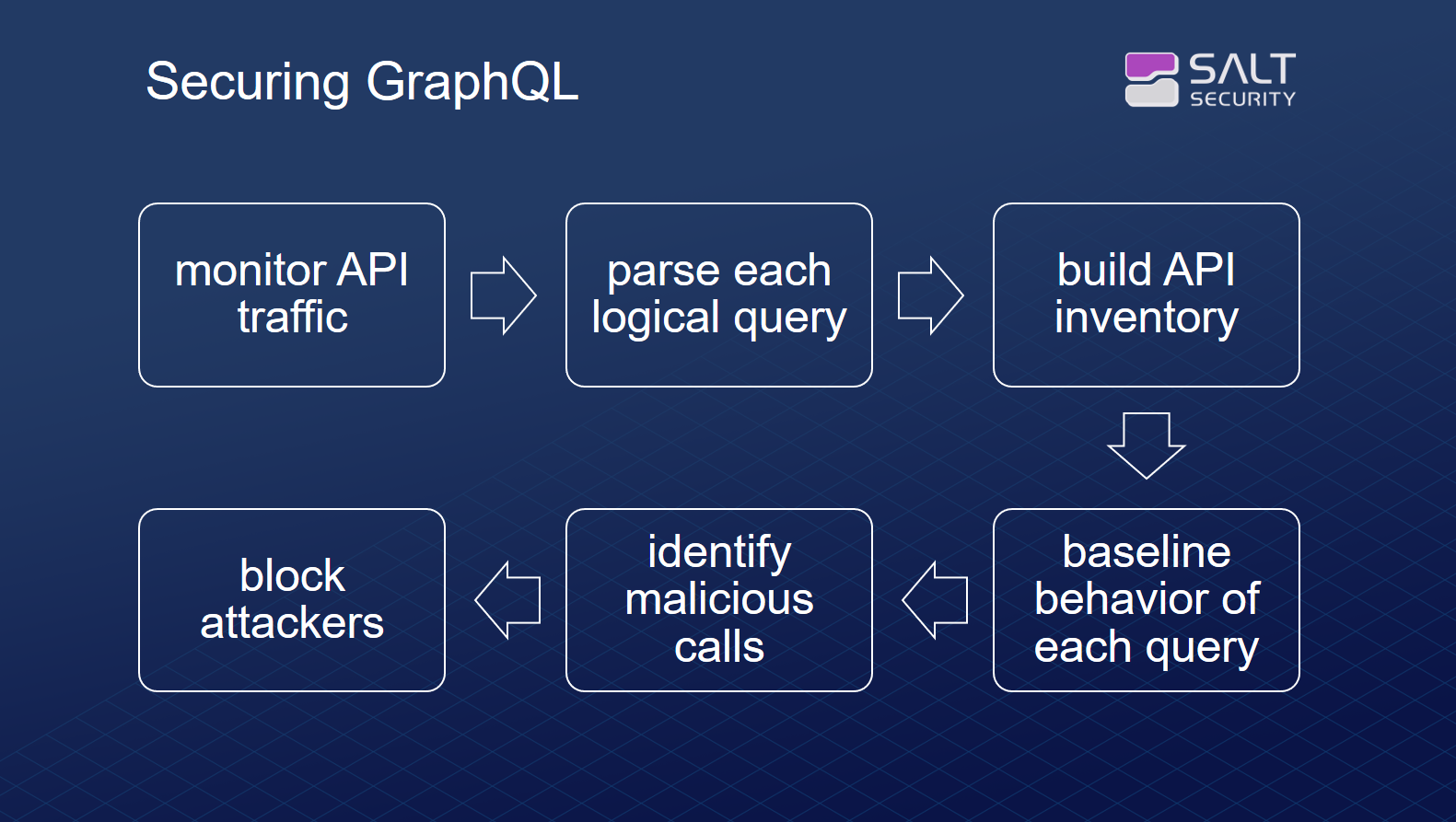 Salt Security has updated its API Protection Platform to secure GraphQL (application program interfaces) APIs. This update can enable users of GraphQL, an open-source query language used to build APIs, to
Salt Security has updated its API Protection Platform to secure GraphQL (application program interfaces) APIs. This update can enable users of GraphQL, an open-source query language used to build APIs, to
mitigate data exposure and eliminate vulnerabilities at their source. Utilizing its patented AI- and machine learning-based big data engine, the platform baselines legitimate system behavior while aiming to effectively identify attackers in real time, stopping bad actors while they are still performing reconnaissance. The Salt Security API Protection Platform integrates with DevOps and SecOps tools such as Slack and SIEM platforms to ensure that remediation details are routed to the right development team. Image courtesy of Salt Security
Find out more at salt.security
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






