Product Spotlight
RSA Conference 2022 product preview
From security policy building to automated cybersecurity defense, Security magazine spotlights solutions from the 2022 RSA Conference.

Axonius
Manages Enterprise Software as a Service Platforms
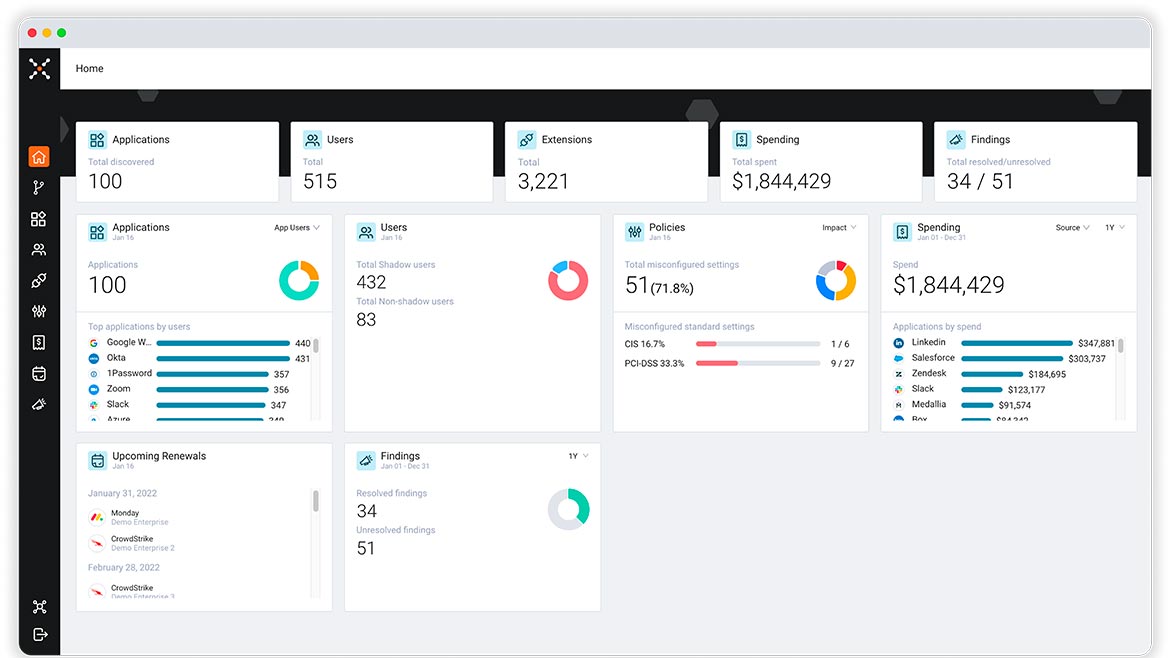
Axonius SaaS Management can help security, information technology (IT), finance and risk teams control the complexity, cost and risk of Software as a Service (SaaS). The management platform uses adapters (application programming interface [API] connections to data sources) and discovery tools to create an inventory of the SaaS applications, permissions and data flow involved in an enterprise. The solution aims to find both the SaaS applications known to and sanctioned by organizations as well as shadow and unmanaged apps. Image courtesy of Axonius
Find out more at www.axonius.com
BigID
Identifies Sensitive Cloud Data
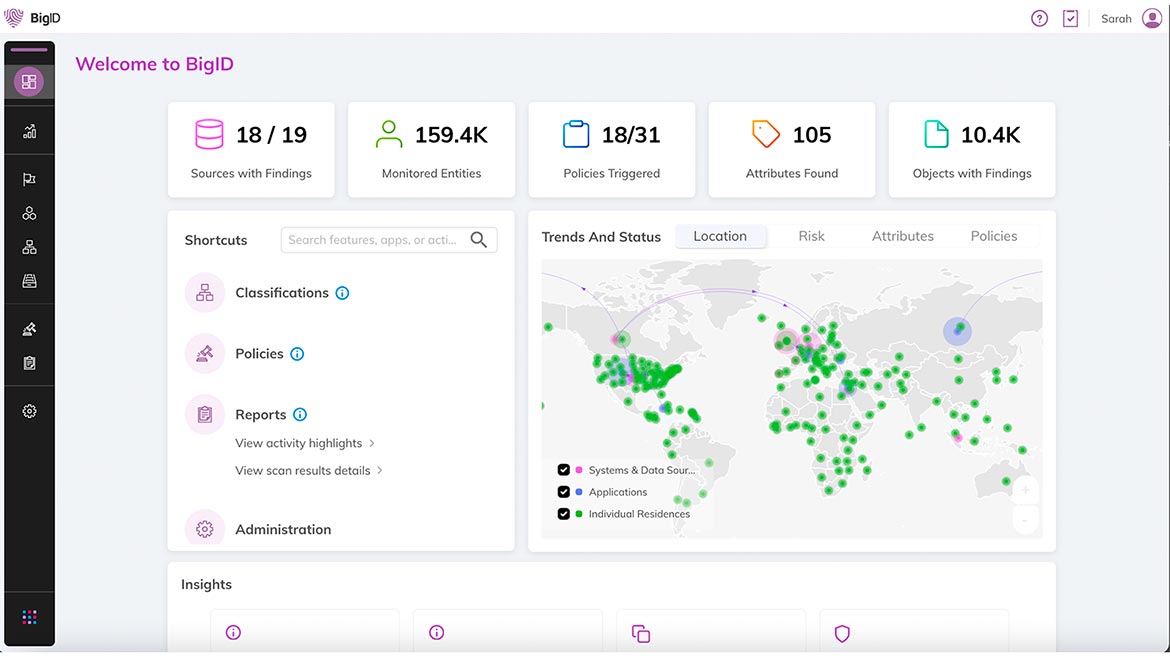 BigID’s Automatic Discovery apps aim to find sensitive and personal data stored in the cloud. The Automatic Discovery apps are designed for cloud platforms, including Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP). The applications can discover data sources in the cloud and can reduce the need for manual efforts to search for, configure and connect data sources across an enterprise’s cloud environment. These apps allow for regular and repeated scanning of AWS and other cloud platforms. Image courtesy of BigID
BigID’s Automatic Discovery apps aim to find sensitive and personal data stored in the cloud. The Automatic Discovery apps are designed for cloud platforms, including Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP). The applications can discover data sources in the cloud and can reduce the need for manual efforts to search for, configure and connect data sources across an enterprise’s cloud environment. These apps allow for regular and repeated scanning of AWS and other cloud platforms. Image courtesy of BigID
Find out more at www.bigid.com
Cobalt
Advises Security Leaders on Cybersecurity Strategy
Cobalt’s Professional Services can aid cybersecurity professionals throughout the penetration testing process. The solution includes Pentest Program Management, which partners users with security consultants to develop penetration testing programs; Advisory Services, which connects enterprise security leaders with cybersecurity advisors to field strategic and technical questions; and Phishing Engagements, a program that trains enterprise organizations how to recognize and protect themselves from a phishing attack. Image courtesy of gopixa / iStock / Getty Images Plus
Find out more at www.cobalt.io
Confluera
Automatically Detects Cyberattack Signs
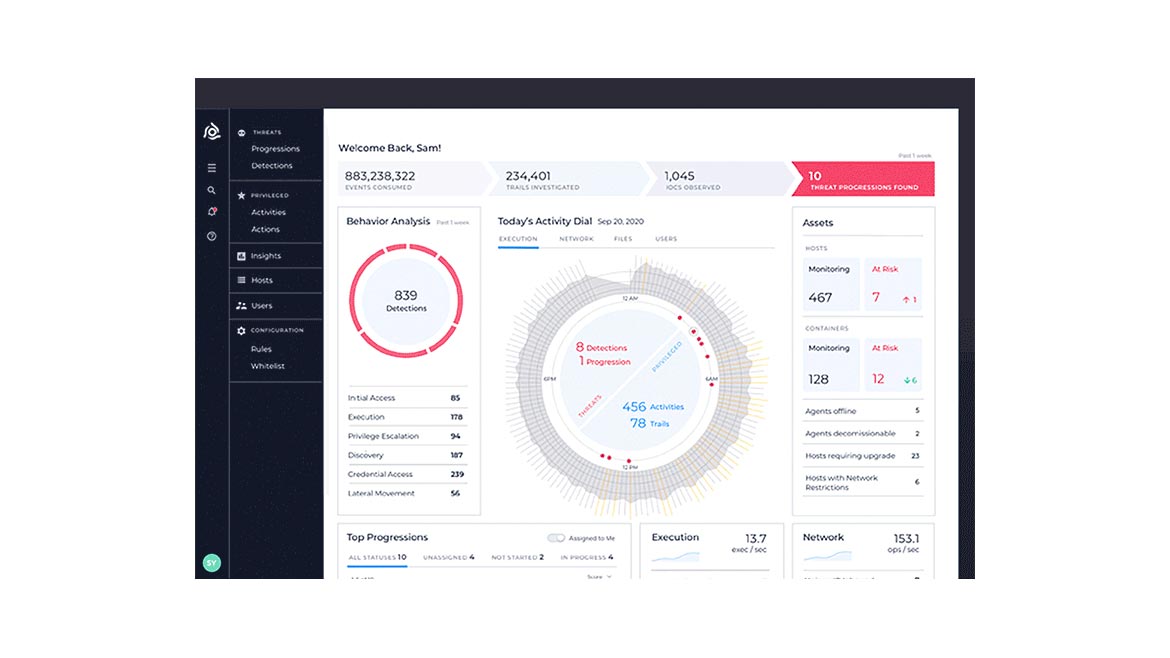
The Cloud eXtended Detection and Response (CxDR) solution from Confluera can help organizations gain visibility into active attack progressions and reduce the average time to detect and mitigate advanced cyberattacks. The updated CxDR solution extends cloud-native threat storyboarding capabilities to support Microsoft Azure, GCP, AWS and other security solutions. Image courtesy of Confluera
Find out more at www.confluera.com
CyberGRX
Predicts Third-Party Vendor Risk
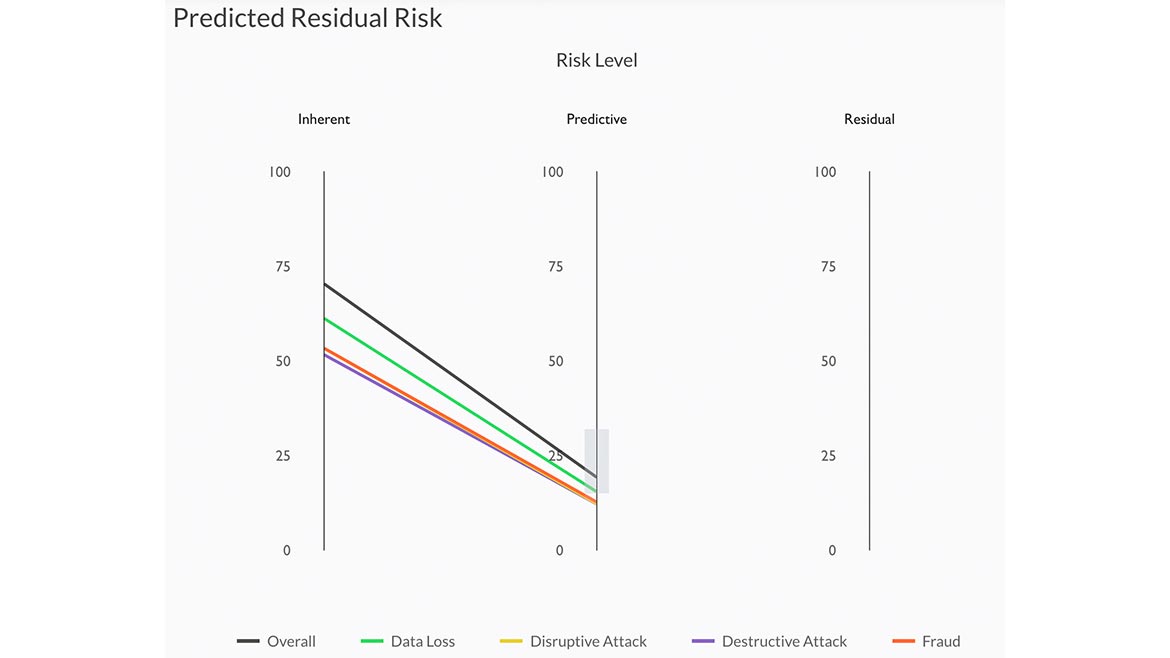 CyberGRX’s Predictive Risk Profile uses standardized data within the firm’s Risk Exchange platform and applies machine learning and data analytics to anticipate how third parties within a company’s vendor ecosystem will respond to a detailed security assessment questionnaire. With Predictive Risk Profile, users can monitor and analyze third-party risk for improved risk management. Users receive insights across their portfolio of vendors to help enable transparency and address control gaps and risk remediation strategies. Image courtesy of CyberGRX
CyberGRX’s Predictive Risk Profile uses standardized data within the firm’s Risk Exchange platform and applies machine learning and data analytics to anticipate how third parties within a company’s vendor ecosystem will respond to a detailed security assessment questionnaire. With Predictive Risk Profile, users can monitor and analyze third-party risk for improved risk management. Users receive insights across their portfolio of vendors to help enable transparency and address control gaps and risk remediation strategies. Image courtesy of CyberGRX
Find out more at www.cybergrx.com
Fortanix
Secures Artificial Intelligence Models
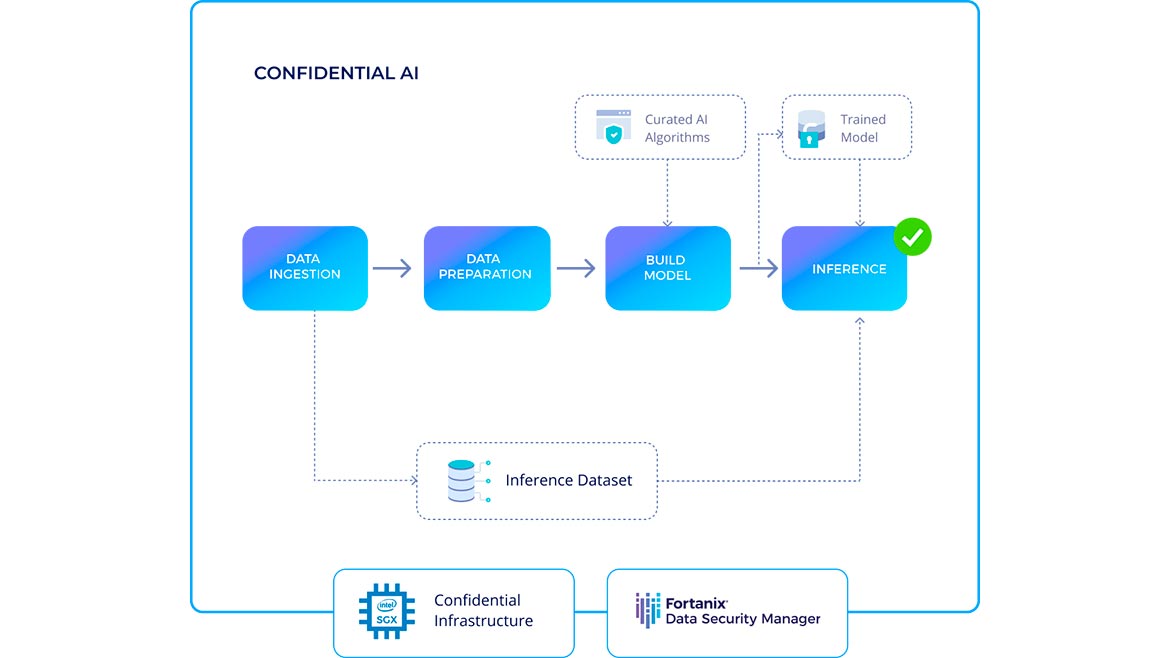
Fortanix’s Confidential AI is a software and infrastructure subscription service that leverages computing technology to help secure the use of private data without compromising privacy and compliance. With Confidential AI, data teams in regulated, privacy-sensitive industries, such as healthcare and financial services, can utilize private data to develop and deploy artificial intelligence (AI) models. The solution helps to provide protection for the intellectual property of developed models with secure infrastructure. Image courtesy of Fortanix
Find out more at www.fortanix.com
NCP
Keeps Confidential Enterprise Data Secure
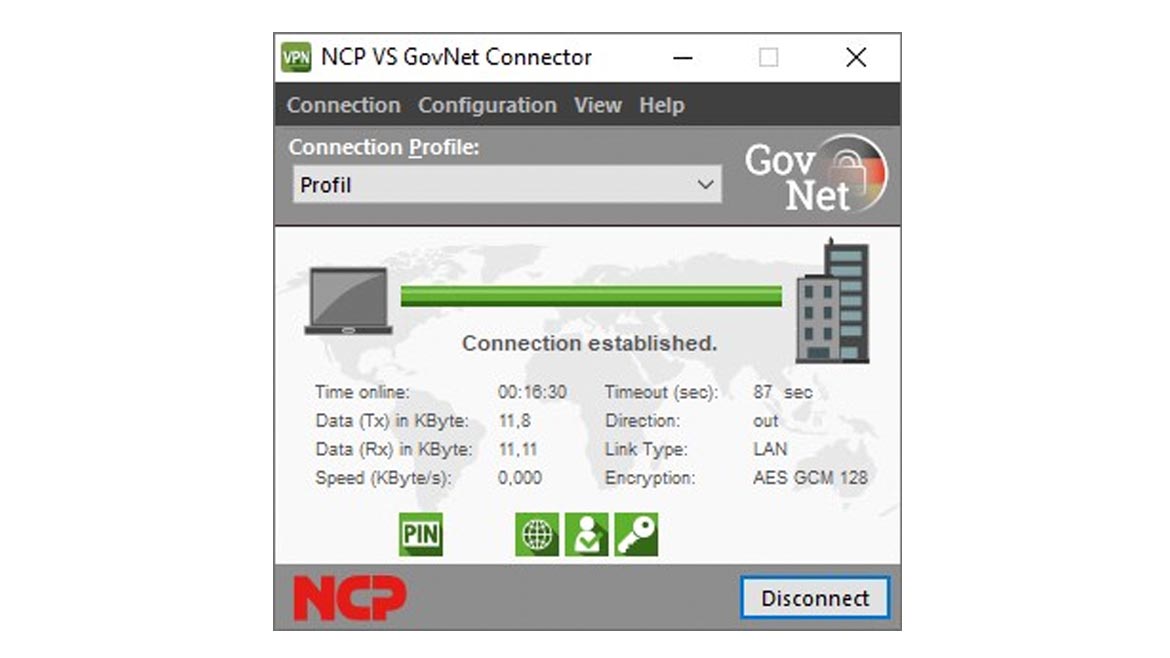 Version 2.10 of NCP’s VS GovNet Connector is designed for use in ministries, public authorities and enterprise organizations operating in European countries. The VS GovNet Connector includes secure hotspot login and Friendly Net Detection (FND). The hotspot login aims to directly connect traveling employees to a corporate network or a reduced-function web browser. FND uses an accessible server to detect whether the user is in a secure or unsecure network. Depending on the network, the FND function activates the corresponding firewall rules. The solution offers biometric authentication and virtual private network (VPN) Path Finder Technology. Image courtesy of NCP
Version 2.10 of NCP’s VS GovNet Connector is designed for use in ministries, public authorities and enterprise organizations operating in European countries. The VS GovNet Connector includes secure hotspot login and Friendly Net Detection (FND). The hotspot login aims to directly connect traveling employees to a corporate network or a reduced-function web browser. FND uses an accessible server to detect whether the user is in a secure or unsecure network. Depending on the network, the FND function activates the corresponding firewall rules. The solution offers biometric authentication and virtual private network (VPN) Path Finder Technology. Image courtesy of NCP
Find out more at www.ncp-e.com
NTT Application Security
Integrates Security Throughout Software Development
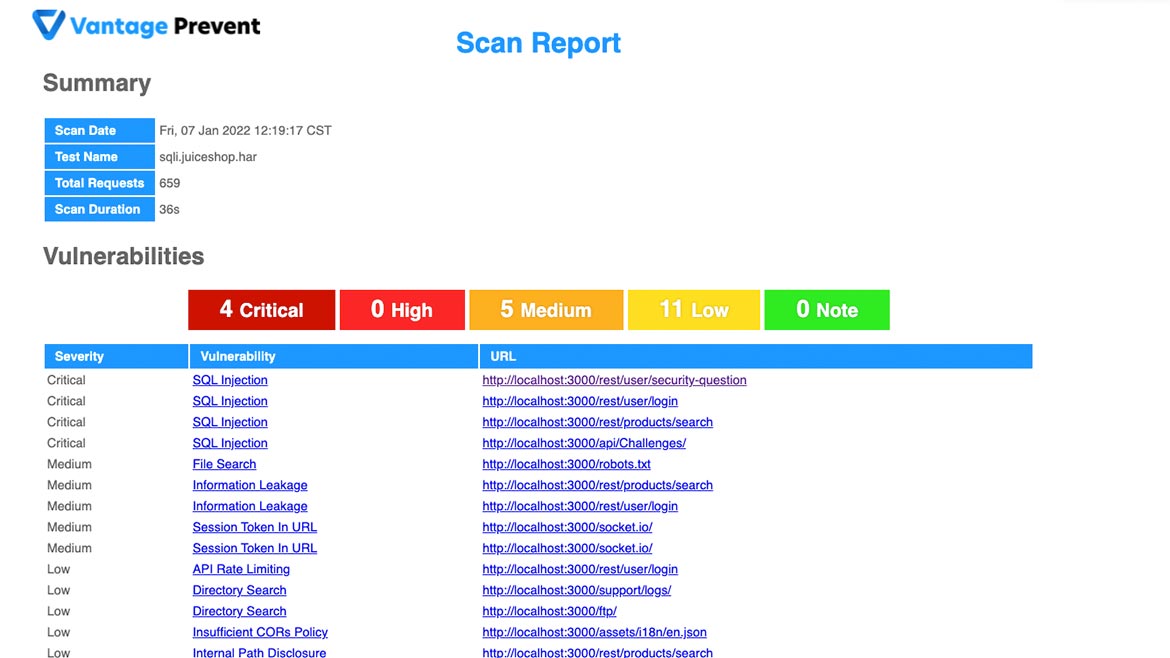
NTT Application Security’s Vantage Prevent helps enable enterprises to conduct dynamic application security testing (DAST) at each phase of the application development cycle and prevent exploitable vulnerabilities from reaching production. The solution leverages developers’ functional and quality assurance tests to identify security risks in their web applications and APIs. Vantage Prevent also allows software engineers to automate security testing, so security teams can assess reported vulnerabilities before they are deployed into production. Image courtesy of NTT Application Security
Find out more at www.whitehatsec.com
Cambridge Quantum
Creates Randomized Encryption Keys
 Quantum Origin derives cryptographic keys using the output of a quantum computer to ensure data is protected at a foundational level against evolving attacks. The keys generated by Cambridge Quantum’s Quantum Origin are based on quantum randomness and can be integrated into existing systems. The protocol relies on “entanglement,” a feature of quantum mechanics. The cloud-hosted platform uses the unpredictable nature of quantum mechanics to generate cryptographic keys seeded with quantum randomness from Quantinuum’s H-Series quantum computers, powered by Honeywell. Image courtesy of Cambridge Quantum
Quantum Origin derives cryptographic keys using the output of a quantum computer to ensure data is protected at a foundational level against evolving attacks. The keys generated by Cambridge Quantum’s Quantum Origin are based on quantum randomness and can be integrated into existing systems. The protocol relies on “entanglement,” a feature of quantum mechanics. The cloud-hosted platform uses the unpredictable nature of quantum mechanics to generate cryptographic keys seeded with quantum randomness from Quantinuum’s H-Series quantum computers, powered by Honeywell. Image courtesy of Cambridge Quantum
Find out more at www.cambridgequantum.com
Revelstoke
Automates Security Operations Centers
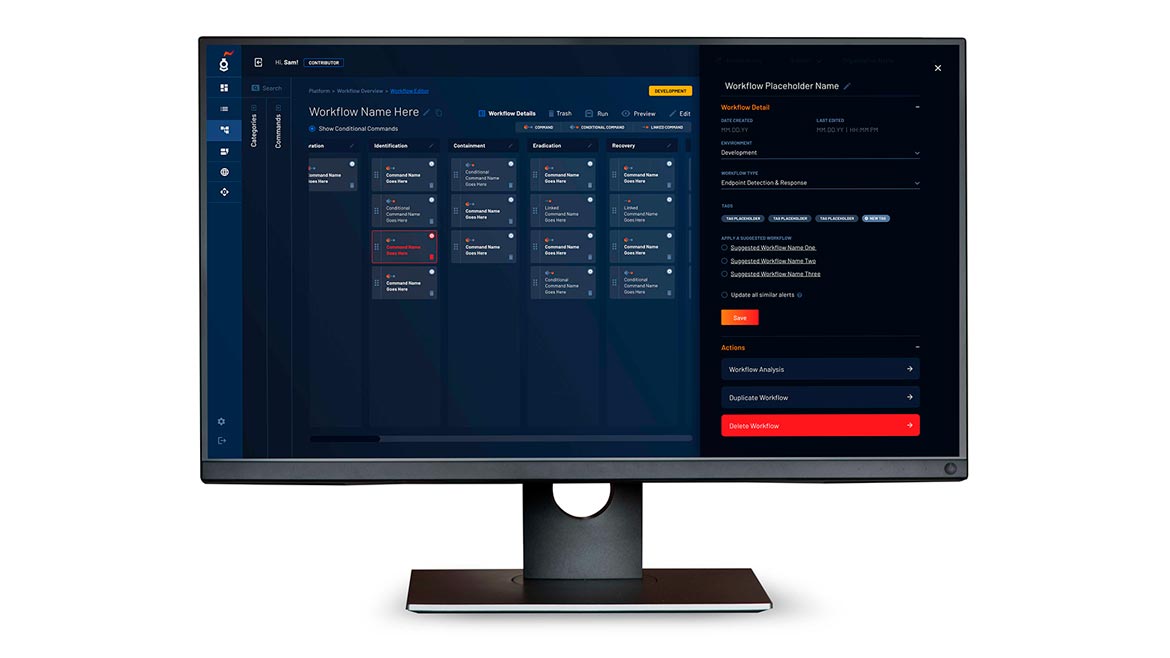
The Revelstoke Unified Data Layer automates analysis in security orchestration, automation and response (SOAR) solutions in security operations centers (SOCs). The Unified Data Layer aims to eliminate software development needs and manage security incidents in SOCs. The no-code/low-code solution can allow chief information security officers (CISOs) to automate certain processes and maintain manual control over others. Image courtesy of Revelstoke
Find out more at www.revelstoke.io
SPHERE
Gives Visibility Into Privileged Access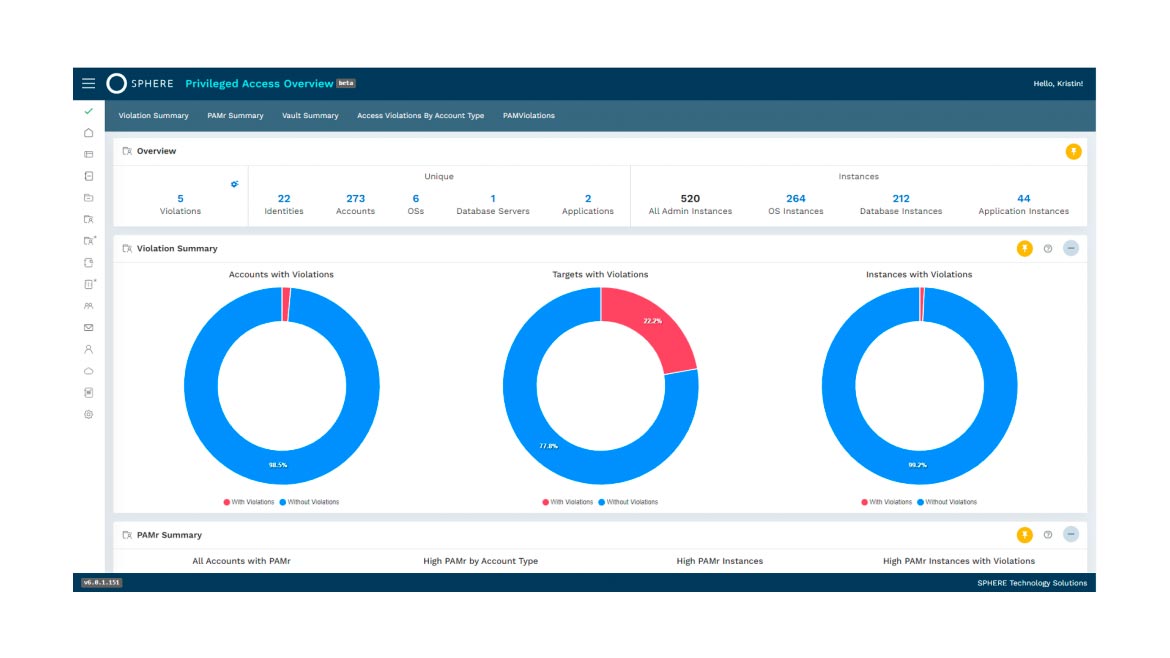
SPHEREboard 6.0 redesigns SPHERE’s access management solution to help give security professionals visibility into privileged access across an organization’s assets. Users can utilize the solution to manage UNIX, Windows, applications and privileged access. The update includes controls, parameters and a redesign of the SPHEREboard dashboard and user interface. The update brings a new version of the Privileged Access Management module to help understand user environments and identify immediate risks. Image courtesy of SPHERE
Find out more at www.sphereco.com
Tufin
Helps Develop Security Policies
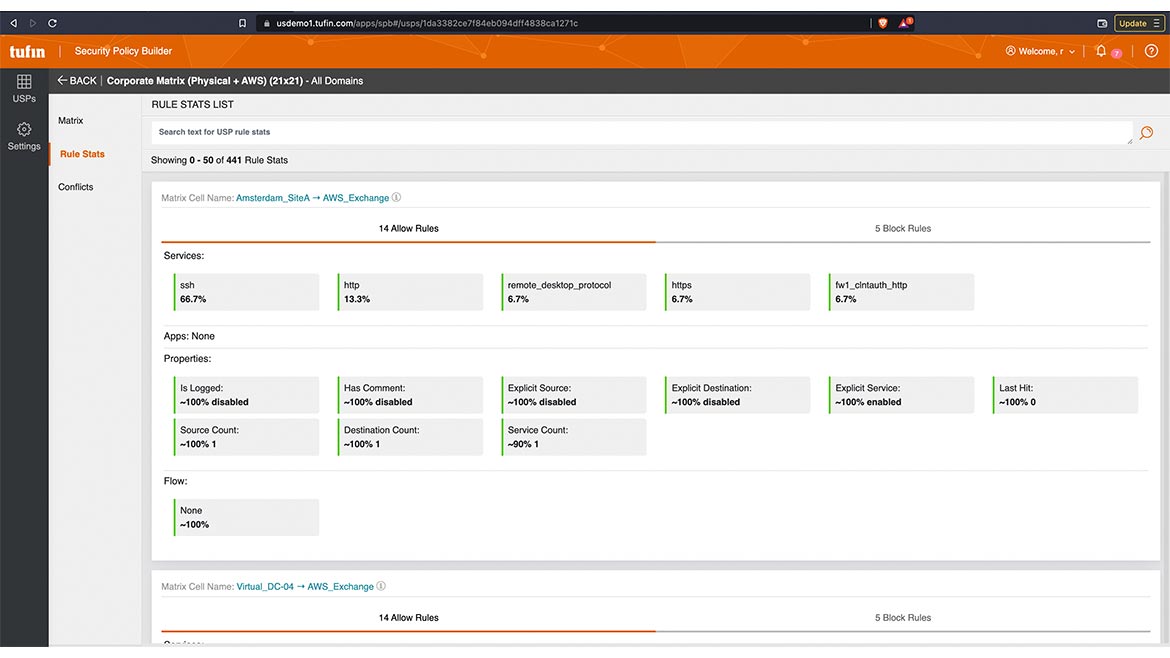 Tufin’s Security Policy Builder (SPB) App automates the design of corporate security network and cloud security access policies across the hybrid environment. Integrating with the firm’s SecureTrack solution, the SPB App can operationalize security policies to identify the exposed attack surface for prioritized response based on a company’s definition of risk to the business to help users track compliance assurance and reduce breach likelihood. Image courtesy of Tufin
Tufin’s Security Policy Builder (SPB) App automates the design of corporate security network and cloud security access policies across the hybrid environment. Integrating with the firm’s SecureTrack solution, the SPB App can operationalize security policies to identify the exposed attack surface for prioritized response based on a company’s definition of risk to the business to help users track compliance assurance and reduce breach likelihood. Image courtesy of Tufin
Find out more at www.tufin.com
VMware
Detects Cyberattacks and Suggests Future Action
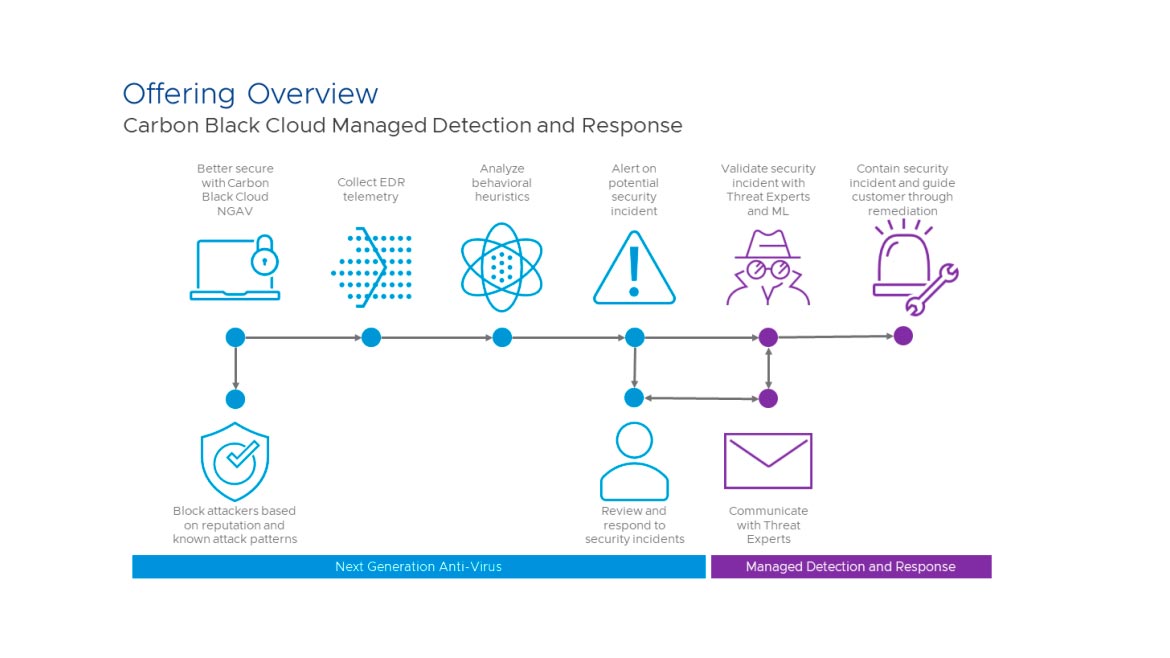 VMware’s Carbon Black Cloud Managed Detection and Response (MDR) for endpoints and workloads aims to give security leaders insight into cyberattacks along with recommendations for remedying policy changes. VMware analysts monitor MDR user environments, offering monitoring, alert triage and threat intelligence. The analysts can notify IT and security teams via email of threats and suggest policy changes to address critical alerts and incident investigations. Image courtesy of VMware
VMware’s Carbon Black Cloud Managed Detection and Response (MDR) for endpoints and workloads aims to give security leaders insight into cyberattacks along with recommendations for remedying policy changes. VMware analysts monitor MDR user environments, offering monitoring, alert triage and threat intelligence. The analysts can notify IT and security teams via email of threats and suggest policy changes to address critical alerts and incident investigations. Image courtesy of VMware
Find out more at www.vmware.com
ZeroFox
Alerts Security to Malicious IT Infrastructure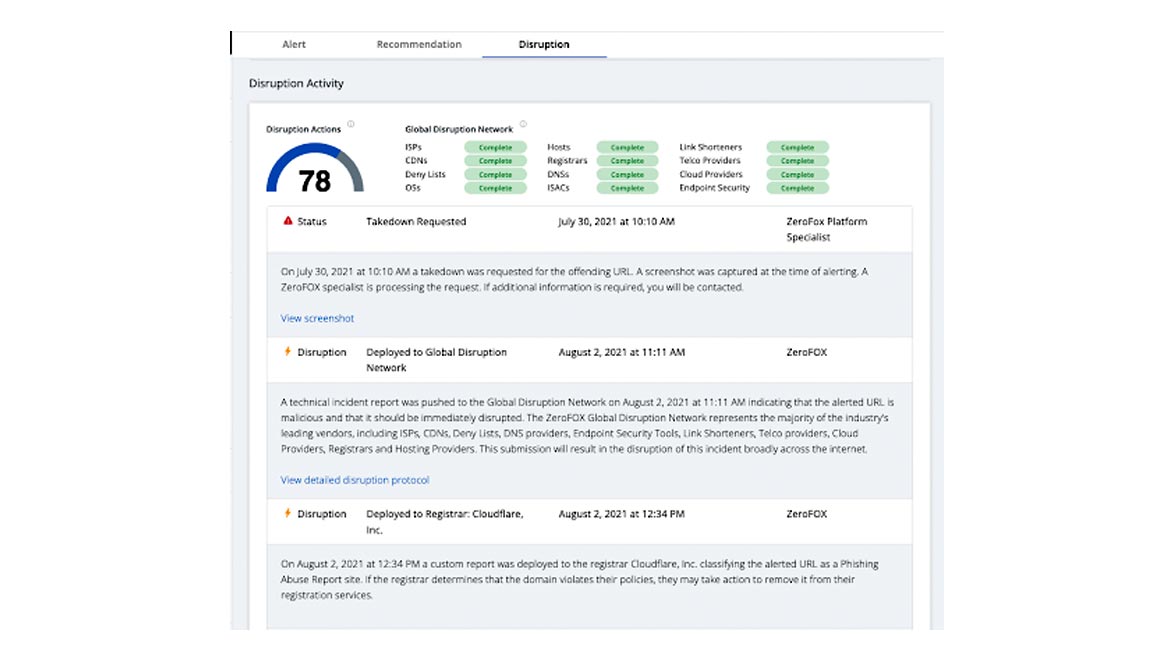
ZeroFox’s Adversary Disruption service can automate the dismantlement of malicious infrastructure, content, sites and bot accounts required to conduct external cyberattacks. The service aims to identify cyberattack indicators collected across validated threats and distribute them to various third-party providers and endpoint security platforms. Image courtesy of ZeroFox
Find out more at www.zerofox.com
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





