Product Spotlight
Product spotlight on threat monitoring and risk assessment solutions

Security leaders rely on a number of threat and risk assessment monitoring tools and solutions to understand, identify and mitigate threats to the enterprise. From travel risk management to social media monitoring, professionals across the industry can use threat monitoring and risk assessment tools to help define security risks and boost emergency response and threat remediation.
Security magazine spotlights threat monitoring and risk assessment solutions that can help improve security posture at various organizations.
Anvil Group
Benchmarks Travel Risk Management

Global travel and operational risk firm Anvil Group’s online scorecard aims to help organizations benchmark their existing travel risk management program against seven key areas highlighted as critical by ISO 31030, the international standard for travel risk management. These include: understanding their organization’s risk context, managing travel risk effectively, determining preparedness for major incidents, and measuring the engagement of internal stakeholders and travelers with the security program. On completion of the scorecard, responders receive a personalized report containing an overall score and a breakdown of their score against key areas of ISO 31030. The results can serve as an indicator of how well the organization is performing against the standard and help to highlight shortfalls in policies and programs. Image credit RyanJLane / E+ / via Getty Images
Find out more at www.anvilgroup.com
Blackline Safety
Monitors Safety of Lone Workers

Blackline Safety Corp.’s Safety Operations Centre (SOC) is a safety monitoring service that can help with employee protection, especially for lone workers. The in-house safety monitoring service is a cloud-based technology, featuring GPS-enabled safety sensors and Internet of Things (IoT) devices that can connect workers to live monitoring. Additionally, the service enables back and forth information sharing, collecting data such as location tracking and making it possible to determine how often workers travel through high-risk areas. With the platform, enterprises can help reduce and manage safety alerts from lone worker incidents and ensure emergency response protocols are followed. Image courtesy of Blackline Safety
Find out more at www.blacklinesafety.com
Dataminr
Real-time Event and Risk Detection

Dataminr has updated its Dataminr Pulse information discovery platform with rapid response capabilities. The organization has incorporated facets of Krizo’s emergency preparedness software and WatchKeeper’s data revisualization platform into the solution, including the ability to plan for, simulate and activate crisis responses to physical and cyber threats, supply chain disruptions and reputational risks. With the update, capabilities include: geovisualization, which allows users to see layers of data for a holistic view of the risk landscape; collaboration workflows, allowing teams to work cross-functionally and in real-time to manage responses to crises; as well as reporting and analysis to provide stakeholders with business intelligence. Image credit sinology / via Getty Images
Find out more at www.dataminr.com
EasySet
Generates Security Assessments
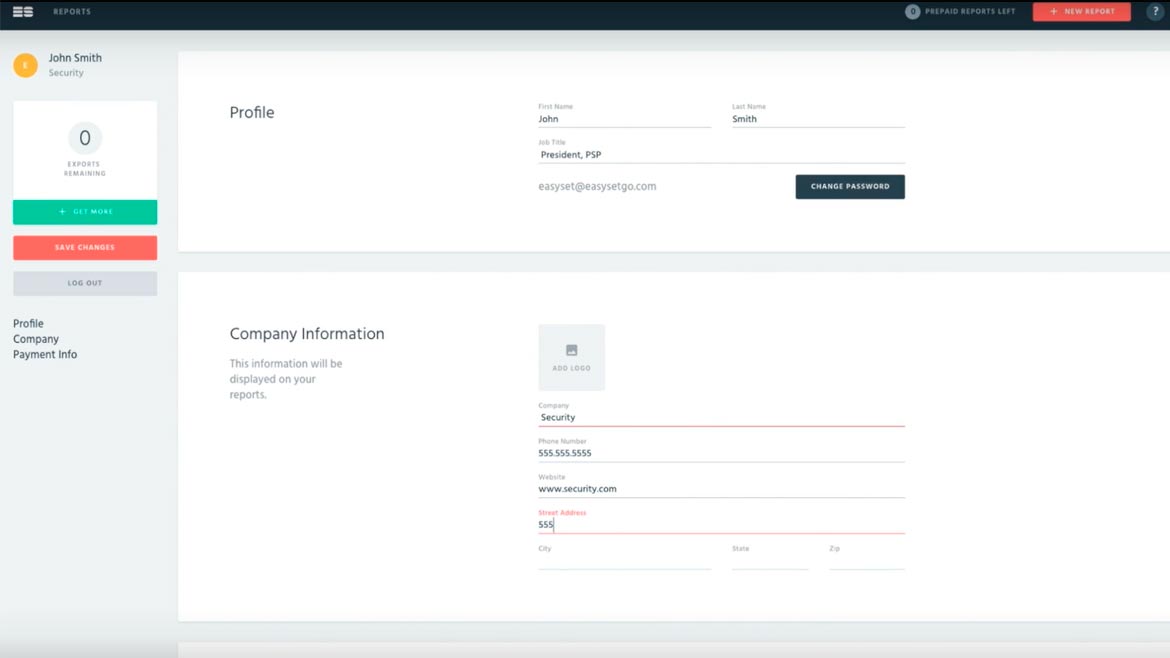
EasySet Risk Analysis helps security leaders write risk assessments and designate risk levels and mitigation priority to vulnerabilities observed onsite, or as it applies to the assessed facility. With the app onsite during a walkthrough, users can take notes and suggest solutions. After users return to the office, they can log in to the desktop dashboard and activate the EasySet Risk Analysis Feature to select a risk level (5 point scale) and a mitigation priority and then apply them to each vulnerability observed to communicate how and where risk resides on a given property. Image courtesy of EasySet
Find out more at www.easysetgo.com
Everbridge
Manages Digital and Physical Events

Everbridge Inc.’s Digital Operations Platform aims to help users with the ability to automate digital service delivery and incident management across teams and toolsets to help improve digital transformation initiatives. In addition, the platform can help organizations assess digital service interruptions, mitigate issues, and improve processes and services. With the platform, organizations can manage digital and physical events through a single pane of glass, streamline resolution across digital operations teams, and protect against major incidents and operational disruption. Image credit everythingpossible / via Getty Images
Find out more at www.everbridge.com
Hakimo
Reduces False Alarms and Tailgating
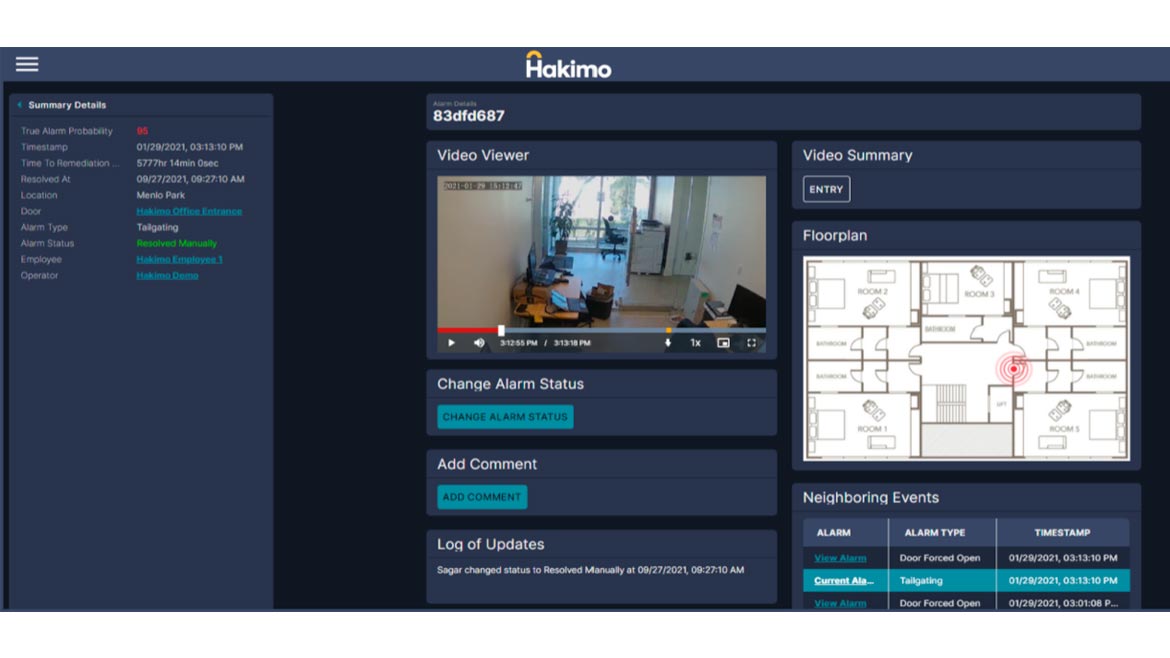
Hakimo Alarm Monitoring 2.0 uses artificial intelligence (AI) to help enterprises solve two problems faced by monitoring stations and Global Security Operations Centers (GSOCs) — access control false alarms and tailgating detection — with the use of existing cameras and video analytics. Powered by deep learning technology, the software helps streamline GSOC workflows by surfacing physical security threats. The platform’s data analytics algorithms also analyze alarms across time and diagnose faulty hardware such as door sensors. The solution provides bidirectional integrations and partnerships with common access control systems. Image courtesy of Hakimo
Find out more at www.hakimo.com
LifeRaft
Monitors Social Media Threats
LifeRaft Navigator is an intelligence platform that helps automate the collection and filtering of data relevant to security operations from social media and deep web sources to provide a suite of investigative tools to explore and validate threats to the enterprise. With Navigator’s newest threat management feature named ‘Dossiers,’ organizations can consolidate intelligence discovery, collection and ongoing management of threat actors, specific events or business entities. Users are able to conduct investigations and organize content with a new user interface launched in conjunction with Dossiers. The user interface allows for simplified threat management and visualization and more navigation specific to security analyst and investigator workflows. Image courtesy of LifeRaft
Find out more at www.liferaft.com
March Networks
Helps Maintain Surveillance Systems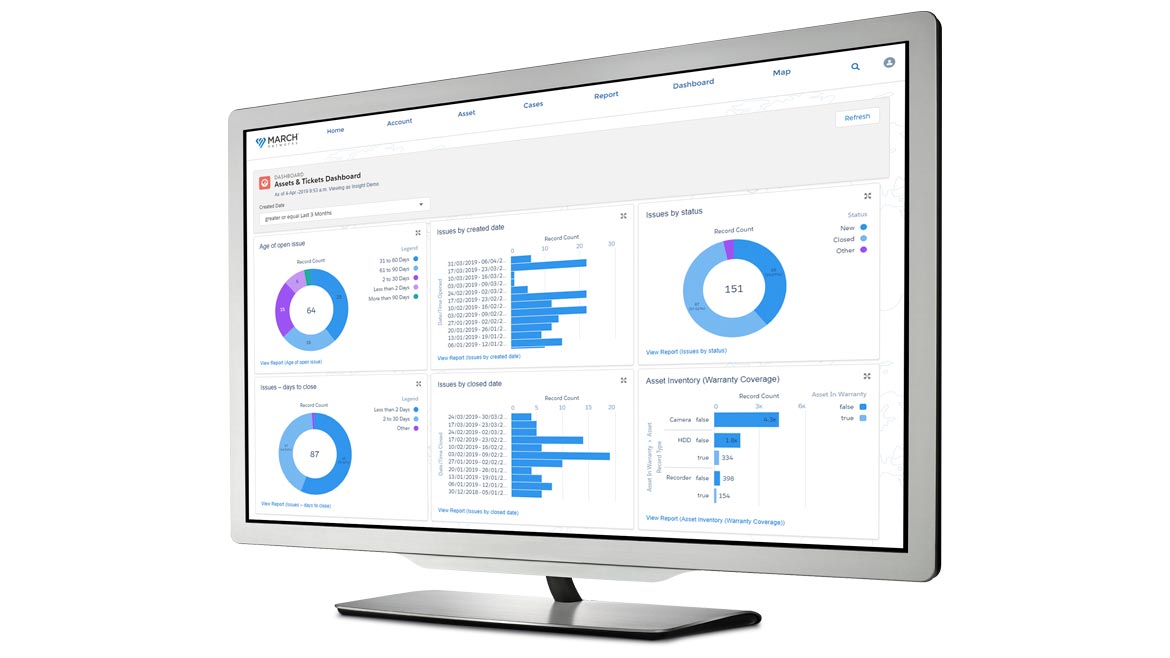
The March Networks Insight Monitoring and Resolution Service is a cloud-based solution that provides users support for their video surveillance systems with remote health monitoring of devices, including recorders, cameras and hard drives, as well as overall network connectivity. Professionals in March Networks’ Network Operations Center (NOC) work with users to remotely monitor network infrastructure, apply software updates, and troubleshoot issues, including dispatching an onsite technician when required. Image courtesy of March Networks
Find out more at www.marchnetworks.com
Ontic
Helps Assess Violence Risk

Ontic’s threat assessment and management offering supports several integrated threat assessment workflows for handling threats. Through its SIGMA workplace threat assessment and WAVR-21 Workplace Assessment of Violence Risk, this offering is designed to ensure organizations follow established protocols for a guided threat assessment and can work consistently for risk mitigation plans and a defensible process. Its threat management program helps establish best practices to conduct threat assessments and make informed decisions to protect people and assets, maintain business continuity, reduce financial harm and protect corporate reputation, through threat assessment training, threat management strategic review, and ongoing case coaching and guidance. Image courtesy of Ontic
Find out more at www.ontic.com
RaySecur
Protects Against Postal Threats
RaySecur’s T-Suite Image Processing Suite for MailSecur scanners produces a high frame rate that enhances realism and sharpens object edges for better detection of trace amounts of white powders and liquids, which comprise the majority of mail threats. With the T-Suite’s SecurTone color palette, the technology helps improve object contrast for more sensitivity, improving object penetration and threat recognition. The technology detects the types of postal threats identified by the U.S. Department of Homeland Security. The solution, for example, can help expedite building lockdown or evacuation and communications to prevent the potential spread of contaminants or smoke. Image courtesy of RaySecur
Find out more at www.raysecur.com
RiskWatch
Risk Assessments for Compliance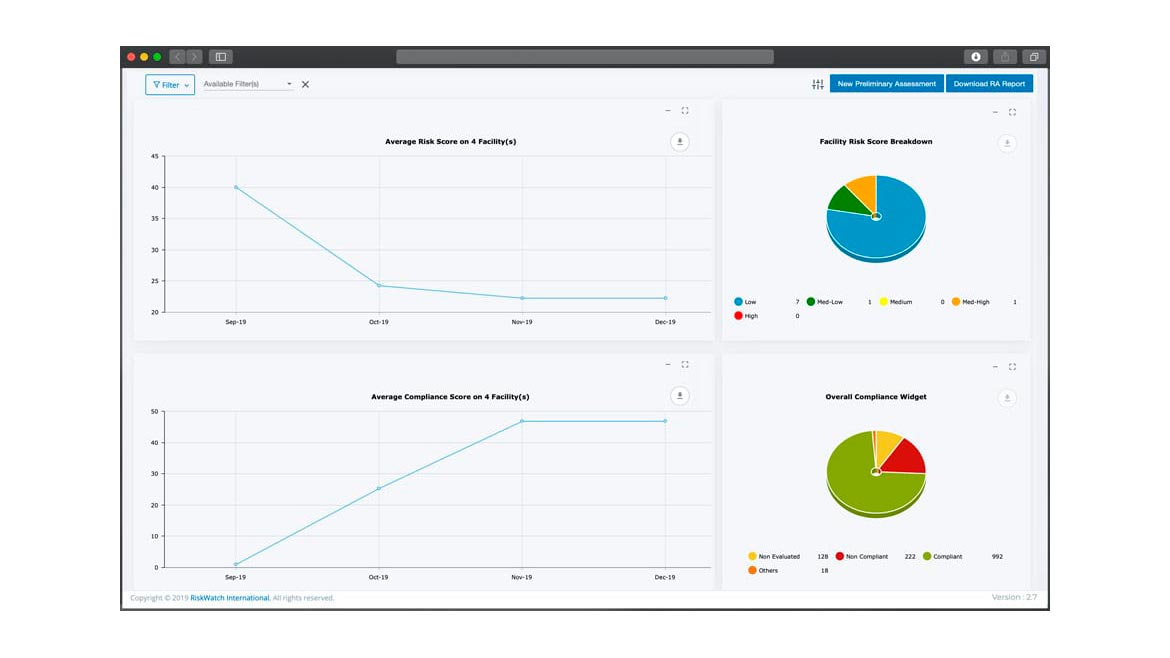
RiskWatch’s SecureWatch is a security and risk assessment platform that can be utilized for facility compliance and security risk assessments to help reduce liability exposure, manage risk, monitor and maintain security, and track continuous improvement. With a web-based solution, offline and remote users can complete assessments and upload supplemental documents that sync when they regain connectivity. The software automates assessments by sending emails to users, introducing them to the assessment process, pushing them through the assessment and offering recommendations, and then assigning tasks for mitigation. Security teams can use a global register to create standardized assessments for standards and regulations and customize questions and formats to fit their organizations’ compliance and risk landscapes. Image courtesy of RiskWatch
Find out more at www.riskwatch.com
Smiths Detection
Security Screening for Explosives
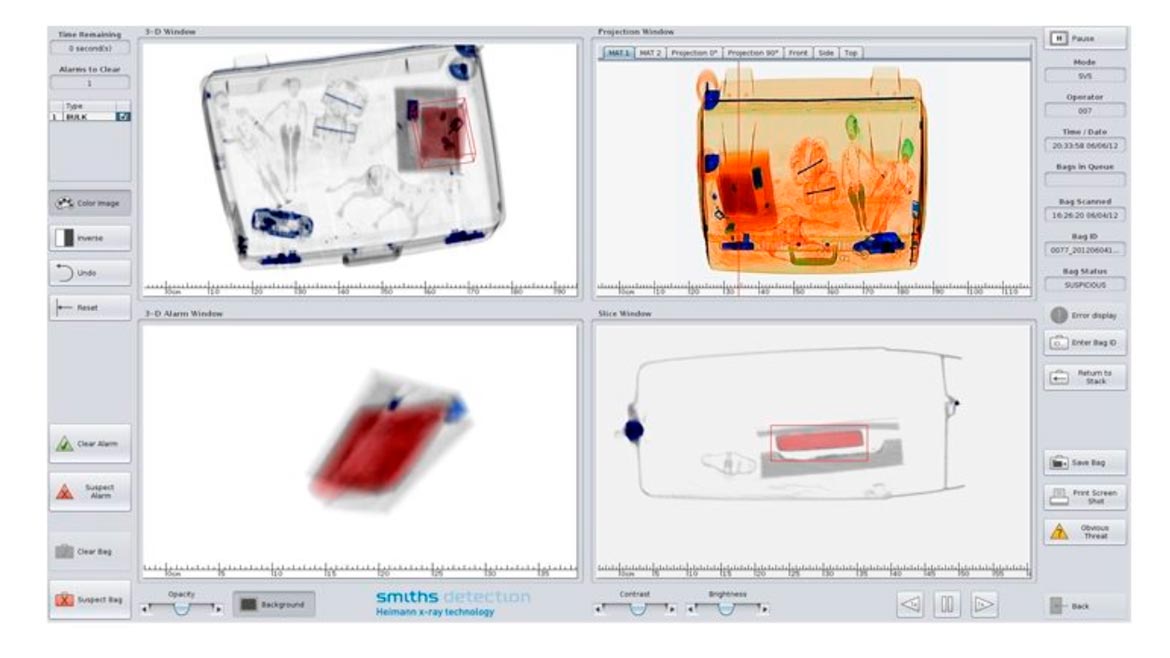
Smiths Detection’s Explosive Detection System (EDS) HI-SCAM 10080 XCT is an X-ray computed tomography system for hold baggage and air cargo. The solution is on the U.S. Transportation Security Administration’s (TSA) Air Cargo Screening Technology List (ACSTL), which serves as an official guide for regulated parties to use when procuring screening devices. The solution is equipped with a dual-view, dual-energy X-ray line scanner with 3D volumetric computed tomography imaging and reconstruction. The automatic detection of dangerous goods such as lithium batteries, flammable solids and liquids, and compressed and liquefied gases can be integrated into the HI-SCAN 10080 XCT. Image courtesy of Smiths Detection
Find out more at www.smithsdetection.com
Topo.ai
Supports Physical Security Operations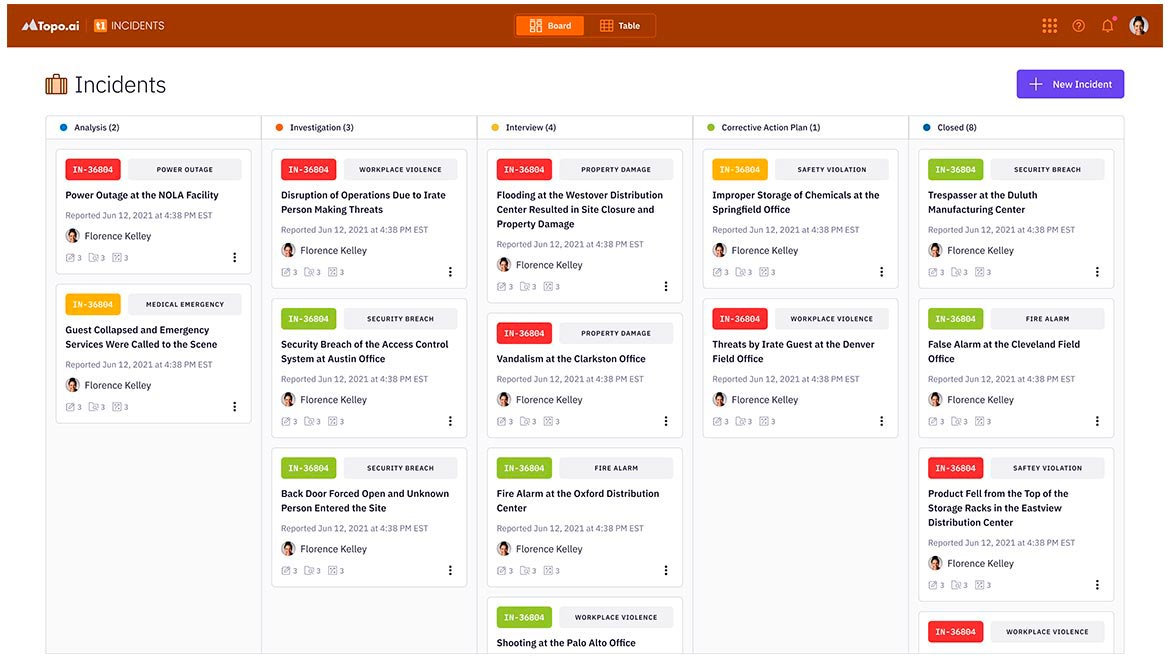
Topo.ai and MAX Security have integrated alerts, intelligence and reports from MAX into the TopoONE critical event management platform. The geolocated information helps update the threat intelligence needed by corporate security teams with assets around the world. The threat intelligence includes detailed region and country-specific risk assessment reports available on a daily, weekly and monthly basis, as well as global COVID-19 assessment reports. With the partnership, multilingual security analysts are available for consultation and situation-specific recommendations. Image courtesy of Topo.ai
Find out more at www.topo.ai
Vismo
Location Monitoring and Safety for Travelers
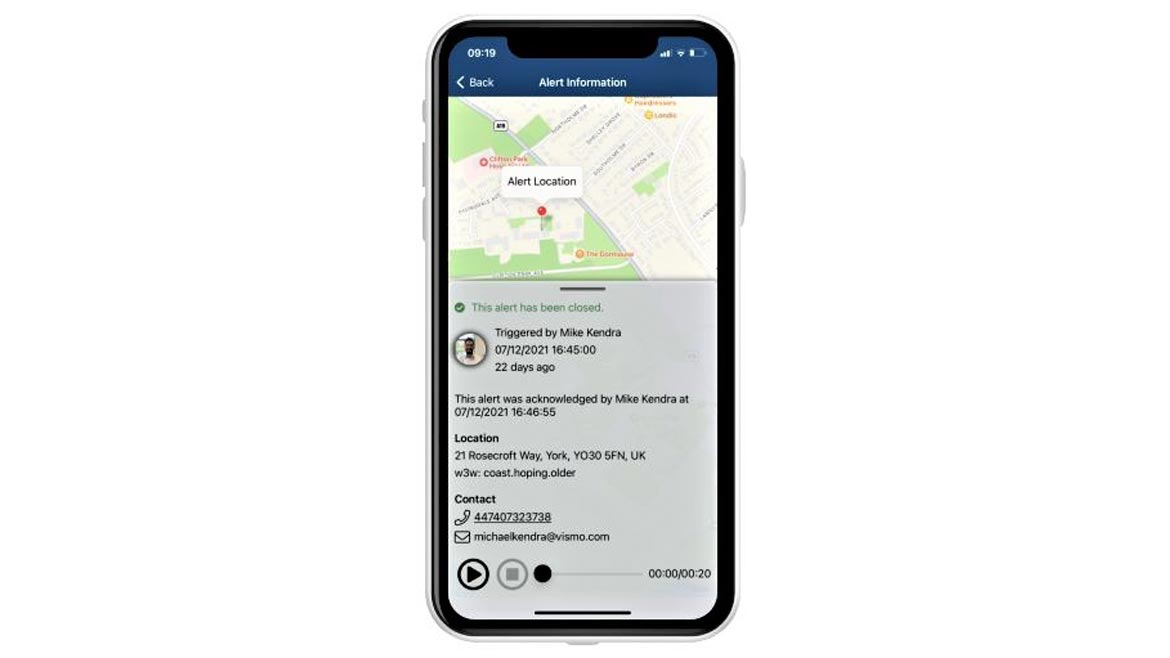
Vismo’s Vismo Monitor is an app that organizations can use to monitor alerts about threatening or potentially threatening events from their traveling or lone working employees. Employees who find themselves in a high-risk situation can activate alerts using the Vismo Locate & Protect App and Red Alert feature. The alert will then notify security teams through an in-app message. The app is designed to help all traveling employees, lone workers, or those away from home or working from home. Image courtesy of Vismo
Find out more at www.vismo.com
Product Spotlight: Product spotlight on cybersecurity threat monitoring and risk assessment solutions
For more articles on threat monitoring and risk assessments, visit:
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






