Education & Training
COVID-19 brought all hands on deck: Why we need to keep it that way

mixetto / E+ via Getty Images
Duty of Care spells out responsibilities an organization has for its people. This includes making the workplace safe, preventing risks to health, and ensuring safe working practices are set up and followed. There is a lot to deal with between these areas and the onus is on a variety of managers to ensure nothing falls between those cracks.
But who — or how — can a diverse team accomplish this effectively and efficiently?
Prior to COVID-19, most organizations tasked a patchwork of groups with largely stove-piped activities to meet Duty of Care responsibilities. They have functional names such as risk; security (physical and cyber); human resources; environmental, health and safety (EHS); emergency management; business continuity; and facilities and travel, to name the most common. But the pandemic has put a sharp focus on the entire organization taking care of all of its people every hour of every day. To manage the impact the crisis is having on an organization’s people and operations, most organizations have created a cross-functional COVID-19 Task Team. Over the last year, this team has met regularly to share information, formulate actions, make decisions, synchronize efforts, and evaluate results. This integrated approach has captured efficiencies for organizations while ensuring proactive protection of its people and assets, operations, and reputation.
The natural extension is to put this cross-functional team’s success towards institutionalizing a broader strategy that delivers operational resiliency going forward. Just as many organizations have adopted an Enterprise Risk Management (ERM) and/or People Risk Management (PRM) is already familiar, Operational Resiliency is a logical, holistic continuation of the COVID-19 Task Team’s newly mastered collaboration and processes. In addition to being more prepared for the next global health crisis, the essential principles can be applied to other types of disruptions from natural disasters to protests.
ERM is defined as “a plan-based business strategy that aims to identify, assess and prepare for any dangers, hazards and other potentials for disaster—both physical and figurative—that may interfere with an organization's operations and objectives.” Now substitute “organization” with “people” and you get a good idea of what PRM encompasses.
While people risk is often used to refer to human risks such as negligence, fraud, and theft, consider people risk as applying risk management principles to protecting people as a key asset. As such, PRM is the process of taking the necessary steps to identify, assess, and mitigate risks to and by personnel and responding effectively when an incident occurs.
A large body of work has been developed over the past two decades around Travel Risk Management (TRM) to protect people when they are on business travel—first with the Travel Risk Management Maturity Model (TRM3) and now with the anticipated release of the ISO 31030 Travel Risk Management – Guidance for Organizations publication.
Using a similar framework, essential elements of a PRM program would consist of 10 key process areas (KPAs):
1. Policy and Procedures: The infrastructure supporting policy and procedure development, implementation, and continuous improvement. Individual procedures such as SOPs are addressed in each KPA.
2. Training: Ensuring personnel have the necessary skills to comply and conform to program policy and procedure. Individual training items are assessed in their relevant KPAs.
3. Risk Assessment: A consistent, documented methodology for evaluating risk provided as input for the overall risk-based decision process.
4. Risk Disclosure: Information derived from the risk assessment analysis to ensure all those potentially affected understand the risk.
5. Risk Mitigation: Strategies and solutions that will result in a level of risk that is acceptable to all stakeholders.
6. Risk Monitoring: Continuous monitoring of potential threats or incidents affecting personnel and providing them with an easy-to-use process for reporting problems and accessing assistance.
7. Response & Recovery: Respond proactively to avoid or mitigate loss and return to business as usual (BAU) within the desired timeframe. This will typically involve location awareness of personnel, proactive threat monitoring, wellness checks, engaging protective measures and life safety procedures.
8. Notification: Ensures the appropriate people are informed of any relevant personnel risk information and addresses internal/external communications such as stakeholder notifications, escalations, and information requests.
9. Data Management: Establishes and maintains the data required to monitor and manage a robust PRM program adhering to privacy and security requirements. This data will include personnel profiles, contact information, location awareness, and other related information on facilities, operating locations, travel, resources, and processes. Program data to support oversight, incident reporting, and threat information is also included both internally and with third-party applications.
10. Program Communication: Strategic communication throughout the organization ensures understanding of both the organizational and individual responsibilities.
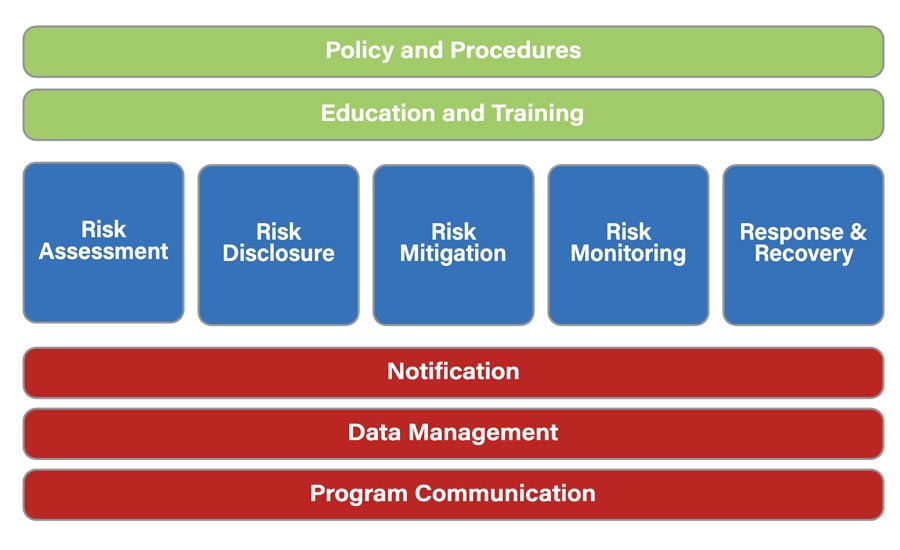
All 10 process areas must be engaged to have a comprehensive and effective PRM program. The overarching KPAs of policy and procedures and training are essential to the establishment of the program and the on-going realization of its value. The five management KPAs constitute the core risk management process, which is operating continuously both to proactively mitigate threats and rapidly respond to incidents when they occur. Infrastructure KPAs reflect the three most important capabilities needed to support the success of the program. This includes the ability to rapidly notify and communicate with potentially impacted personnel, access to and management of the internal and external data needed to support the program, and ongoing communications of individual and organizational responsibilities as well as how to report issues and get help
Let’s put this PRM framework into action. The objective of a PRM program is to effectively protect the organization’s people through cross-functional oversight, coordination, training, exercising, and continuous improvement. This effort is envisioned as a governance role, with each of the functional disciplines participating rather than passively reporting.
For example, consider the installation of new equipment at a manufacturing plant. The organization would conduct a cross-functional workplace risk assessment and based on this assessment implement a PRM plan. This equipment and the materials to be utilized may require actions related to safety, facilities, physical security, emergency management, business continuity, information technology, and other groups. All these functional groups would be involved not only in getting the manufacturing line up, but also ensuring the safety and security of its operation. The PRM risk monitoring KPA ensures training is completed, safety and security measures are properly maintained, safety drills are conducted, and incident reports are addressed with corrective actions by the appropriate functional groups.
Travel is another important use case. Many organizations have some variation of a Travel Risk Management (TRM) program to keep personnel safe when they are on the road. TRM fits nicely into the PRM framework because it sets specific procedures to address prior to travel, during travel, upon return, and in case an issue or incident arises during the trip. However, most organizations delegate the TRM program to the travel function with support from security. Within the PRM framework, TRM would have involvement from all the functional disciplines to address areas such as data privacy, mental wellness, insurance, and inclusion.
The large numbers of personnel working from home post-pandemic will likely continue at higher levels than before. A PRM program would continue the work done to manage the risks related to WFH and institutionalize the ongoing monitoring, assessment, mitigation, communication, and response processes.
A risk management program focusing on people would expand to address areas such as strategic personnel development, retention, liability reduction, anti-bribery, and social responsibility—all of which effect a company’s bottom line as much as its most valuable assets. Through a PRM program, organizations have a 360-degree view of risks related to all their people. Furthermore, it gives them the assurance that these risks are being continually managed by a fully integrated, cross-functional team that can assume a predictive, proactive posture that leads to efficiencies and maintains desirable productivity.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!







