America's Most Stolen Vehicles 2015
The National Insurance Crime Bureau (NICB) released its annual Hot Wheels report, which identifies the 10 most stolen vehicles in the United States.
The report examines vehicle theft data submitted by law enforcement to the National Crime Information Center (NCIC) and determines the vehicle make, model and model year most reported stolen in 2015.
Included with the release is a list of the top 25 2015 vehicle makes and models that were reported stolen in calendar year 2015.
For 2015, the most stolen vehicles in the nation were (total thefts in parentheses):
1. 1996 Honda Accord (52,244)
2. 1998 Honda Civic (49,430)
3. 2006 Ford Pickup (Full Size) (29,396)
4. 2004 Chevrolet Pickup (Full Size) (27,771)
5. 2014 Toyota Camry (15,466)
6. 2001 Dodge Pickup (Full Size) (11,212)
7. 2014 Toyota Corolla (10,547)
8. 2015 Nissan Altima (10,374)
9. 2002 Dodge Caravan (9,798)
10. 2008 Chevrolet Impala (9,225)
The following are the top 10 2015 model year vehicles stolen during calendar year 2015:
1. Nissan Altima (1,104)
2. Chrysler 200 (1,069)
3. Toyota Camry (923)
4. Toyota Corolla (776)
5. GMC Sierra (670)
6. Dodge Charger (666)
7. Hyundai Sonata (632)
8. Chevrolet Malibu (629)
9. Chevrolet Impala (594)
10. Chevrolet Cruze (586)
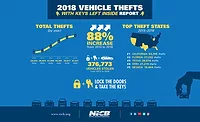
“While older vehicles still dominate our Hot Wheels most stolen list, the number of late model vehicles with anti-theft protection on the list goes to show that technology isn’t foolproof,” said NICB President and CEO Joe Wehrle. “Criminals are doing their best to defeat anti-theft technology through hacking and other means while, at the same time, manufacturers and others are working to improve security. Far too often, drivers leave their vehicles unlocked or with the keys inside, making it way too easy for an opportunistic thief. And as we noted recently, many stolen cars are not reported as typical thefts to police because many of today’s thefts are financial crimes involving complicated VIN switching, cloning, straw buyers, illegal exports and other sophisticated criminal methods.”
www.nicb.org
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!