Product Spotlight
Product spotlight: Sports, venue and entertainment security

When it comes to protecting sports, venue and entertainment environments, security leaders must manage staff and patron identities and protect facilities as varied as parking lots and stages. From sports stadiums to concert halls, security technologies can improve safety for all stakeholders.
Security magazine highlights sports, venue and entertainment security solutions, including drone countermeasures, parking management systems, weapons detection and more.
Azena
Connects AI-Based Security Apps to Smart Cameras

The Azena Application Store platform displays video analytic applications designed to run directly on a smart camera. Apps geared to stadiums and event venues can help optimize the flow of foot traffic through facilities through the use of artificial intelligence (AI)-enabled analytics that detect growing queue lines. These analytics can assist with personnel planning, as visitor flow through the stadium can be monitored through heat mapping, which reports data on the popularity of specific concession stands or visual displays. The platform’s apps can help increase the overall safety of a venue by proactively identifying violent or aggressive behaviors and prompting a response from onsite security. Image courtesy of Azena
Find out more at www.azena.com
Blighter Surveillance Systems
Detects Drone Activity

Blighter Surveillance Systems’ A800 Multi-Mode Drone Detection Radar uses multi-mode surveillance capability with a maximum range of 20km. The radar is capable of being mounted to fixed towers and masts, as well as to land vehicles and mobile surveillance trailers. The Blighter radar can help security leaders detect unauthorized drone activity in and around their facilities. Image courtesy of Blighter Surveillance Systems
Find out more at www.blighter.com
Databuoy
Localizes Gunshots and Alerts Responders

Databuoy’s Shotpoint system uses an Internet of Things (IoT) network of acoustic sensors to detect and locate the source of gunfire in indoor and outdoor environments. Shotpoint can help notify security with additional imagery and audio files. When a gunshot is detected, Shotpoint pushes out reports to all users, including those using mobile devices. Numerous video management system integrations give the system the ability to display the shooter at the moment of the shot. The solution’s outdoor anti-sniper capability can resolve rifle trajectories in locations like crowded concert venues and sprawling infrastructure. Image courtesy of Databuoy
Find out more at www.databuoycorp.com
Eagle Eye Networks
Detects and Analyzes License Plate Information

Eagle Eye License Plate Recognition (LPR) uses cloud-based AI to track license plate information from nearly any Internet Protocol (IP) camera. The LPR technology aims to recognize standard and non-standard license plates in settings including dark lighting and inclement weather. Eagle Eye LPR can allow security professionals to manage and add locations and cameras. By tracking license plate information at a venue, security leaders can identify threats when they enter the parking lot. Image courtesy of Eagle Eye Networks
Find out more at www.een.com
Gallagher
Aims to Increase SOC Workstations

Gallagher’s Command Centre helps build security operations centers (SOCs). Version 8.60 supports an increased number of incorporated controllers and workstations, a user interface for active directory synchronization and cloud and mobile integration. Command Centre v8.60 can support up to 10,000 controllers in a server environment, and up to 300 Command Centre client workstations can connect to the server simultaneously. The introduction of the Command Centre Cloud API Gateway can help integrate third-party applications via the cloud. Users can access Command Centre Mobile from many locations without the need for a corporate network or VPN. Image courtesy of Gallagher
Find out more at security.gallagher.com
Lumeo
Analyzes Parking Environments
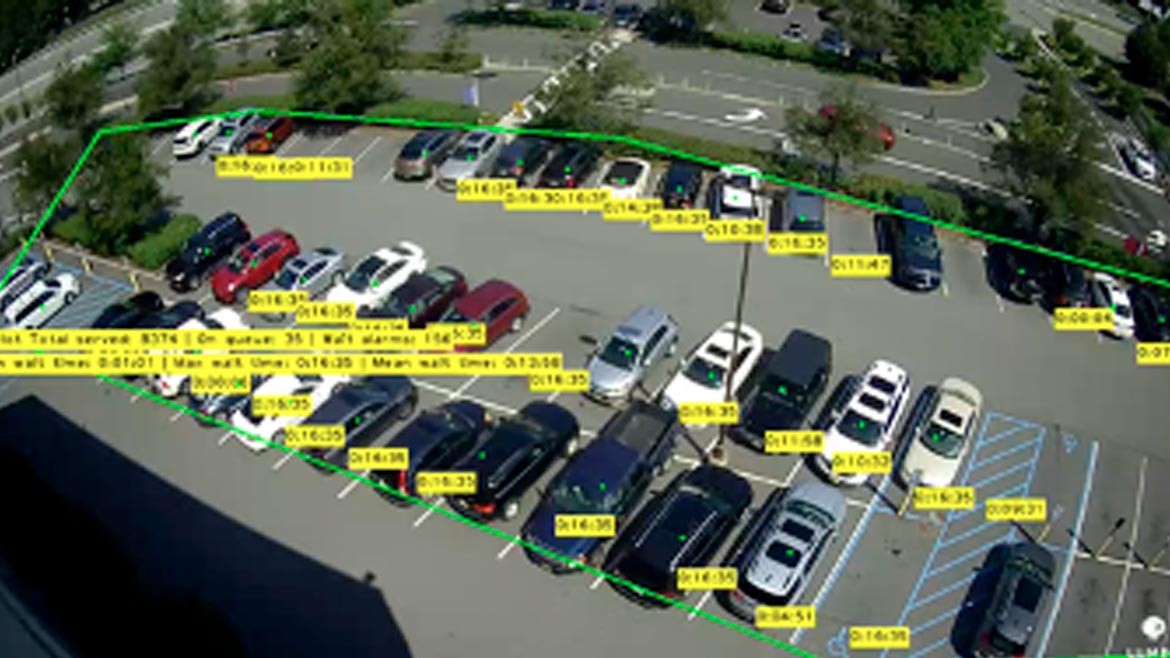
Lumeo has added Parking Management building blocks to its video analytics platform. The building blocks help security professionals at commercial parking facilities use existing camera infrastructure to collect security and business data with AI. The Parking Management building blocks include AI models for vehicle detection from multiple angles, LPR and analytic modules to compute occupancy and parking time. Image courtesy of Lumeo
Find out more at www.lumeo.com
Patriot One
Screens Event Attendees for Prohibited Items

SmartGateway is a patron screening solution from Patriot One designed for stadiums, arenas and live entertainment venues. SmartGateway can aid large venue security teams in protecting employee and patron entrances at facilities. By incorporating input from professional leagues, sports organizations and others in the stadium and arena space, the screening technology can scan patrons for guns, knives and other prohibited items upon entrance to a facility using AI-powered sensors. The solution can allow for a free flow of patrons into the venue, alerting security to incidents in real time. Image courtesy of Patriot One
Find out more at www.patriot1tech.com
ProdataKey
Controls Access by Location and Time

As part of its access control solution, ProdataKey (PDK) has introduced a QR Reader that can scan QR codes and barcodes to be used at stadiums, theaters, convention centers and other facilities where temporary access to restricted areas is permitted to changing groups of ticketholders or guests. Pre-event, system administrators can enter approved QR codes or barcodes into the access management software individually or en masse, granting holders temporary access to designated doorways, gates or turnstiles for a specific period of time. Proximity cards and PIN codes can also activate the QR Reader, allowing authorized staff to use the same security credentials they use elsewhere in the building. Image courtesy of ProdataKey
Find out more at www.prodatakey.com
Salient Systems
Monitors Patron Activity
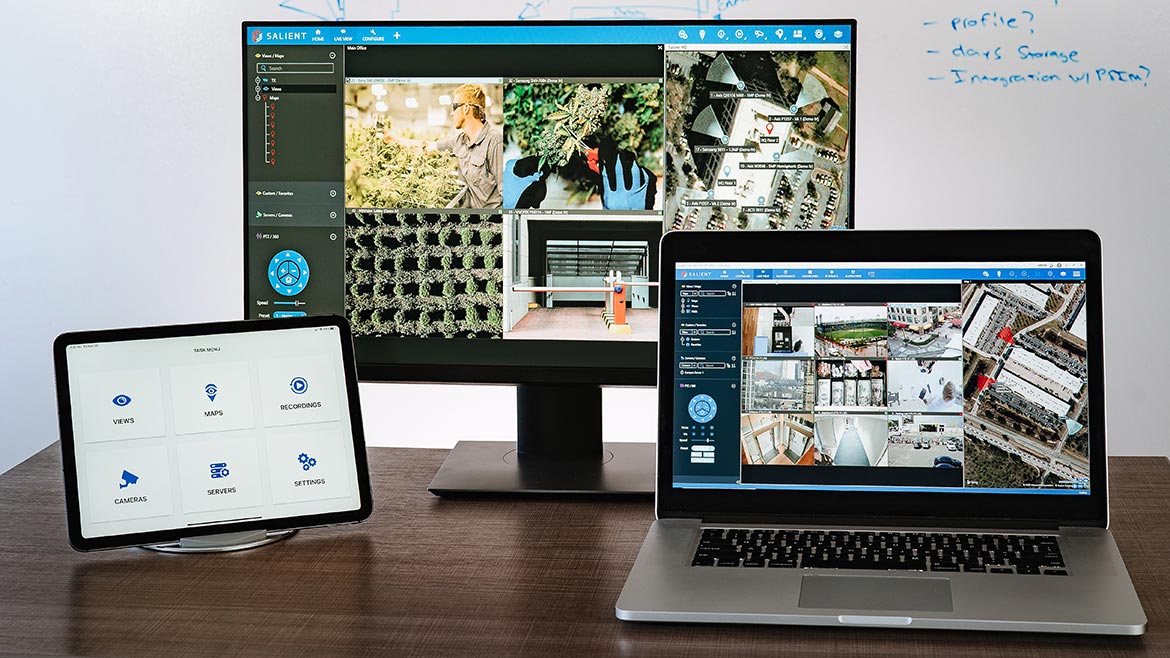
Salient System’s CompleteView video management software (VMS) platform aims to help security teams view, record and manage video surveillance data. Built with an open architecture, CompleteView VMS can be integrated with thousands of cameras, access control and analytics solutions. In an event venue application, CompleteView can determine the percentage of people visiting specific merchandise displays through heat mapping. It can also monitor queue length, notify attendees of wait times via signage, and analyze queue length patterns by time of day at specific concessions or kiosks for better staffing. Image courtesy of Salient Systems
Find out more at www.salientsys.com
Sentry Interactive
Facilitates Visitor Check-Ins and COVID-19 Restrictions
 The Sentry Interactive Tower is a security and visitor management platform that aims to manage access and secure in-person and hybrid workplaces. The technology incorporates a digital receptionist, facial recognition, visitor management, mobile credentialing, video surveillance, host notification and wayfinding assistance. The solution also aims to help security professionals with COVID-19 mitigation measures by facilitating mask validation, temperature checks, and vaccine passport captures. Security leaders can incorporate the Tower into existing access control setups, such as turnstiles and elevator systems. Image courtesy of Sentry Interactive
The Sentry Interactive Tower is a security and visitor management platform that aims to manage access and secure in-person and hybrid workplaces. The technology incorporates a digital receptionist, facial recognition, visitor management, mobile credentialing, video surveillance, host notification and wayfinding assistance. The solution also aims to help security professionals with COVID-19 mitigation measures by facilitating mask validation, temperature checks, and vaccine passport captures. Security leaders can incorporate the Tower into existing access control setups, such as turnstiles and elevator systems. Image courtesy of Sentry Interactive
Find out more at www.sentryinteractive.com
Shooter Detection Systems and Siemens
Tracks Gunshots With Audio and Video
 An integration between the Guardian Indoor Active Shooter Detection System from SDS and the Siveillance Video system software from Siemens aims to improve public safety in the event of an active shooter event. Guardian Indoor Active Shooter Detection System is a smart sensor network that utilizes acoustic detection software and infrared detectors to detect gunshots inside a building. The sensor transmits shot location information to Siemen’s video management system, which aims to help security professionals visually track the path of gunshots. By integrating these systems, shooter detection inputs can trigger automatic responses such as restricted access control and mass notification alerts. Image courtesy of Shooter Detection Systems and Siemens
An integration between the Guardian Indoor Active Shooter Detection System from SDS and the Siveillance Video system software from Siemens aims to improve public safety in the event of an active shooter event. Guardian Indoor Active Shooter Detection System is a smart sensor network that utilizes acoustic detection software and infrared detectors to detect gunshots inside a building. The sensor transmits shot location information to Siemen’s video management system, which aims to help security professionals visually track the path of gunshots. By integrating these systems, shooter detection inputs can trigger automatic responses such as restricted access control and mass notification alerts. Image courtesy of Shooter Detection Systems and Siemens
Find out more at www.shooterdetectionsystems.com
STid
Reads Many Forms of ID to Protect Entryways
 STid’s SPECTRE nano reader helps security teams identify employees, visitors and their vehicles in an access control and visitor management security solution.The reader can increase entry speed and read windshield tags, key fobs, cards, smartphones or wearables using ultra-high frequency technology and Bluetooth. The reader is compatible with third-party access control systems and aims to stand up to harsh environments. SPECTRE nano uses OSDP and SSCP protocols and has EAL5+-certified storage. Image courtesy of STid
STid’s SPECTRE nano reader helps security teams identify employees, visitors and their vehicles in an access control and visitor management security solution.The reader can increase entry speed and read windshield tags, key fobs, cards, smartphones or wearables using ultra-high frequency technology and Bluetooth. The reader is compatible with third-party access control systems and aims to stand up to harsh environments. SPECTRE nano uses OSDP and SSCP protocols and has EAL5+-certified storage. Image courtesy of STid
Find out more at www.stid-security.com
Winsted & Concept Seating
Provides Ergonomic Solutions for 24/7 Security Operations
 Together, Winsted and Concept Seating have partnered to equip control room operations with durable, comfortable, functional consoles, workstations and chairs. Designed for 24/7 environments or continuous-use workspaces, the solutions include configurable, ergonomic control room furniture designed to allow operations to minimize fatigue, boost efficiency and increase situational awareness. Image courtesy of Winsted
Together, Winsted and Concept Seating have partnered to equip control room operations with durable, comfortable, functional consoles, workstations and chairs. Designed for 24/7 environments or continuous-use workspaces, the solutions include configurable, ergonomic control room furniture designed to allow operations to minimize fatigue, boost efficiency and increase situational awareness. Image courtesy of Winsted
Find out more at www.winsted.com and www.conceptseating.com
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





