Home » security risk assessment
Articles Tagged with ''security risk assessment ''
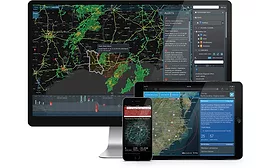
Helps to Ensure Continuity of Operations
Visual Command Center® from IDV Solutions
April 1, 2016
Is Your Program Security Theater?
Is your department making the enterprise safer, or is it a false sense of security? Take our quiz to find out!
September 1, 2013
Security News -- Critical Infrastructure
Serious Security Flaws Found at California Nuclear Plant
June 15, 2012
Sign-up to receive top management & result-driven techniques in the industry.
Join over 20,000+ industry leaders who receive our premium content.
SIGN UP TODAY!Copyright ©2026. All Rights Reserved BNP Media.
Design, CMS, Hosting & Web Development :: ePublishing