Product Spotlight
GSX 2023 product preview

This year, security leaders attending the annual Global Security Exchange (GSX) in Dallas, Texas from September 11-13, 2023 will find the latest security technologies from physical and cybersecurity organizations.
From video management and access control to vulnerability management, Security magazine highlights solutions from organizations at GSX 2023.
ALARM CONTROLS
Delays door opening to control access
 The 1200DE Delayed Egress Maglock from Alarm Controls (at GSX Booth #3033) safely postpones exit while alerting others onsite. This bracket-mounted, single magnetic lock with 1200 pounds of holding force can be installed without special tools. Integrated key reset, digital display, voice message countdown timer, and field configurable settings come standard in a single unit. Code-specific models are also available. Designed for applications that require a locking feature that delays the opening of a door, it can be used in healthcare for patient safety, retail for loss prevention, and more. Image courtesy of Alarm Controls
The 1200DE Delayed Egress Maglock from Alarm Controls (at GSX Booth #3033) safely postpones exit while alerting others onsite. This bracket-mounted, single magnetic lock with 1200 pounds of holding force can be installed without special tools. Integrated key reset, digital display, voice message countdown timer, and field configurable settings come standard in a single unit. Code-specific models are also available. Designed for applications that require a locking feature that delays the opening of a door, it can be used in healthcare for patient safety, retail for loss prevention, and more. Image courtesy of Alarm Controls
FIND OUT MORE AT WWW.ALARMCONTROLS.COM
ALTRONIX
Monitors traffic in public spaces
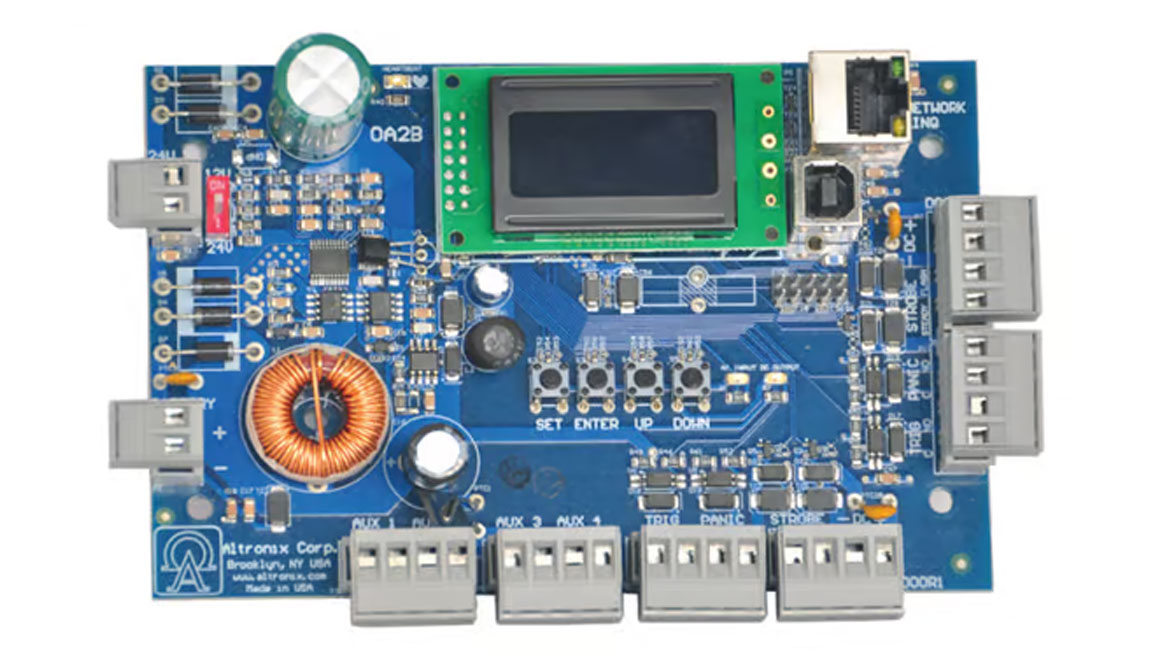 The Altronix OA2 occupancy alert system provides notifications when unauthorized activity or loitering occurs in up to two protected areas. The system is designed to help facilities reduce risks and liabilities in public-facing, secured areas such as restrooms — found in convenience stores, retail establishments, restaurants, universities, sports and recreation venues, and more. The OA2 is designed to work with most types of sensors for monitoring doors or restricted areas. Local alert notifications can be customized and may be audible, visual or both. Optional LINQ network communication enables real-time remote alerts and provides system status information. Normal traffic activity can be monitored as well. Image courtesy of Altronix
The Altronix OA2 occupancy alert system provides notifications when unauthorized activity or loitering occurs in up to two protected areas. The system is designed to help facilities reduce risks and liabilities in public-facing, secured areas such as restrooms — found in convenience stores, retail establishments, restaurants, universities, sports and recreation venues, and more. The OA2 is designed to work with most types of sensors for monitoring doors or restricted areas. Local alert notifications can be customized and may be audible, visual or both. Optional LINQ network communication enables real-time remote alerts and provides system status information. Normal traffic activity can be monitored as well. Image courtesy of Altronix
FIND OUT MORE AT ALTRONIX.COM
BOON EDAM
Detects and prevents turnstile piggybacking
 BE Secure from Boon Edam is an overhead detection system for use with full-height turnstiles. BE Secure is built for the detection and prevention of piggybacking. Boon Edam’s Turnlock Full Height Turnstiles with integrated BE Secure utilizes time-of-flight (TOF) measurement principles combined with artificial intelligence (AI) algorithms to detect when two people try to enter the same compartment on a turnstile using one credential. If piggybacking is detected, the turnstile automatically locks and refuses entry. BE Secure is built for internal and external applications. Image courtesy of Boon Edam
BE Secure from Boon Edam is an overhead detection system for use with full-height turnstiles. BE Secure is built for the detection and prevention of piggybacking. Boon Edam’s Turnlock Full Height Turnstiles with integrated BE Secure utilizes time-of-flight (TOF) measurement principles combined with artificial intelligence (AI) algorithms to detect when two people try to enter the same compartment on a turnstile using one credential. If piggybacking is detected, the turnstile automatically locks and refuses entry. BE Secure is built for internal and external applications. Image courtesy of Boon Edam
FIND OUT MORE AT WWW.BOONEDAM.COM
I-PRO
Visually detects and tracks threats
 The Rapid PTZ cameras are the smallest in their category and feature comprehensive edge artificial intelligence (AI) capabilities and a broad range of resolution options. With pan and tilt speeds up to 700°/s, operators can move the camera through multiple preset positions. IR LED capabilities enable the cameras to monitor in complete darkness up to 250 meters (820.2ft) while analytics and AI-based auto-tracking make sure that persons and vehicles of interest stay locked on target and in focus. All models are salt- and ISO 14993 rated to withstand the harshest conditions. The cameras are FIPS 140-2 level 3 certified. Image courtesy of i-PRO
The Rapid PTZ cameras are the smallest in their category and feature comprehensive edge artificial intelligence (AI) capabilities and a broad range of resolution options. With pan and tilt speeds up to 700°/s, operators can move the camera through multiple preset positions. IR LED capabilities enable the cameras to monitor in complete darkness up to 250 meters (820.2ft) while analytics and AI-based auto-tracking make sure that persons and vehicles of interest stay locked on target and in focus. All models are salt- and ISO 14993 rated to withstand the harshest conditions. The cameras are FIPS 140-2 level 3 certified. Image courtesy of i-PRO
FIND OUT MORE AT I-PRO.COM
HANWHA VISION
Connects cameras for scalable system
 Hanwha SolidEDGE is a serverless camera system with onboard Solid State Drive (SSD) storage and an embedded WAVE video management system (VMS) server. Each SolidEDGE camera can connect and record up to five additional cameras, bringing the total number of cameras in a system to six. Users can also merge up to 30 SolidEDGE systems through WAVE Sync. A metal-shielded RJ-45 terminal and enhanced grounding frame structures protect the camera from transient voltage from lightning or static electricity. A hard-coated dome bubble enhances resistance to scratches from external elements and minimizes degradation of resolution due to scratches. Image courtesy of Hanwha Vision
Hanwha SolidEDGE is a serverless camera system with onboard Solid State Drive (SSD) storage and an embedded WAVE video management system (VMS) server. Each SolidEDGE camera can connect and record up to five additional cameras, bringing the total number of cameras in a system to six. Users can also merge up to 30 SolidEDGE systems through WAVE Sync. A metal-shielded RJ-45 terminal and enhanced grounding frame structures protect the camera from transient voltage from lightning or static electricity. A hard-coated dome bubble enhances resistance to scratches from external elements and minimizes degradation of resolution due to scratches. Image courtesy of Hanwha Vision
FIND OUT MORE AT HANWHAVISIONAMERICA.COM
SALIENT SYSTEMS
Reviews, analyzes and stores video
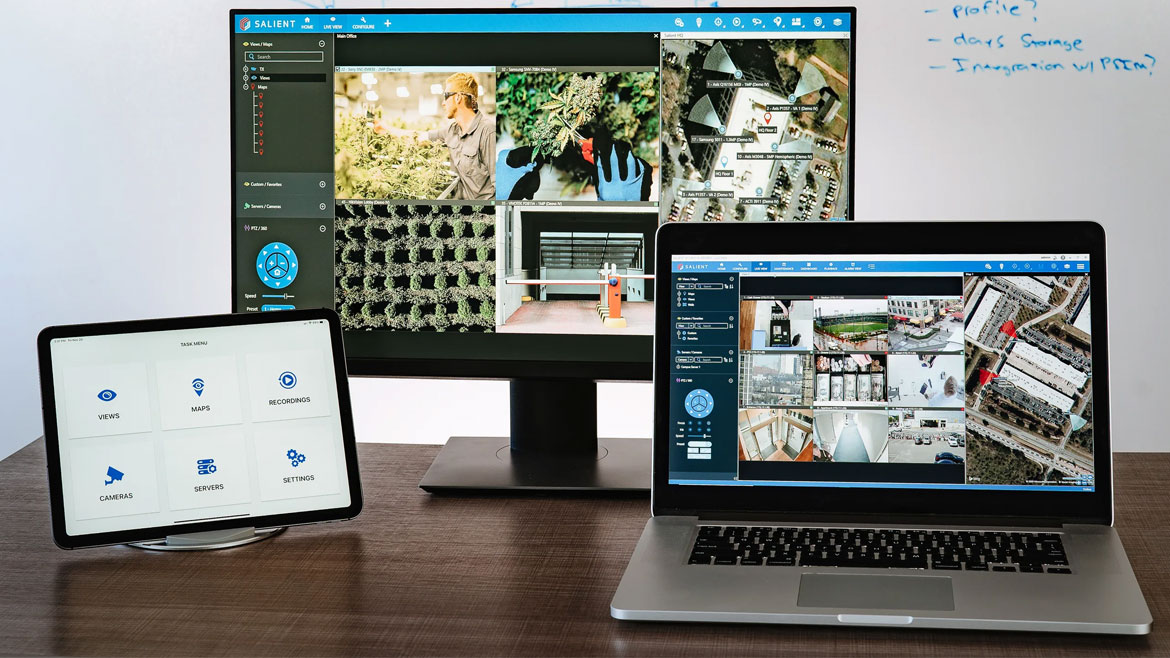 Salient Systems’ CompleteView v7.3 is video management software that includes new features designed to improve the user experience. CompleteView v7.3 has enhanced camera analytic event support. With this feature, users can configure and capture any event delivered over the ONVIF driver, regardless of recording type. The update also ensures the reliable capture and storage of all camera analytic events, the ability to set custom aliases for events and includes a new “Event Search” playback experience. Users can utilize features such as scrubbing, improved playback speeds, reverse playback, customizable skip forward/backwards and jump to next/previous event, and individual trim and export capabilities. Image courtesy of Salient Systems
Salient Systems’ CompleteView v7.3 is video management software that includes new features designed to improve the user experience. CompleteView v7.3 has enhanced camera analytic event support. With this feature, users can configure and capture any event delivered over the ONVIF driver, regardless of recording type. The update also ensures the reliable capture and storage of all camera analytic events, the ability to set custom aliases for events and includes a new “Event Search” playback experience. Users can utilize features such as scrubbing, improved playback speeds, reverse playback, customizable skip forward/backwards and jump to next/previous event, and individual trim and export capabilities. Image courtesy of Salient Systems
FIND OUT MORE AT WWW.SALIENTSYS.COM
QUANERGY SOLUTIONS
Tracks people and objects through a space
 Q-Track is an integrated end-to-end hardware and software solution comprised of 3D long-range light detection and ranging (LiDAR) sensors and smart perception software. Q-Track provides accurate and continuous tracking of more than 600 individuals simultaneously. Q-Track offers a coverage area of 165,000 square feet per sensor with motion detection, classification and continuous object tracking in large areas with sensor fusion technology. Q-Track allows users to leverage existing security-related investments, such as cameras and VMS, and acts as a force-multiplier by enhancing those systems with actionable intelligence that can be used for a variety of use cases in physical security, occupancy analytics, footfall analysis and space utilization. Image courtesy of Quanergy
Q-Track is an integrated end-to-end hardware and software solution comprised of 3D long-range light detection and ranging (LiDAR) sensors and smart perception software. Q-Track provides accurate and continuous tracking of more than 600 individuals simultaneously. Q-Track offers a coverage area of 165,000 square feet per sensor with motion detection, classification and continuous object tracking in large areas with sensor fusion technology. Q-Track allows users to leverage existing security-related investments, such as cameras and VMS, and acts as a force-multiplier by enhancing those systems with actionable intelligence that can be used for a variety of use cases in physical security, occupancy analytics, footfall analysis and space utilization. Image courtesy of Quanergy
FIND OUT MORE AT QUANERGY.COM
VIAKOO
Provides visibility into device vulnerabilities
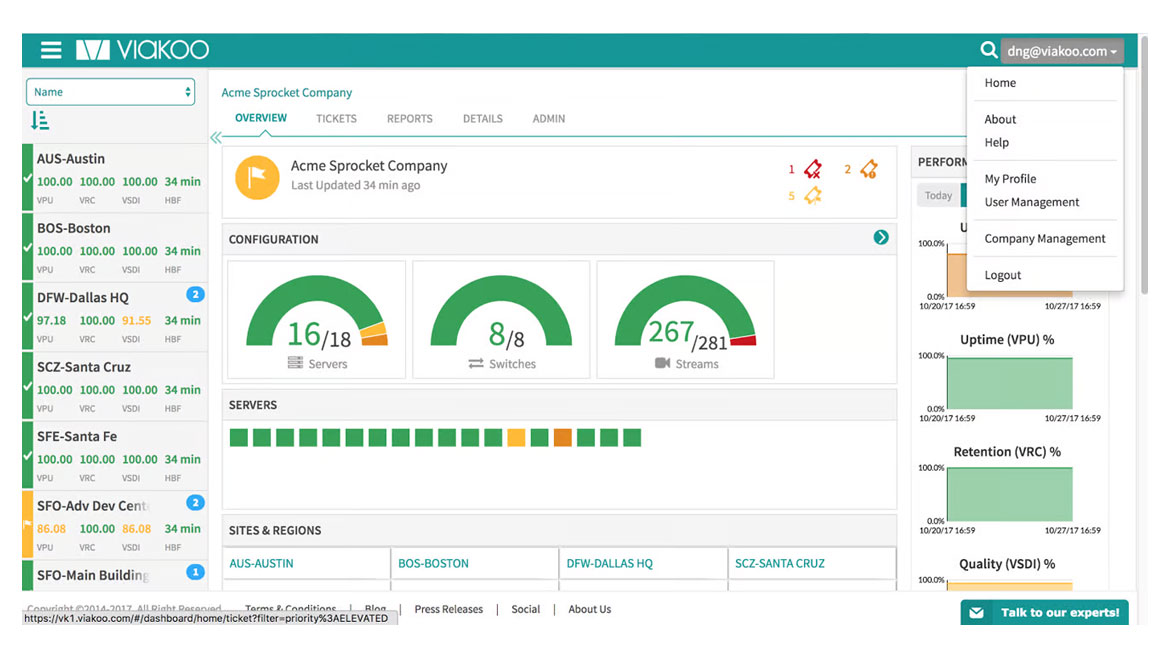 The Viakoo Action Platform includes comprehensive device lifecycle management capabilities. The platform’s users have visibility into device cybersecurity vulnerabilities through integration with the National Vulnerability Database (NVD) and can perform automated remediation across all impacted devices. The platform also provides comprehensive analysis and reporting on devices reaching their end-of-life, end-of-support and end-of-service dates. Image courtesy of Viakoo
The Viakoo Action Platform includes comprehensive device lifecycle management capabilities. The platform’s users have visibility into device cybersecurity vulnerabilities through integration with the National Vulnerability Database (NVD) and can perform automated remediation across all impacted devices. The platform also provides comprehensive analysis and reporting on devices reaching their end-of-life, end-of-support and end-of-service dates. Image courtesy of Viakoo
FIND OUT MORE AT WWW.VIAKOO.COM
VECTOR FLOW
Automates identity management
 Vector Flow’s Physical Workforce Identity Suite delivers the new science of PIAM automation, providing applications for automating all aspects of an identity lifecycle. Designed to deliver a one-credential, one-identity solution across the enterprise, the solution leverages AI technology to automate identity management tasks, such as on-/off-boarding of an identity into physical security infrastructure, badging and credentialing, physical access management, access audits and compliance. Image courtesy of Vector Flow
Vector Flow’s Physical Workforce Identity Suite delivers the new science of PIAM automation, providing applications for automating all aspects of an identity lifecycle. Designed to deliver a one-credential, one-identity solution across the enterprise, the solution leverages AI technology to automate identity management tasks, such as on-/off-boarding of an identity into physical security infrastructure, badging and credentialing, physical access management, access audits and compliance. Image courtesy of Vector Flow
FIND OUT MORE AT VECTORFLOW.COM
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






