The top identity-based attacks and how to stop them: Part 1
Part one of this two-part article series examines password spray, credential stuffing, and man-in-the-middle attacks and techniques and tools for mitigation
.webp?t=1659968418)
Image by jcomp via Freepik
The proliferation of Software as a Service (SaaS), the sudden explosion in a hybrid workforce, and the digital transformation revolution businesses have gone through all were aided by identity solutions that offer agility and modern capabilities. But as the reliance on identity has grown, so too have the attacks and threats. Identity-based attacks have not only been highly prevalent in breaches, but are getting more sophisticated, forcing security teams to constantly be on the defensive and shore up the front door to their organization’s data.
According to the 2022 Verizon Data Breach Investigations Report (DBIR), over 40% of all breaches involved stolen credentials and 80% of all web application breaches involved credential abuse. The presence of phishing attacks in breaches also rose from 25% in 2020 to 35% in 2021. Moreover, the attack surface continues to expand and aside from the traditional enterprise and the digital consumer, third-party supplier risk has taken center stage. Even ransomware attacks have increased to now comprise 25% of all breaches. While ransomware is not thought of in an identity-centric lens, identity is often compromised in order for ransomware to be installed.
What are the most prominent identity-based attacks and how are they carried out? In part one of this two-part series, we’ll look at three of the five most prevalent identity-based attacks, and how security teams can leverage identity technologies to mitigate those attacks and reduce their organizational risk.
Password Spray
A password spray attack comes from the brute force family of attacks and was involved in the 2019 Citrix breach. A threat actor attempts to use a few commonly known passwords across multiple accounts with the hope that even a single user has set that specific password for their login credential. By using a low number of qualified password guesses across many accounts, the attacker is able to stay under most account locking thresholds. Along with researching a company to pilfer possible password combinations, a threat actor may also do the same to determine if a system requires passwords to be a certain length, have special characters, include numbers, and other specific requirements.

How to defend against it
- Create sign-on policies to lock out an account after a low number of invalid attempts. If lockout creates too much friction for your organization, implementing a CAPTCHA can be a good alternative.
- Enforce specific password requirements during the initial account creation process that make using common passwords impossible.
- Implement an alerting system that assesses failed attempts across multiple accounts. A review of logs for failed attempts or a high number of locked accounts is a good sign that an attack is taking place.
Credential Stuffing
Credential stuffing attack is another subset of the brute force attack category. The threat actor attempts to stuff different credentials (often username and password harvested from an online data dump) into as many different sites and portals as possible with the hopes of one of them being successful. This type of attack exploits people’s tendency to reuse passwords across multiple sites and does not exhaust one single system. Avoiding password lockout limits, and frequently using automated tooling allows an attacker to cover a vast number of systems in a short period of time.
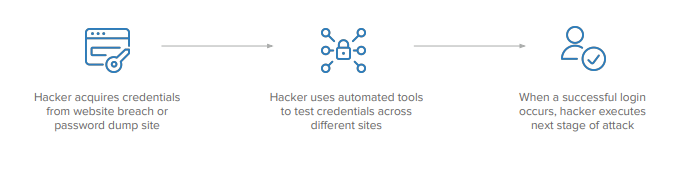
How to defend against it
- Adaptive Multi-Factor Authentication is a primary defense against credential stuffing attacks. By enforcing MFA, the threat actor is not able to complete the authentication flow, even if they have a compromised credential. Leveraging additional data points such as location and IP address can help to build a baseline profile and determine the risk level of the login attempt. In the event that MFA is not a control, try layering contextual access in conjunction with other checks such as device fingerprinting.
- Similar to MFA, security admins can set up CAPTCHA in the login flow in certain use cases to augment the security of the authentication request.
- Educating users to not reuse passwords, especially between sensitive and non-sensitive sites is another measure to reduce the likelihood of a credential stuff attack succeeding.
Machine-in-the-Middle (MITM)
MITM occurs when a threat actor is able to sit in between the user and the resource they want to connect to. Then, the threat actor will broker traffic between the user and the destination site, unbeknownst to the user. In this manner, the traffic flow is normal, however, everything the user is typing is going through the threat actor’s system, including passwords the user submits to login with.
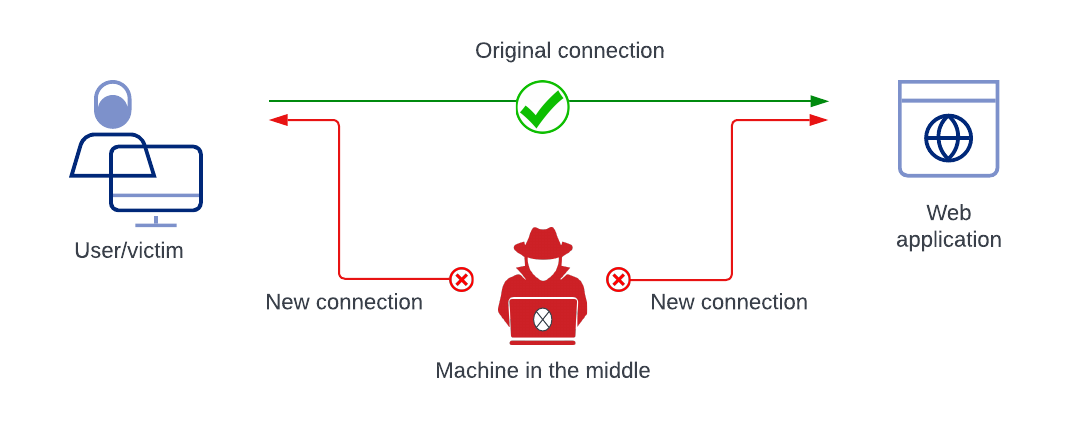
How to defend against it
- Machine-In-The-Middle attacks almost always start with phishing, so user education and training end users to be critical of certificate warnings and urls that mimic legitimate sites also goes a long way.
- Transport Level Security (TLS) is the obvious mechanism that can thwart the majority of MITM attacks. Encrypted communication will deter the attacker from sniffing sensitive information between the client and server.
- A strong phishing resistant MFA factor is the only way to ensure the attacker is not able to obtain a login session to the target server, while other methods can ultimately be phished. It does not however prevent the attacker from stealing credentials which may be used elsewhere.
Today’s threat landscape is rife with exploits when it comes to identity security, making it all the clearer how foundational identity is to an organization’s security posture. In part two of this series, we’ll delve into two more attack vectors: phishing and third-party attacks, and the ramifications that come along with both.
*All images courtesy of Okta
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!








