The top identity-based attacks and how to stop them: Part 2
Part two of this two-part article series examines phishing and third-party account attacks, techniques and tools for mitigation, and tried and true best practices for reducing overall identity-based attack risk.

Image by Freepik
In part one of this series, we discussed some of the top identity-based attacks, including password spray, credential stuffing and machine-in-the-middle attacks. To recap from the first part, in a password spray attack, a threat actor attempts to use a few commonly known passwords across multiple accounts with the hope that even a single user has set that specific password for their login credential. Enforcing specific password requirements during the initial account creation process can defend against such an attack.
In a credential stuffing attack — a subset of the brute force attack category — the threat actor attempts to stuff different credentials (often username and password harvested from an online data dump) into as many different sites and portals as possible with the hopes of one of them being successful. Mitigating such an attack involves the use of Adaptive Multi-Factor Authentication.
Machine-in-the-middle attacks occur when a threat actor is able to sit in between the user and the resource they want to connect to, brokering traffic between the user and the destination site, unbeknownst to the user. Transport Level Security (TLS) can thwart the majority of these attacks.
Part-two of this series explores two more top identity-based attacks — phishing and third-party accounts — and ways organizations can defend against them.
Phishing
Phishing (and broadly the extended category) is a tried and true attack vector as old as the internet itself. Phishing is when a threat actor attempts to lure the end user into clicking, downloading, visiting, or engaging with a malicious endpoint by crafting communications that seem legitimate. Targeted individuals (spear phishing), targeting high ranking personnel (whaling), attempting to gain sensitive information over the phone (vishing), are all techniques with the aim to obtain sensitive credentials either by having the user download malware to steal the information, coercing the user to outright provide the information to an attacker, or having the user visit a site and enter their credentials.
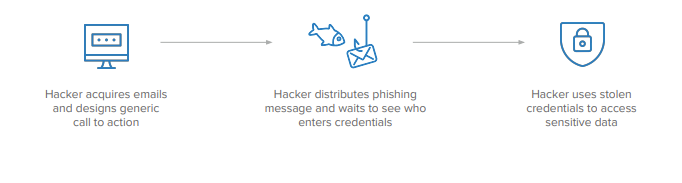
Image courtesy of Okta
How to defend against it
- Often user training is paramount and organizations run phishing campaigns constantly to familiarize their users with sniffing out phishing attacks.
- Technical controls such as behavior detection and step up authentication can help to alarm the end user of abnormal activity on their part.
- Using an open and neutral identity solution allows security teams to integrate leading email providers and set up policies with the email solutions for enforcing MFA, killing sessions, and locking users accounts.
Third-Party Accounts
Identities under an organization’s control are easier to manage and secure compared to those controlled by a trusted partner. The nature of federation is such that the service provider will trust the assertions that come from a partner’s identity provider. While it may be certainly unintentional, the compromise and breach of a partner’s identity provider can allow attackers to hop to your environment and access applications as an authenticated user.
Mitigation strategies
- When partners are accessing resources on your IDP, they must accept that regardless of the security controls they’ve configured, security enforcement will still occur on your IDP
- Configure risk based authentication and enforce phishing resistant factors for high risk logins
- Share login activity information with partners who can better assess anomalous behavior
Tried & True Best Practices
Looking beyond specific attacks and mitigation strategies, security practitioners should focus on a few broad approaches:
- User Education: End user training and education as well as enforcing best practices around passwords is a good starting point. If passwords are not reused, are not comprised of common dictionary words and users are mindful of separating sensitive logins from non-sensitive ones, then many of the techniques attackers deploy can be severely limited in their impact.
- Adaptive Multi-Factor Authentication: To layer additional security, enforce MFA. Traditional MFAs such as TOTP factors, push notifications greatly reduce the success rate of identity based attacks. These factors can be further enhanced by using phishing resistant MFA solutions such as biometric authentication to significantly thwart the efficacy of identity-based attacks.
- Log Correlation: Often overlooked but certainly critical is the logging and event correlation data. Identity provider logs should integrate to SIEM tooling. SIEM logs should be reviewed and proper alerting based on events needs to be set up. Examples include:
- Notification of multiple failed logins originating from cloud service provider IPs (i.e. AWS, GCP, or Azure).
- Login failures via the same username across multiple systems originating from the same IP and/or location and device.
- Successful authentication events that passed high risk login checks.
Sophisticated threat actors leverage multiple tools at their disposal in order to carry out attacks that range from precise and direct campaigns to casting wide nets in the hopes of playing the economies of scale game. By recognizing the most common threats and mitigating them, practitioners can keep their organizations secure.
To read part 1 of this series, click here.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!




.webp?height=200&t=1659968418&width=200)



