Protecting school devices in the age of digital learning

Despite many school districts now fully reopening to in-person learning, the days of school-owned laptops and other devices remaining safely plugged in at the end of each day are long gone. Fueled by much-needed, multibillion-dollar emergency funding from the federal government’s quickly enacted CARES Act, CRRSA and the American Rescue Plan, the number of school-issued devices being used by students has grown to the point where almost every student now has access to either a laptop or tablet.
One student, one device
A 2021 survey conducted by Education Week Research Center found that 42% of districts across the U.S. had purchased and issued devices for every student, with another 55% of districts purchasing them for at least some students. In the same survey, district leaders reported that they had rolled out 1:1 programs — in which each student has a school-issued device — covering 90% of middle and high schoolers and 84% of elementary students. This represents a remarkable increase from 66% and 42% respectively, when compared to the period immediately before the pandemic.
Data from Absolute Software’s latest Endpoint Risk Report on education revealed that 47% of K-12 devices in the spring of this year were located more than 25 miles from their school or district, compared to just 27% just one year earlier — a 20% increase. In addition, a considerable number of devices — 21% — were located more than 500 miles away.
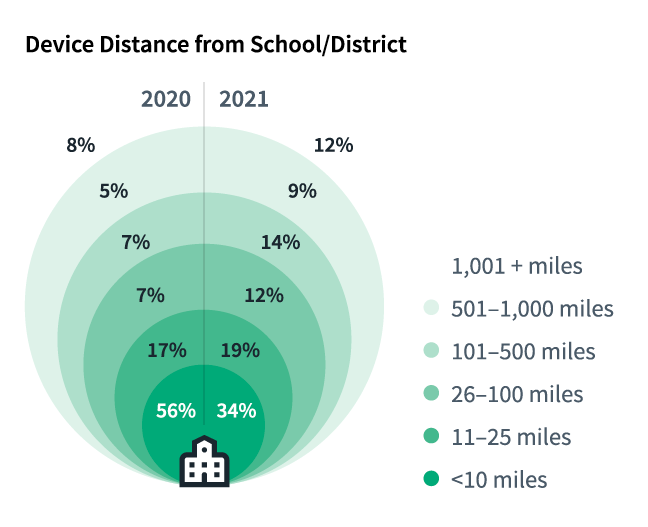
Image courtesy of Absolute Software
Although the increased mobility and the ‘learn-from-anywhere’ environment are both positive outcomes, the IT teams who support these districts are faced with the very real challenge of being able to track and manage much larger volumes of valuable assets that are now well outside the security of a school’s network. A prime example can be seen in these statistics: year-over-year movement increased by 48%, contributing to a very significant 45% increase in the number of devices being reported as missing or stolen in spring 2021 versus the same period one year earlier.
This all points to the fact that IT teams face a tough balancing act. On the one hand, the swift actions taken by school districts over the past two years undoubtedly helped students stay engaged in their academics during a very unpredictable time. However, from a purely IT perspective, there are some immediate challenges that school districts need to recognize and address.
Lack of visibility
One of the most obvious pitfalls that school districts fell into with their accelerated device rollout was that they sometimes — out of necessity — had to overlook their own standard procedures. For many, this created a lack of visibility that has resulted in new management and security challenges for IT teams that were already stretched thin. In addition to knowing where the devices were being used, the need to report and account for federal funding means that school districts are also expected to know how these devices are being used, as well as ensuring that students are adequately protected while online.
On top of these factors, the addition of untested applications on devices, delays in patching, and failing security controls have brought complexity and even more vulnerabilities to environments where security has often been an afterthought. It’s not surprising, then, that the education sector as a whole has become one of the largest targets for ransomware, placing both students and the schools themselves at heightened risk.
According to the Federal Bureau of Investigation (FBI), schools are now the top targets for cybercriminals, resulting in ransomware attacks, data theft, and the disruption of online learning. Fifty seven percent of all reported ransomware attacks in August and September of 2020 targeted K-12 institutions, up from 28% over the first six months of the same year.
Balancing learn-from-anywhere with security and end user privacy
This is not to say that we should turn back the clock. Devices today are often seen as the new classroom, meaning that device portability is an absolute must for most schools and the success of their educational roadmaps. Without trying to sound like a broken record, what’s important here is that IT teams have tools that help them maintain visibility and control over the entire device fleet, no matter where those devices are, or what network they are using. Normally this would be a huge undertaking even for a well-funded private organization, but for most school district IT teams, it is often an issue of budget as well as manpower.
One thing that should be a pre-requisite for this kind of device portability is proper tracking and asset management. Solutions like asset tagging allow IT teams to keep devices within view and up to date, regardless of their type or location. They often have capabilities that ensure that students are able to connect easily and safely, giving them proper access to class materials and assignments.
From cradle to grave
The learn-from-anywhere environment underscores the need for IT teams to scale their processes for device management. It starts with deployment, of course, but extends through each device’s entire life cycle, including collection, configuration and end-of-life.
As mentioned above, the location of school devices is also an important consideration. In addition to the health of critical security applications and the deployment of OS and other software patches, one of the basic indicators of device status that should be monitored is the device’s geolocation. Is the laptop or tablet located where it should be? If not, what are the associated risks? Has the device changed location regularly over the last few weeks or months, and are these changes both explainable and acceptable? With any highly mobile device, there will naturally be heightened risk due to the potential use of insecure Wi-Fi networks and the greater chance that devices will be left unattended, get lost, and possibly stolen.
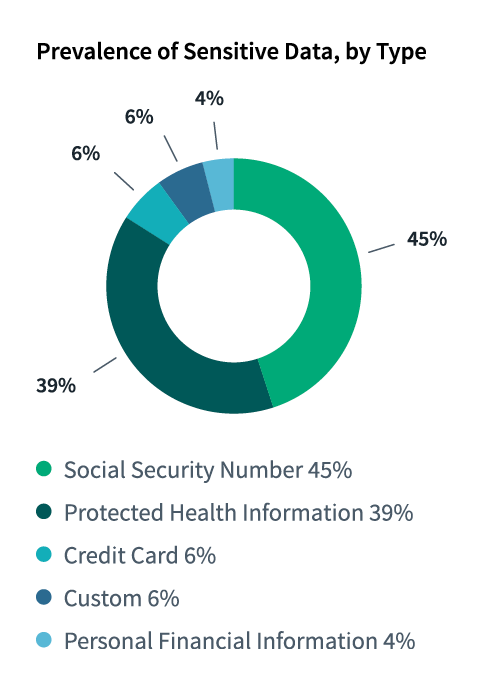
Image courtesy of Absolute Software
One of the most surprising findings from the education report was the amount of personal information that was found on school-issued devices. Almost a third of education devices in the study group contained some form of sensitive data. Of those, social security data was stored on 45%, and 39% contained protected health information.
With asset tracking in place, device losses and data risks can be greatly minimized. In addition, an extended feature set allowing IT teams to locate, freeze, or even remotely wipe the data from any device can be incredibly useful. A lot of these features can and should be automated, making it easier for IT administrators to implement granular policy controls that assist not only the management of the devices but also the reporting process.
As the world continues to figure out how best to deal with work-from-anywhere and learn-from-anywhere environments, organizations of all shapes and sizes will continue to grapple with the need for better security that doesn’t hinder productivity and usability. Balancing all of this with end -user privacy and device integrity is undoubtedly one of the biggest challenges for IT teams, who are now facing the ultimate test.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!









