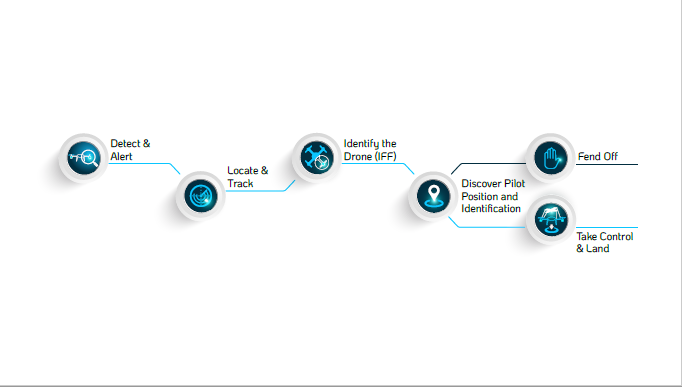
Six steps to control a rogue drone incident

The Minnesota Twins were leading the Pittsburgh Pirates 5-1 in the fifth inning when a drone appeared, hovering over home plate at Minneapolis’s Target Field. A timeout was called. No one seemed to know what to do. A few days later, a similar scenario played out in Fenway Park, followed by drone incidents at several more games this season.
Small, unmanned aircraft systems (sUAS), commonly referred to as drones, are ubiquitous, diverse, and increasingly cheaper and faster to market. Their small size, relative durability and vast range of capabilities make them a vexing target for security services, because dealing with sUAS detection means making split-second decisions between what could be a hobbyist’s gadget or a weaponized aerial vehicle carrying a dangerous payload. The drone surveillance challenge lies in proper drone detection and intelligent mitigation, which can only be achieved via a thorough understanding of the rogue drone event lifecycle.
So, how does the lifecycle of a rogue drone incident play out? Teach your security personnel six possible steps, all of which fall under two broader stages: detection, then mitigation.
Step 1: Detection
All drone events begin with detection, using four primary technologies: acoustic sensors (microphones); optical sensors (cameras); and traditional radar and radio-frequency (RF)-based methods, such as radio direction finders. RF cyber takes this even further, using cyber means to penetrate the RF communications.
Acoustic methods, such as a cluster of microphones pick up on the sounds a drone makes. Good microphones can use that sound to calculate direction.
Optical sensors are essentially video cameras. They rely on imaging technology, including infrared and thermal.
Drone detection radar sends out a signal as a burst, the reflection bounces and measures direction and position as the returning echo.
Radio direction finders use antennas to receive radio waves and then utilize a processor to analyze the RF spectrum. The finders can detect radio communication between the intruding drone and its controller.
There are various pros and cons for each of these methods, which will depend on the needs of the specific environment, as well as the individual characteristics of the drone.
Tall buildings in an urban landscape, for example, create limited lines of sight, rendering optical solutions ineffective. Noisy environments combined with quiet drones can challenge acoustics, and radar may detect false positives and then be unable to distinguish a bird from a drone.
Step 2: Location and Tracking
Now you want to locate and track the drone via GPS.
The above radars can be used for tracking and detection. If you deploy RF sensors, they could reveal transmissions between the drone and its pilot. This will give you the location of the drone and even in some cases the pilot as well.
If you relied on visual detection and identification, for example with optical sensors, you may be able to access information, map, and track from a camera, including GPS location and visual radius of the drone. This does, however, require line-of-sight.
RF cyber methods allow for passive and accurate real-time location tracking by extracting the drone’s GPS positions automatically, with no need for clear line-of-sight.
Step 3: Identification and Discovery
The next step is to know where the drone came from and ideally be able to figure out its intent. Many drones are friendly and pose no harm. You’ll want to extract the drone’s unique communication identification number, a.k.a. its “tail number,” which will tell you if this particular drone has authorization to be in the airspace. This will help you determine your next moves.
You should be able to identify from where the drone took off and you might want to identify the pilot – to alert law enforcement, to prevent future disruptions.
Step 4: Mitigation
Most traditional methods of mitigation have their origins in the military counter-unmanned aerial systems (c-UAS) space and tend to revolve around either jamming, or kinetic methods.
While these jamming and kinetic methods have proven to be effective in mitigating drones, they carry certain disadvantages and risks in urban and sensitive environments, especially with crowds or VIPs in the area, and when in close proximity to important communications.
Jamming systems can cause serious communications interference to your operational or security communications, GPS navigation, or control systems, and can disrupt Wi-Fi and cellular networks. In addition, the counter-drone effect is temporary until the jamming is over, at which point the pilot may retake control of the drone.
In some cases, the execution of mitigation with these methods represents the end of the incident, hopefully with a positive outcome. In some situations, depending on the technology applied, two other potential steps within mitigation may arise as viable options, both of which focus on this aspect of the drone’s operations.
Step 5: Fend-Off
“Fend-off” means mitigating the drone without destroying it or totally disabling it. In particularly sensitive areas, fend-off may be a useful option.
During fend-off, the signal of the rogue drone operator’s remote control is disconnected. This will either cause the drone to hover in place or fly back to its original takeoff position. Either way, the immediate threat is dissolved.
While jamming may also cause a drone to hover or go back to take-off position, it also interferes with nearby frequencies – this could include nearby airports, internal security communications, media, etc. Contrarily, an RF-cyber fend-off is surgical in its approach to cutting the drone’s remote-control communications, without adverse effects.
Step 6: Takeover
In some scenarios, a drone incident lifecycle will end before step 5. You may learn that the drone in question is harmless, and it will either leave your air space, or you’ll decide to let it fly away.
In other scenarios, a fend-off will be performed, which may mitigate the threat and partially resolve an otherwise dangerous situation, at least for the duration of the incident.
Another option, only recently available using new developments in RF-cyber takeover, is ending the incident by seizing control of the rogue drone and landing it safely. In a takeover situation, you as the defensive operator, or your autonomous system, will complete the detection and mitigation steps, and set a new flight path for a safe landing of the drone. Takeover avoids the risks of disruption and collateral damage, and focuses on maintaining control, ensuring a safe landing, and maintaining continuity. This method also allows for inspection and/or confiscation of the drone.
Back in Minneapolis, MLB players were lobbing baseballs at the hovering drone when it started to buzz away and both Twins and Pirates got back on the field. Security personnel at the stadium could have struck out in a major way, but sometimes the drone operator ends the drone incident lifecycle. No two drone events are the same. Like drones themselves, each is unique and often full of surprises.
This article originally ran in Security, a twice-monthly security-focused eNewsletter for security end users, brought to you by Security Magazine. Subscribe here.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!








