Managing the CFO Relationship for Strategic Security Advantage
|
Security is no longer just a hot topic among security professionals. It’s crossed the boundaries into mainstream media and political debates. You can’t watch the news or read a newspaper or magazine without hearing about cyber threats, personal information breaches or risk management. But that doesn’t mean that company executives have opened their wallets to each and every security project their security staff submits – if only it were that easy.
However, fortunately those of us in the security profession no longer need to build our case from the ground up by providing a definition of cyber, breach or risk. I don’t mean to be facetious, because that is where we were some five to 10 years ago. Today we work in an environment where security risks are real and are already being discussed and debated at the board level. CEOs are asking the questions, “Is our company properly protected against an attack?” and “Is our customer data secure?” Our job as security experts is to ensure we can answer those questions in the affirmative, either now or in the very near future. But that means getting the funding and resources needed to implement new projects and programs that address these threats – and the only way to successfully secure budget and resources in most companies is via the Chief Financial Officer (CFO).
Historically, the CISO position has been viewed primarily as a technical role, with limited knowledge and experience on the business side of things. CISOs were asked to protect the company and its assets by using security best practices, ensuring that the most obvious vulnerabilities were mitigated through the implementation of technologies, processes and/or policy. Most of the security projects were no-brainers, and CFOs needed little convincing that investing in these activities was necessary.
But as the network perimeter erodes and data becomes more mobile, convincing executive management that investment in a certain project will mitigate the perceived risk becomes more difficult. Our projects have become less tactical (i.e., implementing firewalls) and more strategic (i.e., data management). Today’s business cases have become more complex and more difficult to define with sub-projects that are multi-pronged and take years to complete instead of weeks or months. This can all lead to very difficult and frustrating conversations with your CFO when trying to justify the need for, say, half a million dollars and two extra headcount.
But it is not impossible – and with a little preparation work and some expanding of your own vocabulary, you will be better armed to go to battle with the CFO before he or she throws your business case in the declined stack.
Here are the activities I have used successfully to create a stronger working relationship with our CFO to ensure when I need his approval and/or endorsement on a project, he will be well-versed in the topic and more likely to sign his name on the dotted-line.
1. Stakeholder Management
One of the most useful activities I use to create a stronger working relationship with the CFO is stakeholder management. We schedule monthly meetings to discuss a broad range of topics, including risk management, cost of crime, current regulatory requirements and contract assurance. I also like to share information on recent breaches reported through the media and how we would have fared as a company under a similar attack. This makes the threat seem more real and current, which helps lay the foundation for future projects that will require his support and budget. This regular engagement also offers an opportunity to familiarize the CFO with terms and topics that are being reported in the media, providing him a better understanding of how current threats could impact our business.
2. Talk Risks, Not Threats
Unfortunately, the CISO has on occasion been compared to Chicken Little with ”the sky is falling” stories about cyber-war and Advanced Persistent Threats (APTs). So I find it valuable to turn the discussion with your CFO from “threats” to “risk.” CFOs understand risk and work in a risk-based model routinely, so change the discussion from a technology-based approach to a business-based approach by quantifying the impact in comparison to the risk appetite. By showing the ROI of your previous projects in terms of reduction in the likelihood and impact of a risk, you’ll likely capture the CFO’s attention by framing the discussion in language and terms he or she understands.
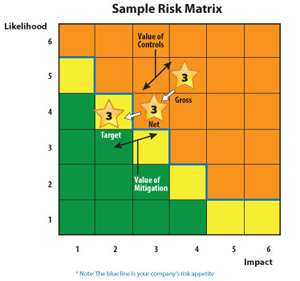
I like to use a risk matrix to display the risks I’m tracking and how they are trending. The graphical display of risks can allow for a much more concise discussion and serve as a form of educating the CFO on particular security risks that are impacting the company. In this way, when I approach the CFO with a business case to address one of those risks, he will already have some background on the topic, which will allow the discussion to go straight to ROI and risk reduction instead of having to explain the basis of the project.
3. Learn to Speak “Business”
One of the most important things I’ve learned is how to speak the language of my senior executives. While the CFO might be impressed by my command of technical lingo, what he really wants to know is how the money that is funding my security budget is being used and how precisely it is protecting the company and the bottom line. Being able to talk about what I do in terms of “risk appetite” and “revenue protection” has helped me have security needs woven into the fabric of decision-making. You know you’re having an impact on the CFO’s thinking when he asks other managers submitting business case proposals if they have taken into consideration the risk impact of their new project and whether Security has been involved in the discussion.
4. Reach out to Business Partners
Engaging with all the different groups within the business – from Legal to HR to the design team – can provide you an opportunity to embed your projects into their business cases and increase your chances of success. It will only take a few times where the CFO asks your colleagues about Security in a business case before you have those same business partners approaching you to get your involvement in their projects and programs. Creating a cooperative and collaborative environment with your colleagues will prove quite valuable, especially when they are willing to endorse and support your projects to the CFO.
5. Change Your Communication Style
Too often Security is perceived as what I call “The Department of No” – and that’s not a fun reputation to have. Nor is it likely to win you allies and advocates on the front lines where you need them most. Working collaboratively means you will be less likely to be circumvented and locked out of key decisions and forced to play catch-up. It will also take you out of the perceived role of being a technical manager and viewed in a more friendly light of being a business manager where your technical knowledge and business acumen is respected and sought for key decisions.
6. Align Your Projects with Compliance Requirements
We in security have been burdened by the recent increases in regulatory and legal compliance requirements so we might as well take advantage of all the additional work by wrapping things like Sarbanes-Oxley, PCI, HIPPA and SB 1386 into our business cases to bring some additional weight to the need to implement. CFOs are quite familiar with compliance and the legal/regulatory implications of getting this wrong, so using them in your business case will serve to get the CFO’s attention and provide some clear value to your project. There is also the added benefit of helping to drive revenue with customers that are more rigorously regulated if you implement and maintain compliance programs such as ISO 27001 or SSAE 16 (formerly SAS70). So where you can embed these into your projects and provide data on revenue increases due to these certifications, it will only bolster your case with the CFO.
7. Know Your Business
This topic should really have been first on the list, but if you walk away with nothing more from this article than this paragraph, then hopefully it will have been of value to you. I can’t tell you how many security professionals I’ve met who can’t even explain the core business of the company where they work. I’m not trying to insult my colleagues, that’s just the way it has been in the past. Security was very separate from the rest of the business, and understanding the core function of a company was not all that relevant to implementing security.
But the workplace has changed a great deal, and it’s now necessary for Security to have a true understanding of a company’s assets, its core products and/or services and the impact brand and reputation have on its ability to succeed and survive in the market. One easy test you can give yourself to see if you understand your company’s core business is to have a two-minute elevator pitch. If you can explain to a friend or colleague what your company does in those two minutes, then you probably know the business better than most. But if you can’t, well, perhaps it’s time you spend a bit more time listening in the management meetings and little less time checking your smartphone.
I know that every company and CFO is different and not every business case you present is going to get approved, no matter how adept you are at stakeholder management or risk-modeling. But hopefully by implementing the steps above, you will put yourself in a much stronger position with the CFO and other key business stakeholders so that when that “must-have” project comes along, you will have done the up-front work to put you in the best possible position to succeed in securing the necessary budget.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!




