Keeping Track Saves Money: IP Covers Everywhere

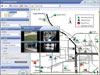
It started out as analog for maintenance security but soon developed into a sophisticated IP-based security video design on a software platform that will, one day, handle over 900 cameras and a dozen remote sites.
With over thirty K-12 schools housing nearly 20,000 students and several administration buildings, the Beaumont Independent School District was looking for the most cost-efficient means to keep track of activities during and after school hours. Additionally, like most districts in the country, officials were looking to implement a strong presence as a deterrent to possible criminal activity while insuring the safety and security of all their pupils and staff.
Greg Schumacher, senior network and programming administrator for the district, working with security systems integrator Micro Integration, investigated several video surveillance options to address immediate areas of concern with an eye on expanding whichever system they selected to cover all of the district’s facilities.

START WITH MAINTENANCE
The system proved its value quickly by helping school officials and the police department quickly identify and apprehend suspects. Mort importantly, incidents at the maintenance department quickly subsided once the word got out that the premises were under constant video surveillance.
Schumacher then looked to apply the same design to the three high schools. This required a more elaborate video surveillance control and management platform to tie the satellite video surveillance systems together from the three remote locations. To start the process, Schumacher and his team provided a wish list of capabilities and functionality to the systems integrator. The integrator recommended a comprehensive video control and management software solution from OnSSI that integrates camera control functions, NVR, virtual matrix, intelligent video delivery and content analysis all in one.
“When we first started looking at various IP video surveillance control solutions on the market, it was quite overwhelming,” said Glenn. “Now we have templates and standards built using the software solution that we use on various projects. Our installation times are shorter and the customer receives a premier solution with open architecture so they are not locked into any manufacturers’ cameras.”
IMMEDIATE RESULTS
To facilitate monitoring operations, staff accesses cameras with map overlays of the city that display all the schools’ locations. The system is hosted on multiple servers custom built by the integrator at multiple sites and integrated. The IP video surveillance system shares a centralized network backbone with the district’s IT system but is partitioned to assure uninterrupted operation and added network security. The cameras streaming to the servers require significant bandwidth on the district’s 1Gbps Ethernet network, so each of the satellite systems run independently on their own backbones and are then tied together on a WAN that feeds into the software platform. This distributed architecture greatly helps conserve bandwidth use.
The satellite systems integrate so they can be viewed from various locations including principals’ offices and directly at the police department. Principals can only see their own schools while the police have access to every camera in the system. Schumacher and the IT staff have control over all system programming and functions along with the integrator.
The bottom line: The solution is reducing incidents, improving surveillance and response, and saving the school district real dollars. Concluded Schumacher. “It’s very efficient and easy to use, as are the control functions for PTZ cameras, allowing even novices to operate them. As we continue to expand the video surveillance system here at the Beaumont Independent School District, the video control and management solution continues to exceed our expectations.”
SIDEBAR: Bringing Megapixels Down to Size
A superior video compression technology, known as MPEG, has been available in low-resolution cameras for years. The latest version of MPEG known as H.264 or MPEG-4 (part 10) or AVC was finalized by standards’ bodies. It offers a significant stream reduction over MJPEG, as well as MPEG-2 and MPEG-4 (part 2) by as much as 20 times with no sacrifice in video quality.
However, the significant benefits of H.264 come at a cost: a multi-fold increase in computational complexity of the H.264 encoder. Numerous vendors now offer or have standardized on H.264, especially since the technology's big splash last year. One example, Arecont Vision's developed a fully proprietary H.264 encoder which supports their megapixel IP cameras across a full range of video formats, frame rates and resolutions. In addition, the H.264 encoder had to support MJPEG as an option and support multi-streaming: a simultaneous transmission of several H.264 video streams at different video formats, frame rates, and/or resolutions.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!




