Product spotlight on mobile solutions

Mobile security solutions allow organizations to protect sensitive information and objects even when off-premises. Security magazine highlights both cyber and physical mobile security solutions.
Cisco Duo
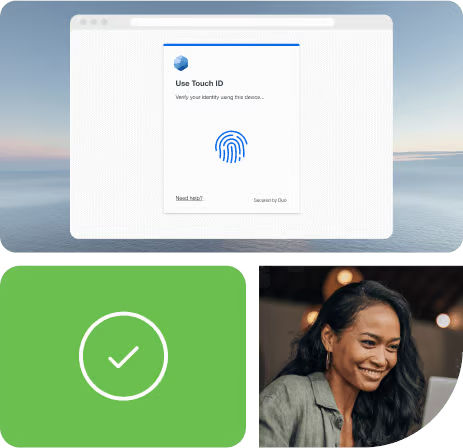
Protect Identity Through Multi-Factor Authentication
Duo’s Continuous Identity Security safeguards against intricate identity threats 24/7 while maintaining a smooth authentication experience for your entire workforce. Users can stay protected with flexible multi-factor authentication (MFA) including options using FIDO2 for phishing-resistant authentication. Image courtesy of Cisco Duo
Find out more at duo.com
Keeper Security
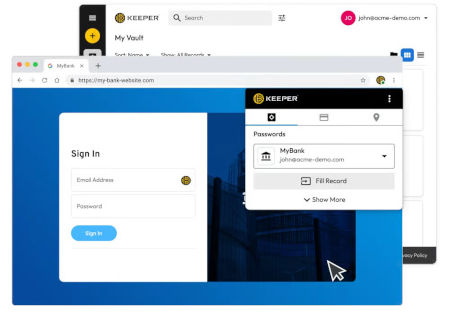
Keep Sensitive Information Confidential
Users can protect, discover, share and rotate passwords, passkeys and confidential data in a zero-knowledge vault with role-based access control, auditing and compliance. Establish cloud and on-prem privileged sessions, create tunnels, power zero-trust infrastructure access and secure remote database access without a VPN. Image courtesy of Keeper Security
Find out more at keepersecurity.com
McAfee
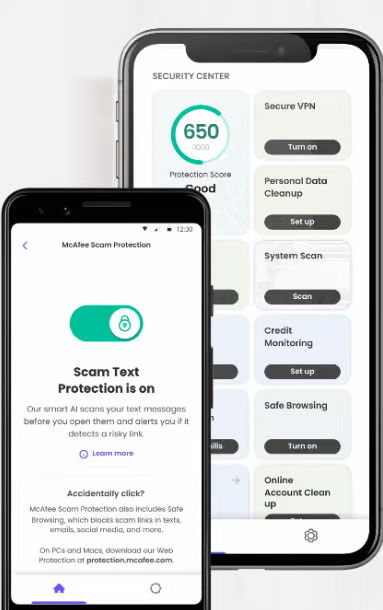
Continuously Detect Phishing Attempts
McAfee scam protection is designed to monitor personal info like email accounts, phone numbers and more. The system will scan any sent links for potential scams and alert users if one is found to prevent phishing attacks. If any breaches are found, the program will notify users and show them potential actions. The system includes anti-virus protection and a virtual private network (VPN) to help protect personal data on mobile devices. Image courtesy of McAfee
Find out more at mcafee.com

SentrySafe
Secure Items During Transport and Travel
The Master Lock Compact Safe from SentrySafe is designed for “on the go” security. The safe is built for small spaces such as vehicles, dorms, campers and boats. It is designed to secure cell phones, wallets, keys, iPods, GPS units and other compact items that are vulnerable to theft. The safe works well for travel when traditional security measures may be unavailable. Image courtesy of SentrySafe
Find out more at sentrysafe.com

Zerify
Block Data Breaches From Anywhere
Zerify Defender is designed to function effectively in a constantly changing threat landscape. Instead of scanning for known risks, Defender stops breaches by securing the devices and processes used by business applications providing protection against known and unknown threats. Protecting cameras from hackers is essential to prevent unauthorized access to confidential information and maintain the privacy of employees and clients. Image courtesy of Zerify
Find out more at zerify.com
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






