Network vs. mobile device management in the age of remote work

Mobile device management (MDM) offers many advantages for protecting devices connected to company networks but also presents drawbacks, including the potential to be undermined by hackers when the managed device joins an unknown network.
A device, a VPN and a network walk into a bar
Many good jokes start with this line, and it is perfect to illustrate the problem with traditional mobile device management operating in the real world. Device management is orderly. VPNs are orderly. Protected company networks are orderly. In a perfect world, these partners would communicate and share information in a carefree and secure environment, without fear of having their privacy breached.
Unfortunately, the real world is messy. Devices connect to protected company networks and assets on unknown and unprotected networks, like the bar Wi-Fi in a hotel. Now this orderly world is vulnerable as the device and VPN communicate over a network territory that is not secure. In many cases, devices are set to automatically connect with an available free Wi-Fi network as a convenience, but it is not without consequence.
The managed device and VPN were fine in their known and protected domain, but once they stepped into the bar and joined the unknown network, they became vulnerable to anyone else in that bar on that network. This is the digital equivalent of leaving your drink unattended, and the hangover you may get from a breach could cost you far more than a night on the town.
The problem runs deep
The network comes into the operating system at a very low level — so low, in fact, that in many ways the operating system is unaware of what it is being exposed to. Operating systems that run our smartphones, laptops and an endless array of cameras, digital doorbells, refrigerators, game systems and Internet of Things (IoT) devices have one thing in common; they all ride on top of the network to which they connect. When this network is unknown and untrusted, the threats are unknown to the operating systems that run these devices. This is the area beyond what MDM solutions can see. It’s the place we call edge territory.
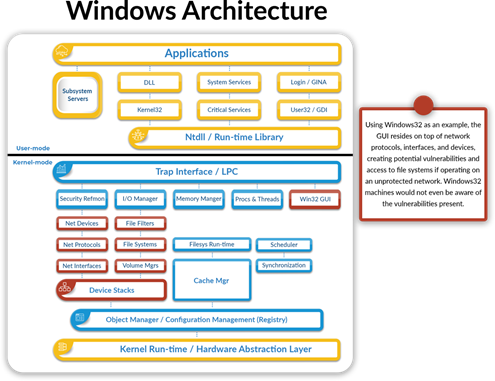 Windows 32 Architecture Example – Source: guardDog.ai
Windows 32 Architecture Example – Source: guardDog.ai
Another problem is that these edge territory networks are possibly hosting many other IoT devices. The majority of these IoT devices are not running Windows or another known operating system. Instead, they are often operating on an embedded and even entirely custom version of Linux. This complicates MDM’s effectiveness because it cannot run agents on these devices.
When we assess this messy situation from a high level, we see an operating system that has no idea what is going on in the network to which it is connected. The device can’t protect itself against all unknown threats. Worse still, a network has no ability to assess its own vulnerabilities. Mobile device management alone cannot meet the needs of a disorderly world.
Unknown networks and asymmetric threats from unseen and seemingly harmless IoT devices can dramatically undermine mobile device management and the information it needs to protect, and these costly intrusions can go undetected for far too long.
The solution is equal to less than zero
There are a couple of interesting challenges MDM faces in truly securing the enterprise. The first is the impossible challenge of deploying management agents on every device. The second important consideration is this: even if you could have agents on every device, can the device be protected before an attack? At best, organizations hope for a zero-day response, or maybe zero plus one. MDM solutions cannot succeed in this circumstance. The answer is turning to threat detection and prevention.
This kind of response requires a network-aware approach that uses an independent overlay working with artificial intelligence (AI) from the cloud to provide managed detection that can autonomously respond to incidents before they affect managed devices and assets. Most managed detection and response providers rely heavily on human resources — and a lot of them. They employ many specialists and invest millions of dollars in 24/7 security operation centers. But this is a realistic choice for most companies, and, if so, could they source the right talent?
What this issue translates to is that companies cannot secure their operations relying on the approaches of the past. They, instead, need to rethink their approach to cybersecurity. The volume of novel exploits is accelerating. The number of devices accessing networks is growing exponentially too, bringing with them an ever-growing number of vulnerabilities for cybercriminals to exploit. What we really need are approaches that can keep up with this changing landscape; that are AI-powered and trained to detect and respond to threats autonomously; and that can leverage a network-aware position to see vulnerabilities and close them before they become problematic.
Not if, but when
To truly protect the enterprise network in today’s distributed environment where an employee could be at the office, at home or on the road, there are many strategies, technologies and tools for defending confidential information from aspiring thieves. There isn’t one solution, such as mobile device management, that can handle every circumstance that emerges from this evolving environment. Furthermore, this isn’t a case of if an attack will happen, but when.
The best strategy is a holistic approach that strengthens cybersecurity in orderly and disorderly environments against threats both known and unknown. The goal is to reduce any attack surface, to seal vulnerabilities as they are discovered to prevent future exploits and to shut down threats in real-time, where possible, to avoid losses, damages to reputation and even regulatory fines for compliance failures.
.webp?height=96&t=1637075091&width=96)