Global Security Exchange (GSX) 2019 Highlights and Products
Abloy’s ABLOY PROTEC2 CLIQTM Connect.

Tyco Cloud from Tyco Security Products.

March Network’s SE4 Outdoor IR Dome.
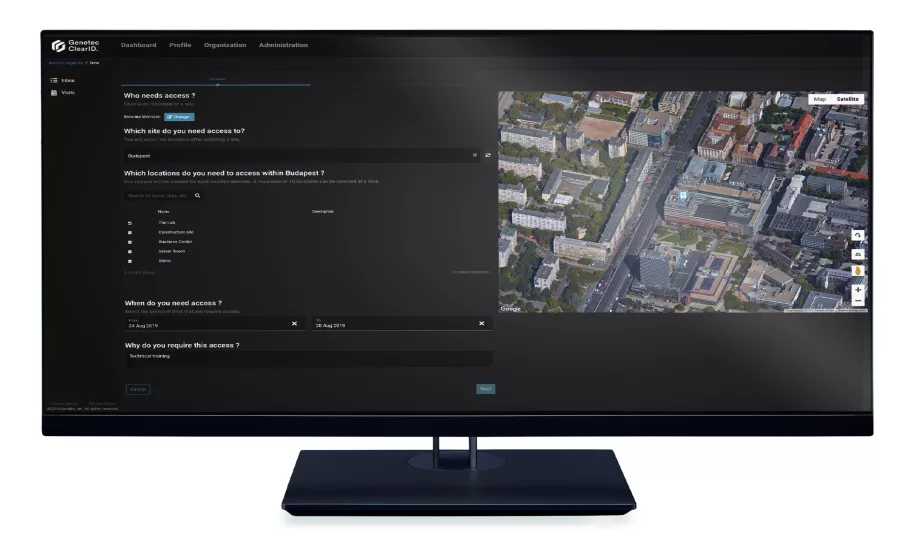
Genetec’s ClearID™.

Boon Edam's Circlelock celebrates 35 years.

Eagle Eye Networks’ Eagle Eye Cloud Video Management System.

AXIS Communications’ Q1700-LE License Plate Camera.

Dortronics’s 4800 Series Door Interlock Controller.

Codelock’s CL4500 and CL5500.

Aiphone’s IX Series 2 Peer-to-Peer Video Intercoms.
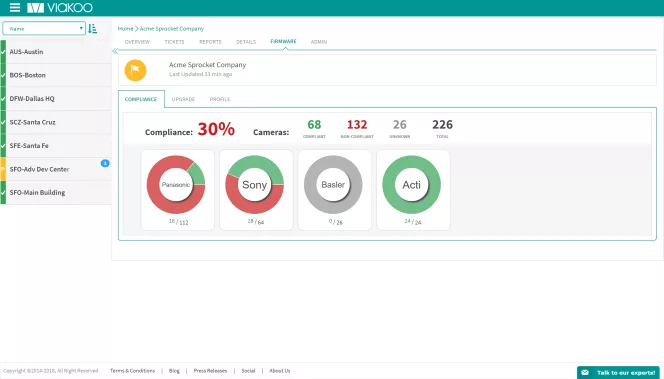
Viakoo’s Video Assurance Service (VAS).

HID Global’s iCLASS SE® RB25F Fingerprint Reader.
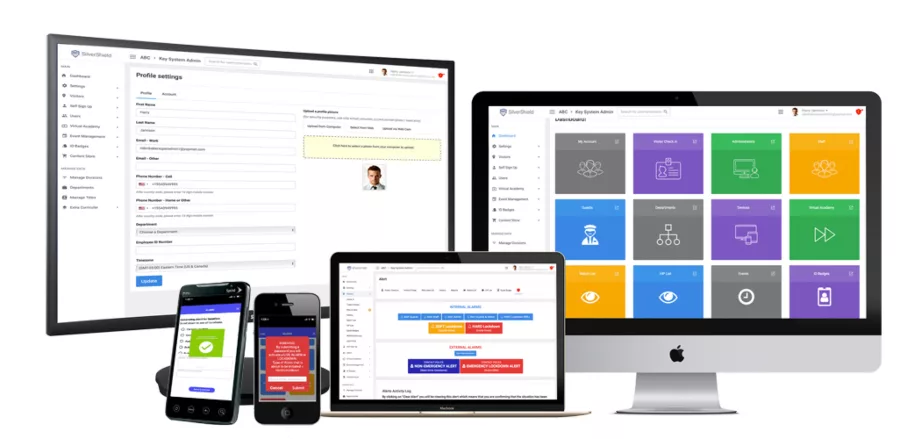
The SilverShield™ Safety & Information Systems software.

Morse Watchmans’ KeyWatcher Touch.
RS2 Technologies’ ACT365 Cloud-based Access Control and Video Management Solution.
The Global Security Exchange (GSX) 2019, held at McCormick Place, Chicago, proved to be a successful educational and networking event for end users, security professionals and more. More than 20,000 registrants from more than 125 countries and more than 550 exhibitors joined the trade floor and the many events that took place since the inauguration on Saturday, September 7 until its closing on Thursday, September 12.
John F. Kelly, retired four-star general, former U.S. Secretary of Homeland Security and White House Chief of Staff, spoke on Military and Law Enforcement Appreciation Day (Wednesday, September 11) about policies, agency structures and more since the terror events of 9/11, and how those changes are possible through the collaboration of public-private partnerships and intelligence and law enforcement agencies.
The general sessions focused on the emerging threat landscape, the importance of cybersecurity and the frequency of cyber-attacks, risk management and crisis preparedness.
This year was also no exception to the display of the latest technologies, services and solutions for enterprises. Below, you’ll find a list of products that were displayed at GSX 2019 that continue to evolve to meet the changing needs of enterprises and adjust to the threat landscape.
The editorial team at Security Magazine looks forward to seeing you at GSX 2020, taking place September 21-23 in Atlanta, Ga.
Addresses Challenges to Critical Infrastructure Facilities
Abloy’s ABLOY PROTEC2 CLIQTM Connect is an access control mobile application for large, geographically challenged organizations such as utilities and corporate enterprises. Managers at a number of utilities, airports, rail transportation, gas and energy companies and municipal water treatment facilities, have the ability to update, amend, renew or revoke access rights remotely from the CLIQ Web Manager software. Mobile workers simply need to open their CLIQ Connect app for the updated access permissions to be instantly transferred to their programmable CLIQ key via Bluetooth. Lost keys can be activated without needing mechanical keying, and both keys and locks provide an audit trail.
Find out more at www.abloyusa.com
Secures all Data from Connected Devices to the Cloud Platform
Tyco Cloud from Tyco Security Products is a cloud-based security suite developed to help customers move security infrastructure for access control and video surveillance to the cloud. With the cloud platform, enterprises can improve security management and scale security operations on demand. Users can protect lives, assets and facilities through management of access control, video surveillance and other security operations using secure cloud services and connected devices such as cloud cameras and controllers. It enables video storage in camera, in gateway, in low latency cloud or a hybrid combination to support flexibility. The interface allows users to customize multiple recording parameters, such as which cameras to record and for how long, video resolution, as well as create unique upload schedules to minimize bandwidth consumption. It also supports heat mapping, object detection and crowd formation.
Find out more at www.tycocloudsolutions.com
Features High Dynamic Range and Built-in IR
March Networks' ME4 Outdoor IR Dome integrates IR LEDs, High Dynamic Range (HDR), P-Iris and 4MP resolution to guarantee clear image quality, regardless of lighting. Additionally, the camera is protected by a weather-proof (IP66), vandal resistant (IK10) enclosure, which generates an alert in the event someone attempts to obstruct or move the camera. Its P-Iris feature enhances video clarity and depth of field, and allows objects close to and far away from the camera to remain in focus, simultaneously. A 4MP resolution allows for twice the amount of pixels as 1080p to view details such as facial features and bill dominations.
Find out more at www.marchnetworks.com
Reduces Challenges Related to Managing Employee, Visitor Access Requests
Genetec’s ClearID™ is a self-service physical identity and access management (PIAM) system that standardizes and enforces security policies to help make organizations more efficient, compliant and secure. The solution enables employees to login to an online portal and make access requests directly to the area owner or supervisor. Employees control their own access requests which ClearID automatically approves, denies or sends to an operator to review. ClearID simplifies the auditing process by providing area owners with an instant view of who has access to their areas, allowing them to quickly revoke access to those who shouldn’t be there, as well as simplify manual processes that are time and resource intense and prone to human error. Additionally, the solution supports organizations in industries where they need to comply with strict access requirements.
Find out more at www.genetec.com
Facilitates Multi-Factor Authentication
Boon Edam’s Circlelock celebrates its 35th Anniversary. First built in 1984, the mantrap portal continues to be used in sensitive facilities, including data centers, government and military buildings and commercial campuses. The portal integrates with any access control system and biometric scanning technologies can be mounted inside the portal on an optional, supportive post. The user can present one credential to enter the portal, which scans the interior to avoid tailgating. The user then presents their face, iris, fingerprint or hand to confirm their identity before the second door opens.
Find out more at www.boonedam.com
Compact Solution Designed to Save Valuable Wall Space
Altronix’s Maximal Fit series of access power controllers provide system designers and integrators with a more compact and economical alternative to their Maximal series. The new models include single or dual power supply/chargers with or without sub-assemblies and accessories to meet a wide range of system requirements. Units can also be customized or pre-installed with myriad combinations. Its power supply features include: supervised fire alarm disconnect, low power cutoff and overvoltage protection, built-in battery chargers that is 30 to 50 percent faster, room to accommodate up to four 12AH/12VDC batteries that are network ready by adding a LINQ2 network communication module to control, monitor and report diagnostics.
Find out more at www.altronix.com
Enhances to Support Fifteen Additional Body Cameras
Eagle Eye Networks’ Eagle Eye Cloud Video Management System (VMS) now supports 15 additional third party mobile and body worn cameras. The VMS provides simultaneous operations, search and cloud storage for fixed and mobile cameras. The Eagle Eye mobile and body worn camera system includes viewing mobile and fixed camera footage in one cohesive interface that eliminates the need for multiple applications, archiving, storage and retrieval of time-stamped mobile footage with GPS coordinates and tracking. The platform ensures secure sharing of video via mp4 files or via direct links to interested parties, provides compatibility with a broad array of cameras and access to a True Cloud system meaning virtually unlimited scalability. It is equipped with triple redundant data center architecture, full encrypted video and comprehensive cybersecurity.
Find out more at www.een.com
License Plate Camera for Capturing Clear Images
AXIS Communications’ Q1700-LE License Plate Camera captures vehicle images with clarity by ensuring the required pixel density for license plate identification in one lane traffic at a range of up to 328 ft. during daytime and up to 164 ft. at nighttime. Its robust design allows for reliable operation in extreme weather conditions. The built-in license plate capture assistant allows for customizable and optimized settings in a specific traffic scene. It enables horizontal field of view of 16˚ to 2.3˚ and allows for use with third-party license plate recognition software. The solution is compatible with Axis Camera Station and can be used with server-based or edge analytics from most third-party vendors to perform further analysis of recorded or live material.
Find out more at www.axis.com
Accommodates Up to Five Doors
Dortronics’s 4800 Series Door Interlock Controller accommodates up to five doors, including doors with automatics openers. The unit’s 17 outputs control door locks, traffic lights and mirror door status with alarm outputs with a long list of features that includes adjustable timers for propped door time, panic release unlock time and unlock pause time for Request-to-Exit unlock time. Additional features include 12 inputs for door status, request for access, interlock override and emergency unlock. A watchdog circuit to monitor operation, LED input/output status indication and voltage spike/surge protection are included, as well.
Find out more at www.dortronics.com
Offers Advanced Programming and Access Methods
Codelock’s CL4500 and CL5500 guarantee keyless entry, which helps prevents risks associated with lost keys. It includes a 12 button back-lit keypad, NetCode generation technology, Tubular Latch, Mortise Lock and Panic Kit. Its keypad indicates a “locked” or “unlocked” status with tamper time out and low battery warnings. It allows for auxiliary connections that enable four modes of operation, including remote release, sensor mode, sensor and alert and unlock and lock down modes. It enables the locks to be fully operated and managed via smartphones.
Find out more at www.codelocks.com
Creates Safer Buildings with Increased System Flexibility
Aiphone’s IX Series 2 Peer-to-Peer Video Intercoms offer Session Initiation Protocol (SIP) compatibility, and enhances video surveillance control, line supervision, backwards compatibility with the original IX Series and many more features. End users can create efficient security operations centers (SOCs) using the system as a single command point to control a variety of security layers. The intercom solution can page across multiple stations with general or emergency announcements and scan through video intercoms and video surveillance cameras to monitor locations.
Find out more at www.aiphone.com
Improves Physical Security through Video Surveillance
Viakoo’s Video Assurance Service (VAS) is a managed service offering that provides the benefits of service assurance to physical security teams of all sizes. VAS installs software agents on the end user system, which are monitored to ensure video is being recorded and stored properly. If an issue is detected, the system automatically diagnoses the root cause and develops a repair plan for the integrator to resolve the problem, in many cases even before there is any impact on video recording.
Find out more at www.viakoo.com
Allows for Reliable Biometric Authentication
HID Global’s iCLASS SE® RB25F Fingerprint Reader brings reliable biometrics authentication to the door with HID Global’s multispectral imaging technology to provide high-performance image capture and fingerprint matching in under a second. It captures images from both the surface and sub-surface of the skin with liveness detection under all extreme weather conditions. The reader maximizes security with built-in optical tamper protection and in support of Open Supervised Device Protocol (OSDP), as well as HID Global’s Seos technology. It is field programmable and can be used with all popular industry-standard high frequency credential technologies.
Find out more at https://www.hidglobal.com/
Creates Safer Environments for Students, Staff and More
The SilverShield™ Safety & Information Systems software incorporates a fully-integrated suite of modules including visitor management, lockdown initiation, incident management, event management, virtual academy, Kiosk and the HR & Safety Resource Center. Originally developed for school campus applications, the software enables manned or unmanned visitor screening at all types of facilities where users can check visitors’ credentials against watch lists and the national sex offender database. If the system identifies a threat at an entrance, it immediately sends silent alerts. The software allows temporary ID badges to be created for staff, students, volunteers and vendors. Alerts are sent to local police to initiate a virtual lockdown procedures where mass emergency notifications via email, SMS/text, mobile and web push notifications are sent.
Find out more at www.silvershield.com
Offers Remote Diagnostics and Servicing Capabilities
RS2 Technologies’ ACT365 Cloud-based Access Control and Video Management Solution (VMS) provides both access control and video management in a web-based platform that allows users to quickly update or remove user permissions, view cameras or open a door directly from a mobile phone, tablet or PC. The scalable solution offers management of multiple sites from a single, unified and user-friendly interface without the added expense of local servers and IT resources. There is no software to install and updates are automatic, which ensures delivery of the most up-to-date, secure version of the system.
Find out more at www.rs2tech.com
Tracks Usage of Keys and Physical Assets
Morse Watchmans’ KeyWatcher Touch key management system features a 7” touchscreen with an easy-to-use interface and SmartKey system with KeyAnywhere technology to make it simple to remove and return a key to any key cabinet in an enterprise. New features to KeyWatcher Touch include remote functions added to the TrueTouch Software that supports multiple user logins for key returns and removals. A new “Key Group Associations” feature allows users more specific key access to be configured directly through the access control system. This feature makes it easier for users to cover special situations, such as when an employee is out of the office that day, or if they fit the criteria for a specific profile, but they temporarily need some additional keys.
Find out more at www.morsewatchmans.com