Global News
Addressing the cybersecurity workforce staff shortage

sanjeri / E+ via Getty Images
(ISC)² estimates the global cybersecurity workforce in 2022 to be 4.7 million, an 11.1% increase over last year, representing an additional gap of 464,000 more jobs, according to the fifth annual (ISC)² Cybersecurity Workforce Study.
The study surveyed 11,779 international practitioners and decision-makers to gain insights into working in the modern cybersecurity profession. This report highlights hiring and recruiting trends, corporate culture and job satisfaction, career pathways, certifications, professional development, how the workforce is adapting to current events, and what the future of cybersecurity work looks like.
To calculate a global workforce estimate and gap, (ISC)² uses a proprietary methodology that integrates primary and secondary data sources to extrapolate the number of workers responsible for securing their organizations.
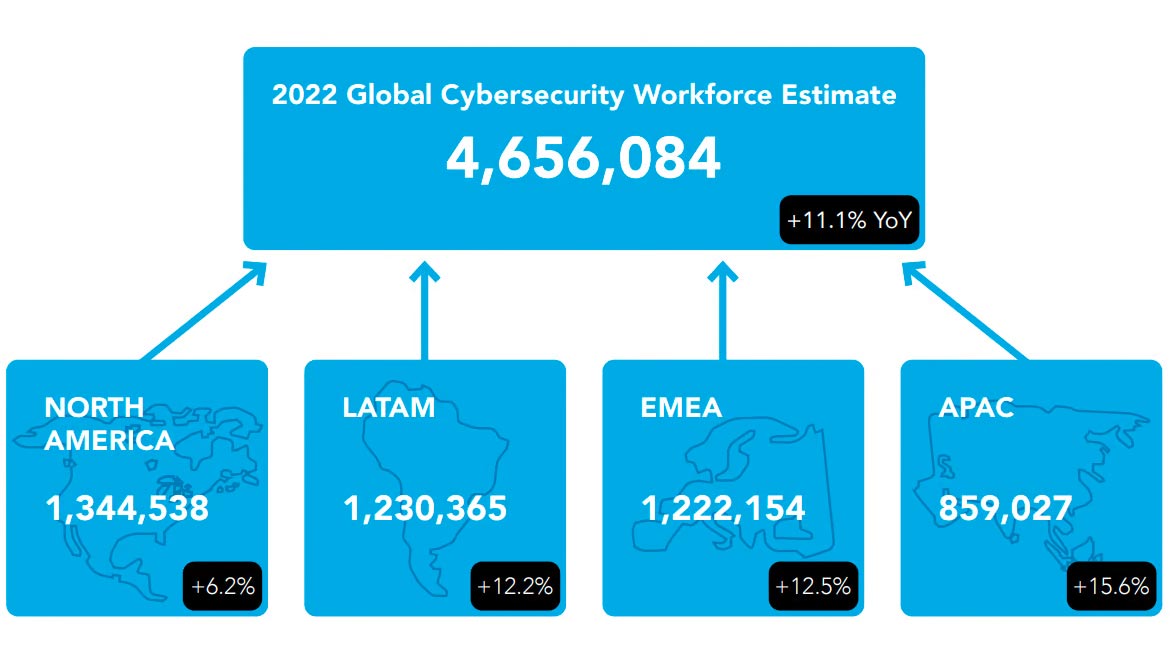
*Click the image for greater detail
The organization observed growth in cybersecurity positions across all regions, with Asia-Pacific (APAC) registering the most significant growth (15.6%) and North America the least (6.2%).
While the cybersecurity workforce is multiplying, the number of positions to fill is increasing even faster. (ISC)²’s workforce gap analysis indicated that despite adding over 464,000 workers in the past year, the gap has grown twice as much as the workforce, with a 26.2% year-over-year increase.
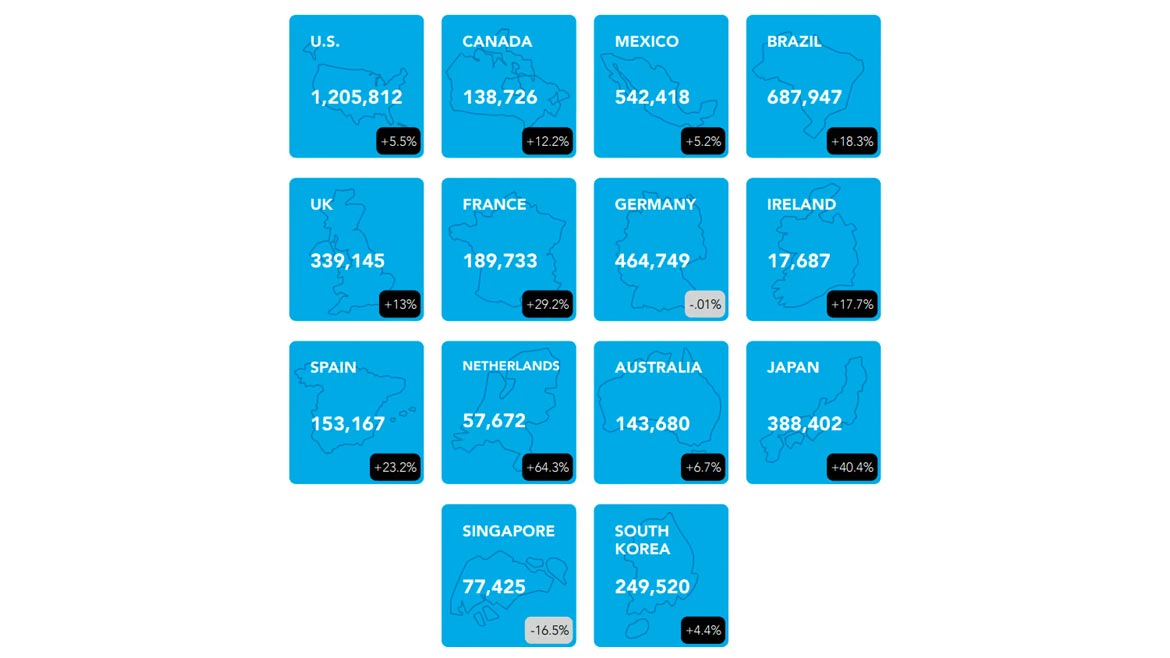
*Click the image for greater detail
Approximately 70% of cybersecurity workers feel their organization doesn’t have enough cybersecurity staff to be effective. The shortage is especially severe in the aerospace, government, education, insurance and transportation sectors.
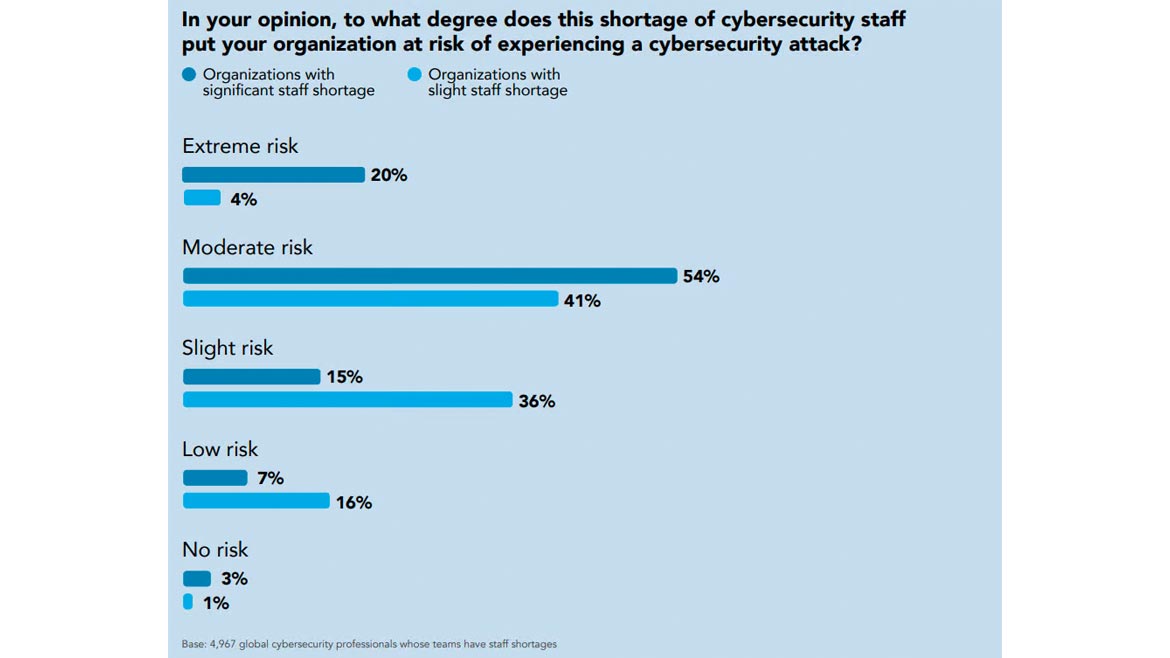
*Click the image for greater detail
A cybersecurity workforce gap threatens the most foundational functions of the profession, such risk assessment, oversight and critical systems patching, according to the study. More than half of employees at organizations with workforce shortages feel that staff deficits put their organization at a “moderate” or “extreme” risk of cyberattacks. In addition, that risk increases substantially when organizations have a significant staffing shortage.
Compared with last year’s report, more cybersecurity professionals indicated that their organization encountered issues, such as a lack of proper time for assessment and oversight of processes, slow patching of critical systems and inadequate time and resources for training due to staffing shortages.
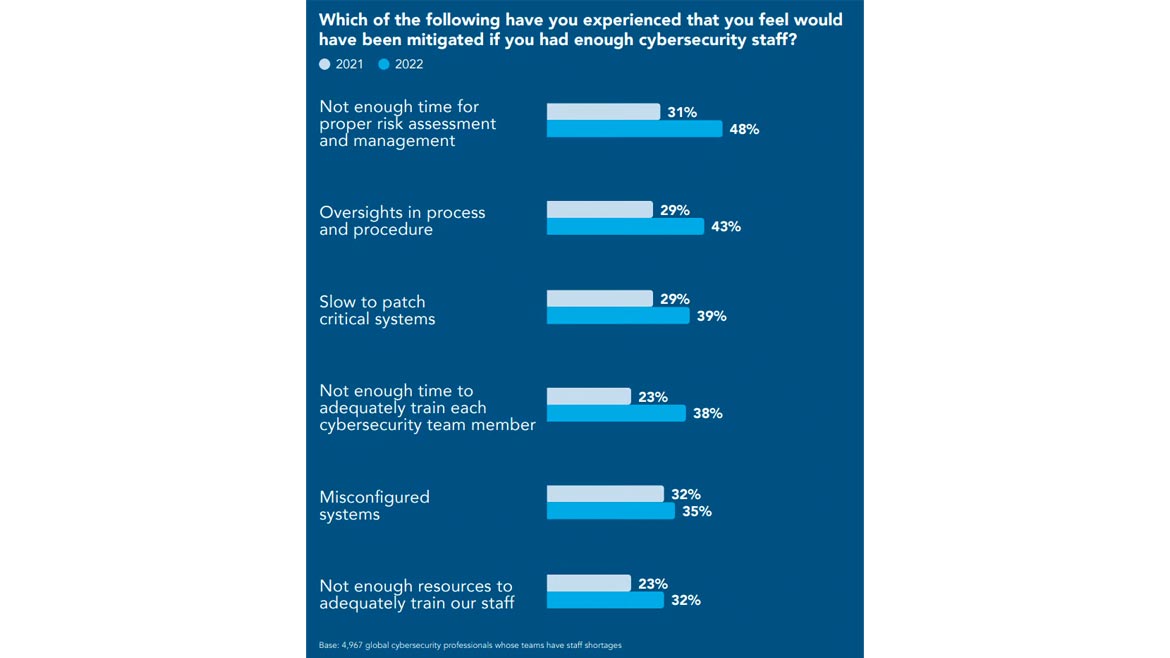
*Click the image for greater detail
Addressing the Cyber Workforce Gap
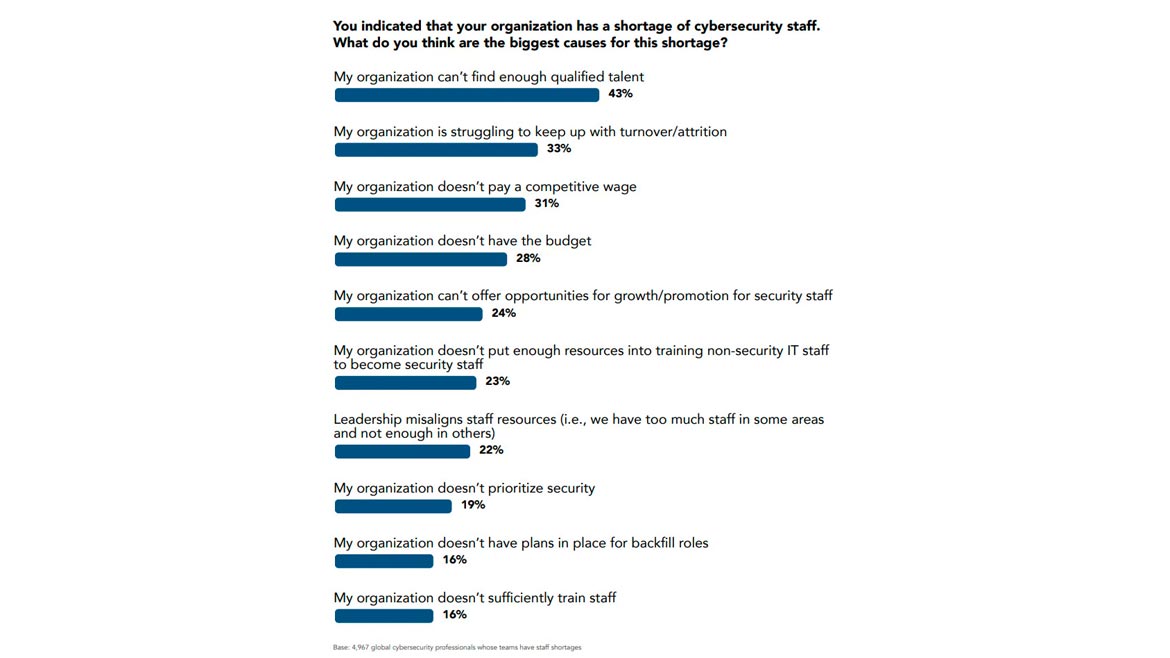
Why does this workforce gap exist? How can organizations best mitigate it? Some factors are out of an organization’s control — demand for cybersecurity employees is bound to increase as the threat landscape continues to grow, and supply can’t always keep up. The inability to find qualified talent was cited most frequently as a challenge by organizations with cybersecurity staff shortages. While this may be the most common challenge, it is not the most impactful.
To better understand what challenges are linked to the biggest staffing shortages, (ISC)² examined what percentage of employees at organizations with those issues had significant staffing shortages. This analysis suggests that the most negatively impactful issues are ones that organizations can control: not prioritizing cybersecurity and not training staff or offering opportunities for growth or promotion. However, finding qualified talent was the least impactful problem based on this analysis.
While organizations attempt to mitigate staff shortages, it’s not always effective. Although almost all initiatives positively impacted staffing, the study found that organizations with initiatives to train internal talent — rotating job assignments, mentorship programs and encouraging employees outside of cybersecurity to join the field — were least likely to have shortages.
These initiatives are particularly impactful for larger companies — only 49% of companies with 1,000 or more employees who had implemented all three internal training initiatives had staffing shortages compared with 77% of those who had implemented none.
*Click the image for greater detail
However, internal trainings were not the most commonly adopted initiatives. Many of the most effective initiatives had the lowest implementation levels. The initiative with the lowest impact is outsourcing. Respondents at organizations that were outsourcing cybersecurity were slightly more likely to see a shortage in staff.
Automation is becoming more prevalent in cybersecurity as well — 57% have adopted it, and 26% plan to adopt it in the future. While it isn’t likely to replace cybersecurity workers at any time in the foreseeable future, automating consistent and repeatable processes frees workers to focus on higher-level tasks. This may, in turn, reduce staffing shortage issues without requiring additional staff.
The study found that cybersecurity hiring managers with a strong working relationship with their human resources (HR) department were far less likely to have significant staffing shortages at their organizations. However, only 52% of respondents said that hiring managers have a strong working relationship with HR, and 40% of hiring managers said that the HR department at their organization does not add value to the recruiting process.
What the Cyber Workforce Gap Means for Organizations
Combatting staffing shortages is no easy task, but there are three key places where organizations can focus:
- Understand what your gap is. Senior-level practitioners in the study were more likely than managers or executives to say their organization had a staffing shortage. This suggests that those making decisions may not always fully appreciate what frontline cybersecurity professionals are experiencing. Decision-makers should make sure they are actively listening to employees to understand if and where there are staffing shortages.
- Emphasize internal training. The most impactful organizational initiatives in reducing worker shortages were those that took advantage of internal talent with programs such as rotational job assignments, mentorship and encouraging non-IT employees at the organization to learn about cybersecurity. The challenges that were most associated with high staffing shortages were a lack of emphasis organization-wide on cybersecurity, insufficient staff training and a lack of pathways for growth.
- Work with HR, not against them, when hiring for cybersecurity. Hiring is a challenging process. While cybersecurity hiring managers know best what candidates to look for, HR managers are more likely to have the expertise to find and attract those candidates. Therefore, cybersecurity organizations need to build effective working relationships with HR or risk having significant staffing shortages compared with those who have built a strong relationship with HR.
For more information, visit www.isc2.org.
Images courtesy of (ISC)²
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






