Global News
6 strategies to reduce workplace violence risk

erhui1979 / DigitalVision Vectors via Getty Images
Workplace violence is on the rise — yet approximately 50% of U.S. employers are unprepared to prevent and respond to incidents that occur during the work day, according to the National Safety Council’s “Workplace Violence: Using Technology to Reduce Risk” report.
The report examines data from the most recent Bureau of Labor Statistics (BLS) 2021 report and data from the National Crime Victimization Survey (NCVS), which relies on self-reported victimization data collected by the Bureau of Justice Statistics (BJS).
According to the most up-to-date data from the BLS, in the past decade, workplace violence has taken the lives of 788 U.S. workers per year, on average (see Figure 1). Homicides claim the lives of 443 workers per year, while another 273 die of unintentional, work-related or self-inflicted injuries per year.
In 2020 alone, 705 workplace fatalities occurred, the BLS reports. This represented the first year-over-year decrease since 2017, although report authors say this is likely due, in part, to the economic disruptions triggered by the COVID-19 pandemic.
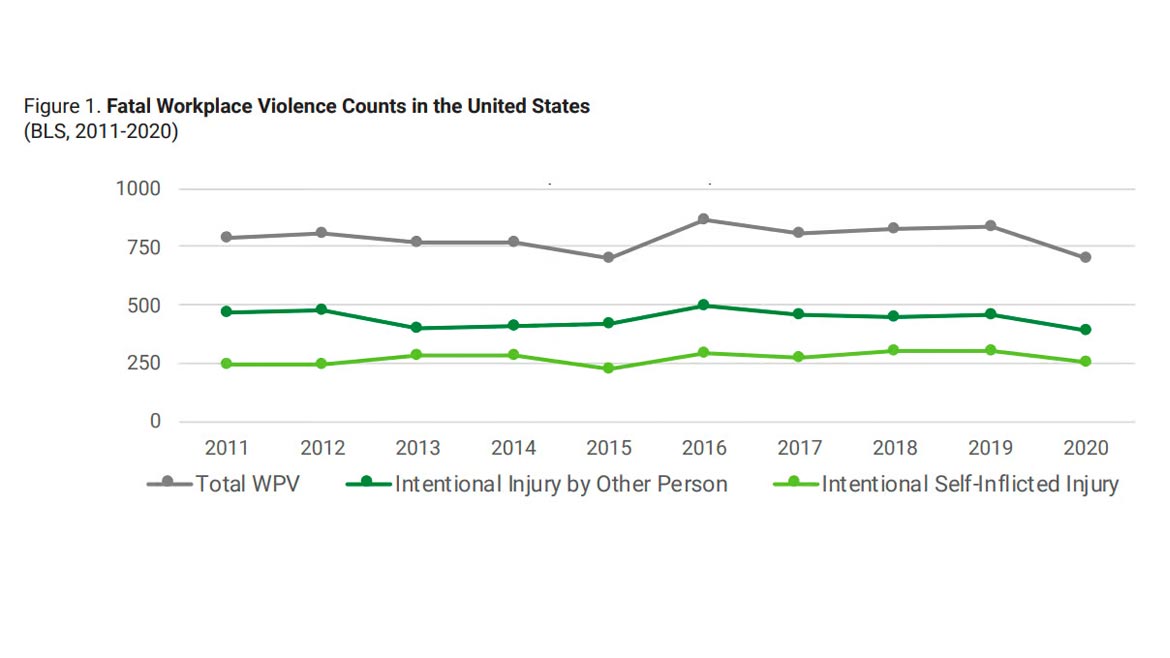
Image courtesy of National Safety Council
Between 2011 and 2020, there were over 16,700 reported incidents of workplace violence — a rate of about 1.7 assaults for every 1,000 workers, the BLS data shows. In 2020, an estimated 20,050 workers suffered injuries from violence on the job, about 2.1 assaults per 1,000 workers — an increase from a rate of 2.0 in 2019, according to the BLS.
While the official BLS reports put the 10-year average at about 16,700 injuries, NCVS estimates more than 761,000 injuries occur each year. However, both datasets indicate that the overall rate of workplace violence is trending upward (see Figure 2), which highlights the need to enhance violence prevention plans across all industries.
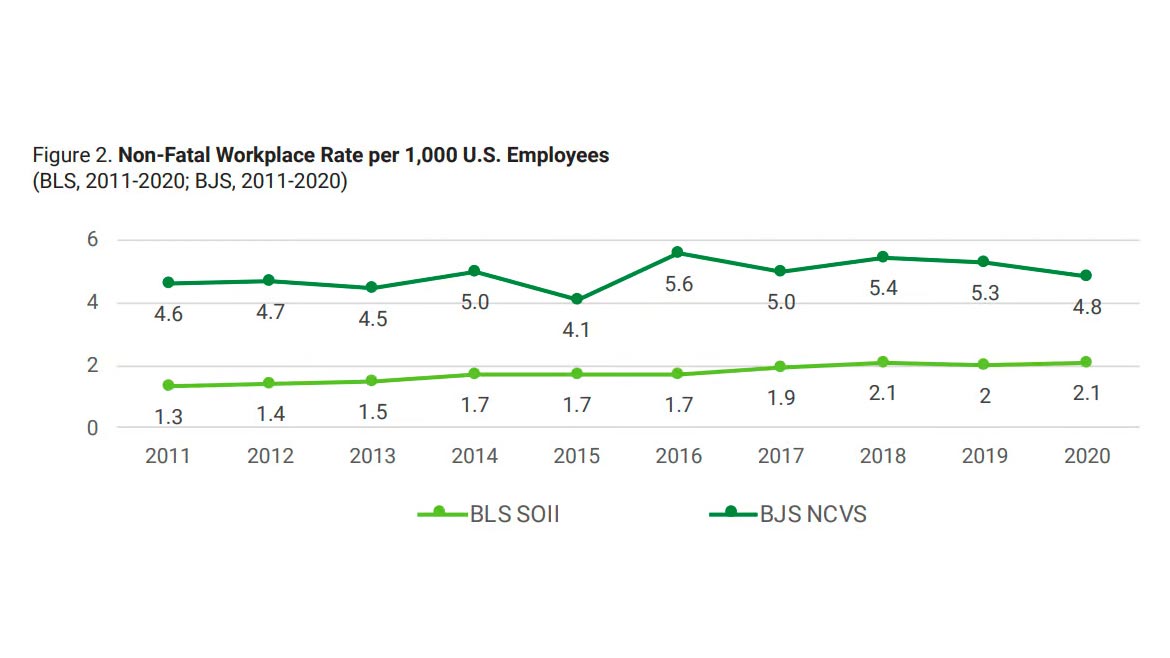
Image courtesy of National Safety Council
Workplace violence risk management can be approached in the same manner as other safety and health programs, utilizing a well-rounded approach rooted in hazard prevention strategies, which include a written workplace violence policy, employee training and administrative security controls to prevent or mitigate the risk of an incident.
For effective risk management, the National Safety Council proposes a workplace violence prevention plan. Beyond reducing the risk for violence, a prevention plan has several benefits, including: increased feelings of safety, increased reporting confidence, higher levels of job satisfaction, reduced insurance costs, and stronger organizational safety culture.
The plan offers seven steps to address workplace violence in organizations and, in turn, provide a safe workplace for all employees.
1. Identify a workplace violence prevention taskforce and include the right people in the conversations.
Organizations may want to include representatives across departments, including Security, Safety, IT, HR and Employee Assistance Program Managers, and include employees from varying levels of responsibility, emphasizing those performing the highest-risk job duties.
If your site does not have these specific departments, reach out to those responsible for performing those duties. If working with consultants or third-party vendors, request the applicable information necessary to complete the following steps.
2. Prepare a working policy and workplace violence prevention plan and get workforce feedback on the organization’s position.
Security leaders and their organizations should understand if you work in a state with workplace violence provisions. For example:
- California, Connecticut, Illinois, Maine, Maryland, Minnesota, Nevada, New Jersey, Oregon and Washington require healthcare facilities to develop, implement and periodically evaluate a workplace violence prevention plan.
- New Mexico and New York require employers in convenience stores or all public employers to have security controls to prevent violence.
- Hawaii and Ohio provide suggestions/guidelines to reduce violence in the workplace.
Next, regularly review the program and determine its effectiveness. Evaluate the program through tabletop exercises or simulations involving emergency response personnel (e.g., law enforcement, local officials and internal security), and utilize the program as a guideline during workplace violence response drills. Reach out to local law enforcement and/or a third-party consultant to help develop these exercises.
Using the results from tabletop exercises can help uncover and address weaknesses in workplace violence prevention plans, such as gaps in security protocols, clarity around individual responsibilities or missing links in the chain of command.
Utilizing indicators as a screening tool for HR complaints and incident investigations can also help prevent violent events. Indicators can include a history of violent or criminal behavior, verbal abuse and bullying, drug or alcohol abuse, social isolation, etc.
3. Understand if the characteristics of your organization increase the risk of a workplace violence event.
Organizations can utilize the National Safety Council’s Site Workplace Violence Risk Assessment and Auditing Tool to further understand if they are at risk of violent events. If corrective actions are needed, utilizing recommendations in Step 4 can help security stakeholders find potential solutions and assign an action-item owner to investigate.
Reviewing the following documents may be helpful during this process:
- Employee Engagement Surveys: If not already completed, introduce this survey system to your organization to better understand the overall culture.
- Site Records/Metrics: Collect information, such as HR files/grievances, injury reports, overtime/turnover reports and legal restrictions between coworkers (restraining orders, etc.).
4. Explore technology solutions that could reduce the risk of a hazardous situation in your workplace.
Choose solutions that will remedy risk factors identified during the assessment for the most effective approach. Be sure to focus on a full-spectrum approach, including solutions that help to prevent, mitigate and react to workplace violence.
These technologies may include:
Prevention-based technology
- Virtual reality and digital training: Virtual training modules can include engineering and administrative controls; recognizing warning signs; de-escalation tactics; incident reporting; emergency response procedures.
- Social media listening/screening: This technology can help screen applicants for employment; flag direct or indirect threats to an organization; and monitor potentially dangerous situations (e.g., political unrest, severe weather, mass violence).
- Access control: Applications can include visitor management systems (e.g., ID badges), security gates, alarm systems, emergency lockdown systems, biometric readers and metal detectors.
- Weapons detection: Such technology can help with visitor and employee screening, early detection, and threat response.
- Audio/video analytics: This software can help flag visual signs of violence (e.g., weapon detection, fighting, running, fall detection, loitering, etc.); audible signs of violence (e.g., gunshots, glass breaking, car alarms, verbal aggression, etc.); and enable digital fencing, facial recognition, and license plate readers.
Mitigation-based technology
- Lone or downed worker monitoring: Applications can include monitoring employees working alone or in potentially dangerous situations such as remote or isolated locations, fieldwork, overnight shifts, in patient/customer homes and other high-risk environments (e.g., corrections, mental health facilities, hospitals, etc.).
- Panic/duress buttons: This technology can help send discrete SOS alerts in emergencies, such as verbal or physical altercations, robbery, hostage situations, trespassing or break-ins, and mass violence.
- Camera systems: Video surveillance applications can aid in monitoring entry-exit, manual or digital assessment of warning flags (e.g., fighting, falls, running, brandishing weapons, etc.), deterrence of potential violence and investigations.
Reaction-based technology
- Intelligent case management: These software solutions can help detect red-flag behavior indicators, capture and record complaints, corrective actions, terminations and policy violations, track investigations and generate reports.
- Digital floorplan and mapping: This software application can help to facilitate an organization’s emergency response plan, including route assignments, employee training and first responder navigation.
5. After identifying security technology that can reduce the risk of workplace violence, determine if you’re ready to address the issue digitally.
A workplace violence taskforce in the organization should collaborate to complete the readiness assessment. To identify your organization’s readiness level when it comes to safety technology, utilize this assessment.
Security leaders can inspire trust by engaging employees in co-defining the purposes and need for change and new technology. This can help people see innovation as an opportunity rather than a threat, thus fostering readiness.
After determining which control may be most effective for your risks, use an investment calculator to make the business case. A calculator can allow a company to compare the costs of “business-as-usual” and investment in optimized operations using safety technology.
6. When you’re ready to utilize technology in your organization, follow the pilot and implementation roadmap to facilitate the process.
Several steps exist to assist employers on their innovation journey to prepare for piloting or implementing safety technology. Simply implementing technology does not constitute a successful digital transformation.
An enterprise-wide risk mitigation program, aided by security technology, can help effectively mitigate and address workplace violence.
To view more insights, visit nsc.org.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!







