Global News
6 emerging threats and trends in venue security

simonkr / E+ via Getty Images
What unique challenges does the sporting world face when returning to play following a global pandemic?
The National Center for Spectator Sports Safety and Security (NCS4) “Venue Security Director Survey” shows that many leagues, teams and venues are exploring a number of methods to maintain or improve their security operations.
Conducted in April and May 2022, the report surveyed venue security directors hosting professional sports teams from Major League Baseball, Major League Soccer, the National Basketball Association, the National Football League and the National Hockey League.
The survey revealed several key trends around:
- Staffing and training
- Fan behavior
- Technology utilization
- Patron screening
- Cybersecurity
- Drone mitigation
Let’s explore some of the findings within the key trends.
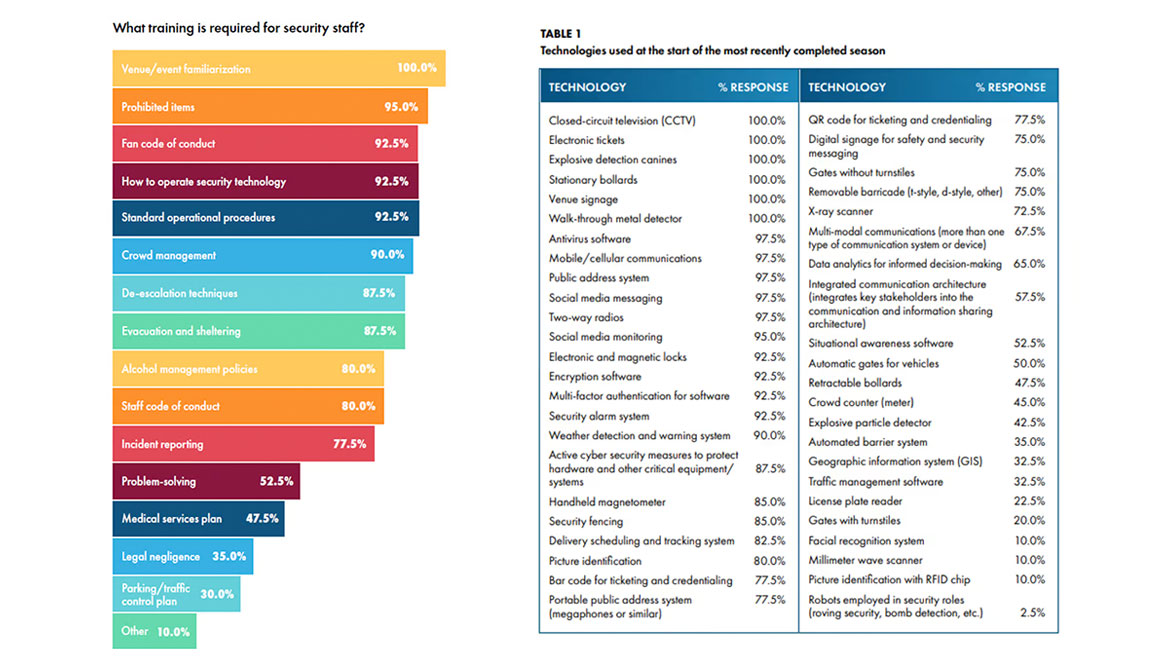
1. Staffing and training
- Contracts: Approximately 90% of venues utilize a third-party service provider for security staff, with the majority (67.5%) contracting 75-100% of their security staff.
- Background checks: All venues, according to respondents, require background checks on contracted security staff, and most venues (97.5%) require them on all full-time staff.
- Staff shortages: Most venues (95%) experienced security staff shortages in the last two years, and 70% of respondents indicated that absenteeism among security staff has increased since the pandemic.
To mitigate the effects of staff shortages, 91.9% of venue directors increased the hourly wage. Other actions included awarding a bonus per event, enhancing employee recognition, providing gift cards for referrals and job performance, hiring more third-party staff, utilizing security screening technology, establishing mutual aid agreements and leveraging out-of-town resources.
- Training: All respondents indicated that venue/event familiarization is required training for security staff. Other types of training include guest services, on-field emergency response, STOP THE BLEED and active shooter.
Facilitated in-person training is the most common training method used (97.5%), followed by tabletop exercises (82.5%), routine refresher courses (67.5%), e-learning (62.5%), workshops (7.5%), and other activities, such as drills and virtual PowerPoints via Zoom (5%).
Images courtesy of (NCS4)
2. Fan Behavior
- The COVID-19 effect: Most respondents (65%) indicated that fan behavior today is much worse or worse than it was 10 years ago, and 65% of participants stated that COVID-19 restrictions caused increased tensions between patrons and staff.
- Concerning fan behavior: The most prevalent form of inappropriate fan behavior is alcohol abuse (82.5%), followed closely by fights between patrons (80%). Respondents indicated that fights between patrons (72.5%), violence against staff members (60%), and use of weapons (47.5%) are the most concerning fan behaviors. Additional concerning fan behaviors included those related to cannabis.
- Crowd management: Crowd management strategies include an established alcohol policy (100%), signage (97.5%), public address announcements (95%), barriers (92.5%), and event staff directing crowd movement (90%). Other crowd management strategies include CCTV and a fan text system.
All respondents indicated that they maintain a central information system for documenting incidents, and 80% conduct research or statistical analysis on the incident data. Approximately 92.5% of participants use industry research and data to inform their venues’ safety and security policies and operations.
3. Security Technology
The survey polled respondents on the use of technologies employed at venues and facilities, as technology can help bolster safety and security efforts.
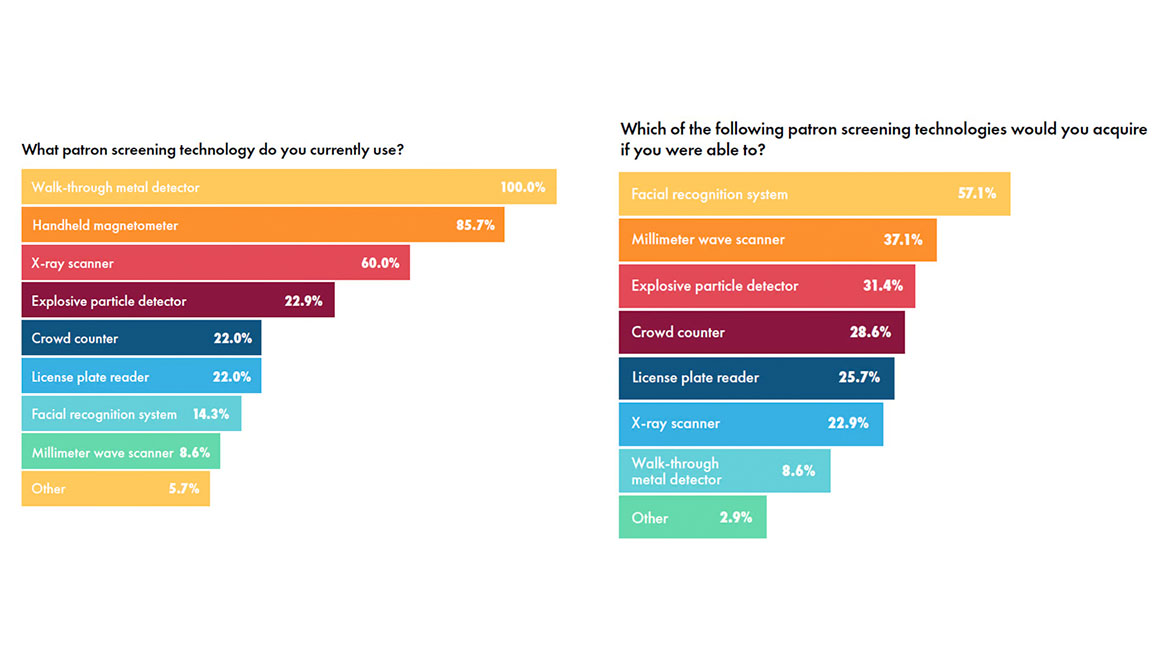
The survey also asked venue security directors to describe the technologies and analytical tools they would purchase with additional funding. Facial recognition systems (37.5%), license plate readers (32.5%), RFID staff identification (30%), retractable bollards (27.5%), automated barrier systems (25%), and x-ray scanner capabilities (22.5%) were among the most sought-after resources.
4. Patron Screening
- Wait time: Approximately 87.5% of participants stated that their current entry screening checkpoint caused lines to form outside their venues. The average wait time at security checkpoints during the busiest time before an event was less than 10 minutes (75%), followed by 10 to 20 minutes (25%). About one-third of participants (32.5%) experienced security incidents between patrons waiting to enter the venue.
- Technology: Most participants (87.5%) use patron screening technology. Walk-through metal detectors (100%), handheld magnetometers (85.7%), and x-ray scanners (60%) are the most commonly employed technologies.
Images courtesy of (NCS4)
5. Cybersecurity
Most respondents (87.5%) have an active cybersecurity defense program and 85% provide basic cybersecurity awareness training to full-time staff.
6. Drone Mitigation
The majority of participants (82.5%) have a drone mitigation plan, and 82.5% have observed or detected unauthorized drone operations in the airspace above or near their venues. Event operations are interrupted occasionally, with one past reported instance when an evacuation or protective action was required.
Security Best Practices
Information gleaned from this study can help assist venue directors in policy development, increase awareness of technology solutions, identify security resource needs, and address training gaps to help protect human, physical, and cyber assets.
To help increase venue safety and security, NCS4 recommends taking the following steps:
- Conduct background checks on all staff, especially individuals with access to restricted areas or privy to sensitive information.
- Require de-escalation, crowd management and active shooter training for event staff.
- Engage with TEAM Coalition or TIPS for alcohol management training and responsible consumer campaigns.
- Offer in-person training supplemented by e-learning programs. Training requirements should be determined for all staff and account for organizational and discipline-specific training needs. Initial and refresher training opportunities should be provided at regular intervals.
- Explore incentives for security staff to increase hiring and retention numbers (i.e. increased hourly wages, rewards programs, complimentary food and discounted ticket prices).
- Clearly communicate venue and spectator policies.
- Discuss the feasibility of adding resources with executive leadership, including facial recognition, license plate readers, RFID staff identification, retractable bollards, automated barrier systems, millimeter wave scanners and explosive particle detector capabilities.
- Explore patron screening technology options that best fit operational needs and budget.
- Implement a drone mitigation program and work with local/state authorities on drone intrusion response procedures. Consider using drone detection technology.
- Benchmark with peers and continue to leverage research and industry resources to inform plans, policies and procedures.
For the full report and additional resources, visit www.ncs4.usm.edu.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






