Global News
Key traits of security leaders in cyber resilience

YiuCheung / iStock / Getty Images Plus / via Getty Images
Based on a survey of more than 4,700 executives globally, Accenture’s State of Cybersecurity Resilience 2021 study explores different types of leaders in cyber resilience. Due to the rapid increase in high-profile attacks and the sheer complexity of handling cybersecurity demands, Accenture also tested what difference it made to cyber resilience if there was a stronger alignment between cybersecurity practices and business strategy.
A cyber resilient business brings together the capabilities of cybersecurity, business continuity and enterprise resilience while embedding security across the business ecosystem and applying fluid security strategies to respond quickly to threats, so it can minimize the damage and continue to operate under attack. As a result, the cyber resilient business can securely introduce innovative offerings and business models across the entire value chain, strengthen customer trust, and grow with confidence, Accenture says.
Accenture’s research identified four levels of cyber resilience: The Vulnerable, Business Blockers, Cyber Risk Takers and Cyber Champions.
Accenture also explored how winning organizations tackle cyber resilience, evaluating their responses based on the following performance criteria: they stop more attacks, find and fix breaches faster and reduce breach impact.
The Vulnerable
The Vulnerable stand to reduce their cost of breaches by 71% if they increase their performance to Cyber Champion levels.
Cyber Champions, Business Blockers, and Cyber Risk Takers outperform The Vulnerable across most key cyber resilience measures. They experience more breaches, take longer to find and fix breaches, and lag in reducing breach impact.
Business Blockers
Business Blockers outperform Cyber Risk Takers and The Vulnerable, but fall behind Cyber Champions across all key cyber resilience measures. They experience fewer breaches than Cyber Risk Takers and The Vulnerable, but 8% more than Cyber Champions (17%).
When it comes to the average share of significant attacks — with high-profile, severe and long-term impact on the organization’s business or mission — they experience fewer attacks than Cyber Risk Takers or The Vulnerable, but nearly twice more than Cyber Champions.
And when attacks get through, Business Blockers detect and remediate them more quickly than Cyber Risk Takers and The Vulnerable, but fall behind Cyber Champions by a day on both measures.
Business Blockers also have the highest percentage of chief information security officers (CISOs) with full authority to approve budgets (32%) versus Cyber Champions (21%), Cyber Risk Takers (21%) and The Vulnerable (16%). This CISO-driven spending autonomy may explain the increased focus on cybersecurity over business strategy.
Business Blockers could reduce costs by 48% per successful attack if they increased their performance to Cyber Champion levels, with savings of about $294,000 per attack.
If Business Blockers add alignment to their already-robust cybersecurity foundation, they will have even stronger cyber resilience without sacrificing business outcomes.
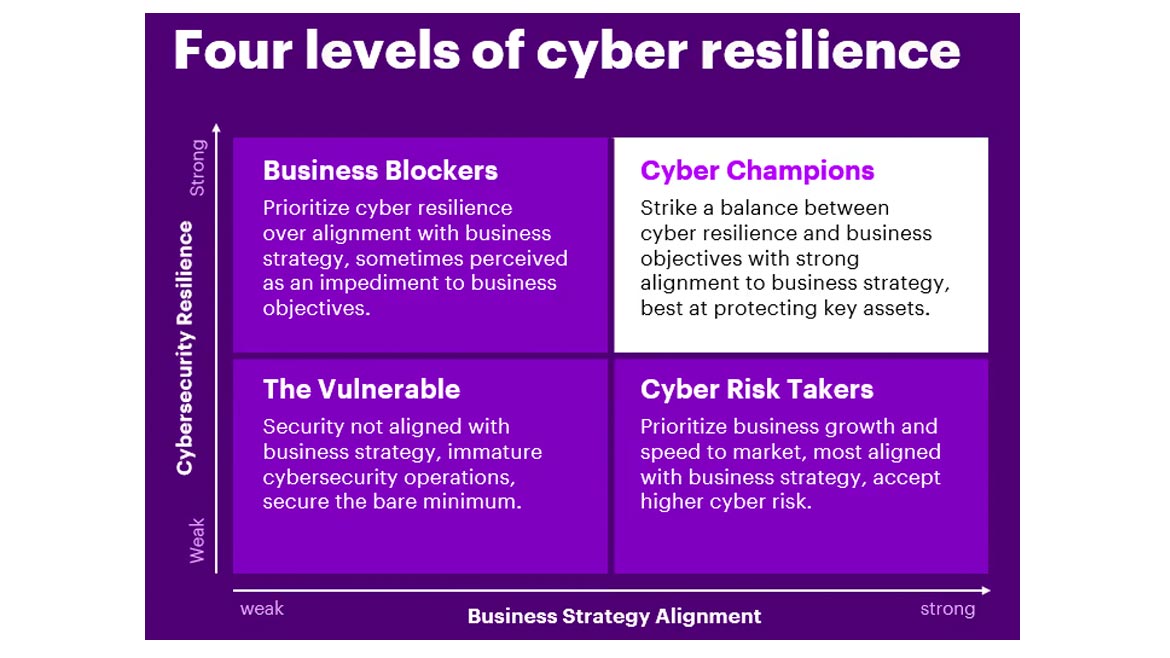
Image courtesy of Accenture
Cyber Risk Takers
Cyber Risk Takers lead in cost reduction, business growth, faster time to market, gaining market share, developing new products/services, entering markets, improved customer satisfaction and frictionless user experiences.
Despite being focused on business objectives, Cyber Risk Takers’ performance is among the poorest when it comes to the average share of successful breaches (53%) and the average share of attacks that result in significant damage (23%), according to the research.
According to the survey, Cyber Risk Takers lack visibility and have unclear metrics which delay investment decisions, and they demonstrate a poor allocation of funds.
Cyber Risk Takers could reduce costs by 65% per successful attack if they increased their performance to Cyber Champion levels, with savings of about $226,000 per attack.
While focusing on alignment alone may enable potential for meaningful business benefits, without a foundation for cyber resilience, companies will be at greater risk and have higher cybersecurity costs.
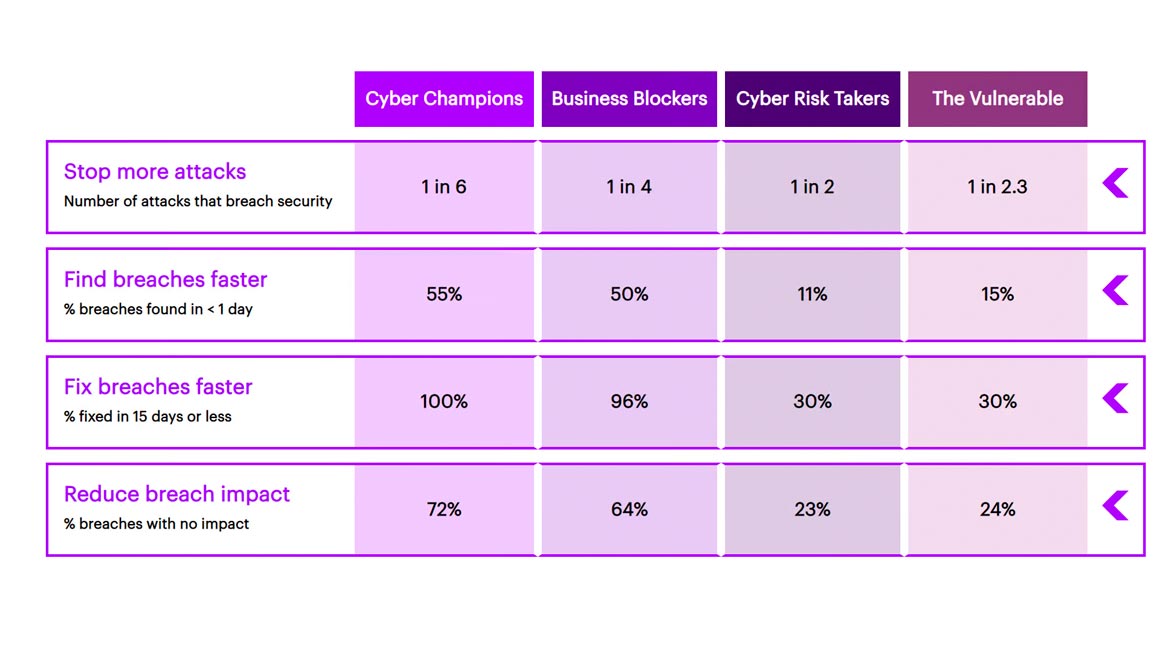
Image courtesy of Accenture
Cyber Champions
Cyber Champions are the cream of the crop. Like Business Blockers, Cyber Champions are among the top 30% in at least three of the four cyber resilience criteria. What sets them apart is their close alignment to the business strategy.
The number of successful breaches experienced by Cyber Champions is 8% lower than Business Blockers and 36% lower than Cyber Risk Takers. They also experience the fewest significant attacks, according to Accenture.
Cyber Champions have a speedier response to detection and remediation — an extra day of being fully operational can make all the difference to the bottom line. Cyber Champions are better able to protect themselves from loss of data — about 4% of Cyber Champions lose more than 500,000 records — almost seven times less than Cyber Risk Takers (27%).
Compared with other organizations, Cyber Champions are far more likely to:
- strike a balance between cybersecurity and business objectives;
- report to the CEO and board of directors and demonstrate a far closer relationship with the business and CFO;
- consult often with CEOs and CFOs when developing their organization’s cybersecurity strategy;
- protect their organization from loss of data;
- embed security into their cloud initiatives; and
- measure the maturity of their cybersecurity program at least annually.
Cyber Champions are able to strike a balance, excelling at cyber resilience and aligning with the business strategy to achieve better business outcomes. They are successful in at least three of four cyber resilience performance criteria — better at stopping attacks, finding and fixing breaches faster, and reducing their impact.
“Spending more on cybersecurity without being closely aligned to the business doesn’t make your organization safer,” said Jacky Fox, Group Technology Officer at Accenture Security. “When it comes to managing cyber risks, organizations can’t afford to lean one way or the other.”
To achieve sustained and measurable cyber resilience, CISOs need to move away from security-focused silos so they can collaborate with the right executives in their organization to gain a 360-degree view of the business risks and priorities.
To learn more about the research, download the State of Cybersecurity Resilience 2021 report here.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!




.webp?height=200&t=1717794274&width=200)



