Cloud vs. edge processing… and fake cloud too

As surveillance moves to the cloud, the terms “cloud” and “edge processing” are being bandied about by dozens of security vendors. As the terms aren’t in Webster’s, there are a significant number of misrepresentations on the market.
What’s Past is Prologue
What’s old is new. When I was a kid growing up in the 1970s and 1980s, my dad worked for Boeing Computer Services. They used to rent out time on their large computers. Boeing paid the CapEx for the computer, installed the OS, managed the applications, and essentially everything, so the end user didn’t have to do anything other than run their job. This was, by almost any definition, cloud computing nearly a half-century ago.
Then the PC (Personal Computer) came out. Anyone could buy a home computer, and suddenly all computing went on-premises. With the PC, the end-user paid the CapEx for the computer, installed the OS (or at least managed updates), installed and managed the applications, and was responsible for backups and not losing data.
Somewhere around the Dot Com boom, the ASP “Application Service Provider” got renamed SaaS “Software as a Service,” and things moved off-premises again, usually to a website ending in .com. Shortly after that, you could, for example, store your files with Box, DropBox, Google Drive, etc., where the provider paid the CapEx on the computers, installed the OS and managed the application. Around this time, people started calling this the “cloud,” and what they meant was:
1) The cloud provider supplies the computers.
2) The cloud provider manages and runs those computers from the OS through the application layer.
3) The cloud provider provides data integrity, business continuity, and uptime, which means the data must be offsite.
This brings us to the hot term in smart surveillance: “edge processing.” Vendors are touting this term in their cloud-based surveillance options, and one might logically assume that edge processing is done in a similar fashion. Let’s take a look.
Edge Processing vs. Cloud Computing
Say you wanted some of your AI security computation done on-premises. This could be for various reasons, but the most compelling might be latency: you might want a door to open when an employee walks up to it via facial recognition. If you have to push the video to the cloud, process it there, return a result, reach back out to the door controller and open the door, there might be a few seconds of delay — during which your busy employee might smash their nose into the door.
How to fix this? Well, you could process the video onsite. Run the video through a computer onsite, frame by frame, and when the AI identifies the employee, send a command to the door controller. This could save a few seconds of upload/processing/download time. Welcome to edge processing.
We are assuming that the solution provider is providing this local computer: they manage this computer remotely, and they are still responsible for making sure everything works. It sounds like the cloud, except the processing is performed at the customer’s site — at the edge. It’s cloud-based on our definition above, except something is running on-premises. This edge processing is still legitimately part of a cloud-based offering because your provider handles all the hardware and support.
All that Glitters is not Cloud
Now let’s turn our attention to the term “Fake Cloud.” Fake cloud is when a surveillance security provider slaps a DNS/DDNS entry on a computer that your company owns and operates in order to achieve the same goal. You might be logging into something like:
- www.legacyprovider.com/yourcompany
- www.yourcompany.com/legacyprovider
- https://yourcompany.legacyprovider.com
But you might still be logging into a computer at your offices. So what just happened? Suddenly your company owns that computer and is responsible for its care and feeding, and it’s your problem if the data is lost, patches aren’t done, or the computer is hacked.
Let’s review:
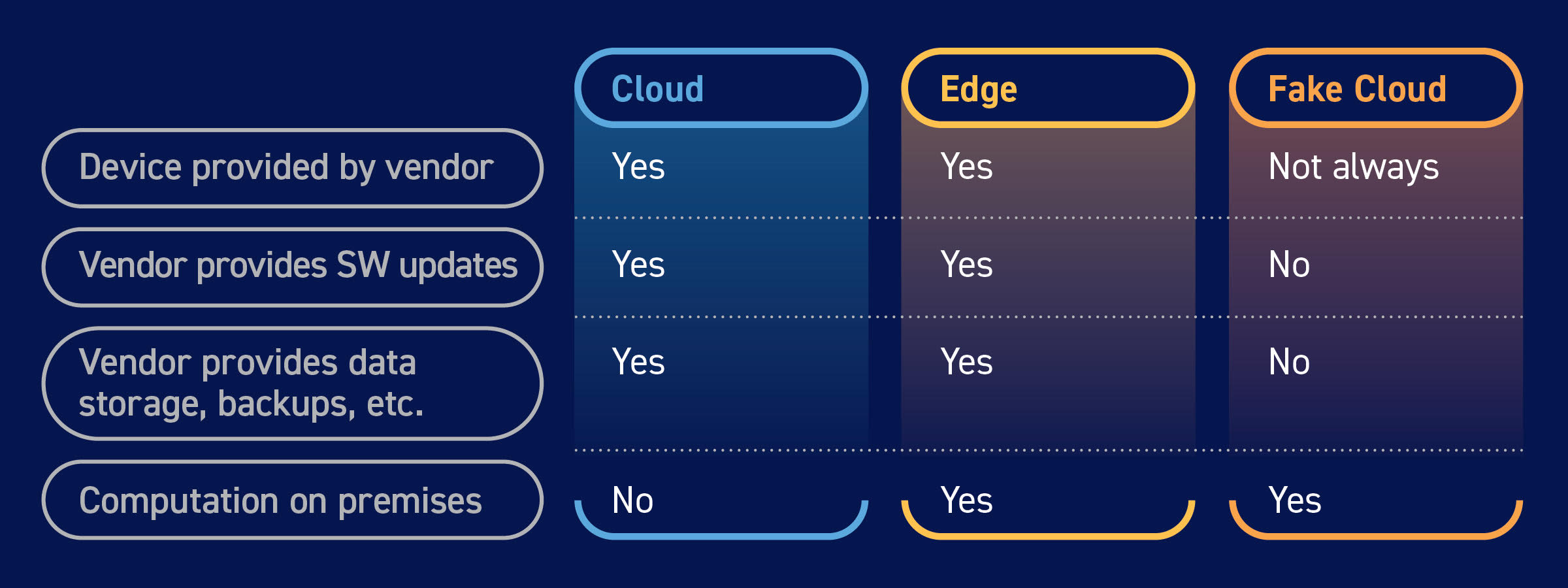
Image courtesy of Cloudastructure
Essentially, now you’re in the cloud business, but as a provider, not a customer. You’re providing the hardware and IT support. Even worse, you likely need a fixed IP address on the LAN, port forwarding in your router, a hole in your firewall, a fixed IP address on your WAN and/or DDNS, and/or a VPN… all of which jeopardize security.
If you have purchased a cloud solution for your video surveillance or are in the market to do so, ask detailed questions about where all the vendor’s software will live. Who is in charge of updates? Who is in charge of data integrity/backups/etc.? Cloud and edge processing are catchy terms, but they are malleable in the hands of a marketing team, and you may not end up with what you thought you paid for.
This article originally ran in Security, a twice-monthly security-focused eNewsletter for security end users, brought to you by Security Magazine. Subscribe here.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!







