Inside Conti ransomware group’s leaked chat logs

In February, more than 60,000 messages were leaked from the backend of a Jabber server that the Conti ransomware group used for internal communications, dating back to January 2021. Digital Shadows has examined the leak and brought it into context with its own research, providing a rare look into the cybercriminal group’s inner workings.
The Conti ransomware group is one of the most prolific ransomware groups currently operating. The group claims to have compromised 50+ new victims, such as Oiltanking Deutschland GmbH and Mabanaft Deutschland GmbH.
In March, the Ukrainian cybersecurity researcher who leaked the chats also released a password-protected archive, which contained an older version of the Conti ransomware source code, as well as the source code for version three of the ransomware to VirusTotal, a website created by the Spanish security company Hispasec Sistemas.
“It’s rare to obtain reliable primary source intelligence about threat actors’ tactics, techniques, and procedures (TTPs), structures and hierarchies, working patterns, undisclosed victims, private infrastructure, and cryptocurrency usage,” Digital Shadows says. “And then the sheer size of the data set is both a blessing and a curse — while it’s a huge treasure trove of information, making your way through every single message would take years.”
Here are some four insights that the Digital Shadows Photon Research Team learned from examining the logs:
1. Conti doesn’t work during the weekend: Conti’s operations resemble those of a real-world professional establishment. The Photon Research Team looked at the time and date stamps of messages contained within the logs and noticed a significant drop-off in the number of messages the group members sent on Saturdays and Sundays (see graph below).
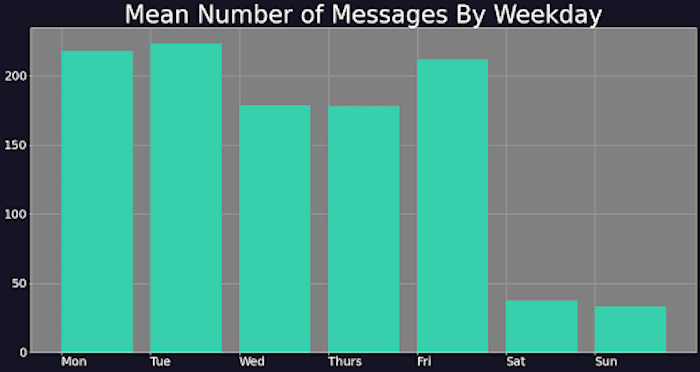
Graph showing the average number of messages sent per day throughout the data set. Image courtesy of Digital Shadows
2. Workload corresponds with chat activity: Data analyzed by the research team reveals a correction between successful ransomware attacks and message activity. The peak in attacks and increased number of victim tippers in November 2021 coincided with a peak in messaging activity before decreasing, which shows that the more victims Conti successfully attacks, the more work must go on behind the scenes to discuss tactics and illicit payments from victims.
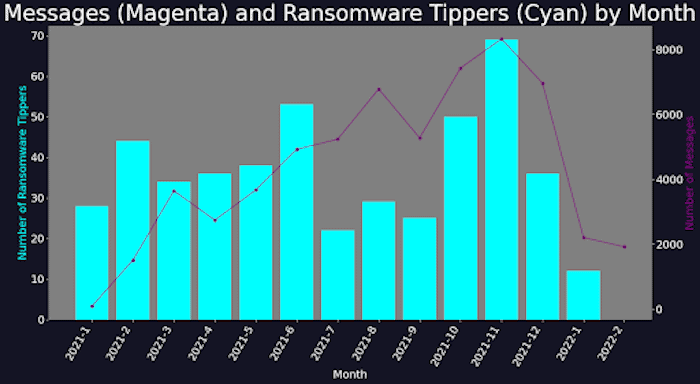
Graph showing the number of Digital Shadows’ portal tippers for new Conti victims mapped against the number of messages sent per month in the Conti logs data set. Image courtesy of Digital Shadows
3. Activity varies per month: The number of messages sent per month varied wildly, from a high of over 8,000 in November 2021 to less than 2,000 in February that same year.
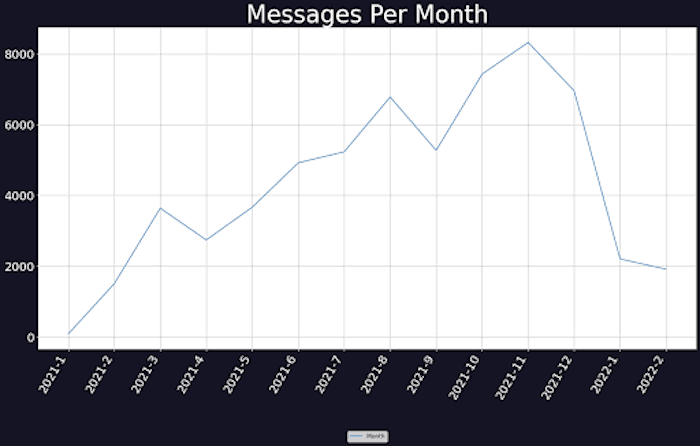
Graph showing the number of messages sent per month in the Conti logs data set. Image courtesy of Digital Shadows
4. Leadership: When looking at the distribution of messages among all different users named in the chat logs, the cybersecurity research team observed that the top 10% of users accounted for 80% of the messages sent. This indicates that a handful of users play a major role in running operations, suggesting that important decisions and strategizing are concentrated in a small group. In particular, one user stood out with more than 80,000 messages. Users repeatedly referred to this user as “boss” or “chef,” indicating that they have a leading role within the organization.
5. Working hours: After looking at activity distributed over the working day, Digital Shadows found that several Conti affiliates focus their efforts on a limited number of hours per day, with activity increasingly slowly between 0500 and 1200, peaking between 1200 and 1800. Conti affiliates are likely located over a wide geographic area, which indicates the peak activity is a crossover time in which operators all over the globe are all online at the same time.
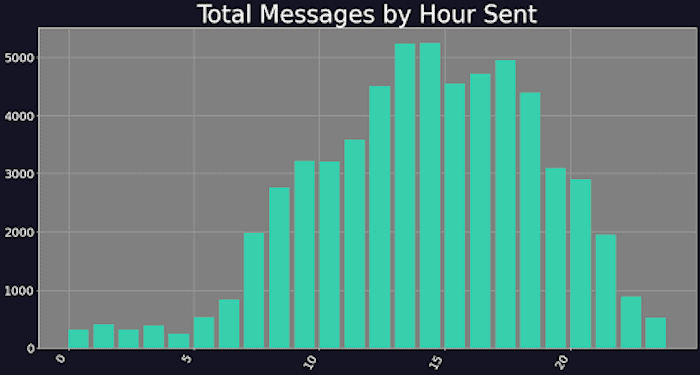
Graph showing messages sent by hour (time zone unknown). Image courtesy of Digital Shadows
For the full analysis, please visit https://www.digitalshadows.com/blog-and-research/five-things-we-learned-from-the-conti-chat-logs/.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






