Product Spotlight
Product spotlight on pandemic management and contact tracing solutions
Security magazine spotlights solutions that aid enterprises in their efforts to mitigate COVID-19 risk, including disinfecting robots, employee wellness checks and more.

 Controls Access at COVID-19 Checkpoints
Controls Access at COVID-19 Checkpoints
Battery Operated Barrier’s Heavy Utility Gate aims to aid security leaders in setting up COVID-19 checkpoints at schools, colleges, hospitals and businesses throughout the U.S. The security gate is solar-powered and can be deployed in various locations for short- or long-term use without external power. The battery-operated gate has numerous additional options, such as radio control, ultra-high frequency readers and keypad/keycard exit wands. The heavy-duty security gates come with adjustable steel leveling pads, a reflective tower and gate arm, urethane coating, security loops and an enclosed battery box. Image courtesy of Battery Operated Barrier
Find out more at www.batteryoperatedbarrier.com
Blackline Safety
 Identifies High-Risk Exposure Areas and Monitors Contact
Identifies High-Risk Exposure Areas and Monitors Contact
Blackline Safety’s cloud-enabled G7 wearable safety devices detect gas leaks, falls and other health events in business environments. They can also be used for contact tracing purposes or to determine how often workers travel through high-risk areas. The devices operate on available cellular, with optional satellite connectivity. Workers are alerted to emergencies to facilitate streamlined evacuation and emergency response procedures, and if workers themselves are harmed or injured, their location is pinpointed for use by emergency responders. G7 wearables are backed by cloud-based software solutions to enable centralized safety monitoring from internet-connected devices. Image courtesy of Blackline Safety
Find out more at www.blacklinesafety.com
Bosch
Monitors Safe Social Distancing Capacities
Bosch’s Intelligent Insights include a software widget update that can support safe social distancing. Intelligent Insights is an Artificial Intelligence of Things video software solution that combines the connectivity of physical products with the application of artificial intelligence. The Area fill level traffic light widget offers a graphical interface that can help users comply with social distancing regulations. The widget visualizes the current and maximum number of people allowed in a particular area at a specific time, illustrating three different states — normal, serious and critical — along with corresponding information, aiming to alert security professionals when safe limits are reached. Image courtesy of Bosch
Find out more at www.boschsecurity.com
Everbridge

Manages Employee Wellness Checks
Everbridge’s COVID-19 Return to Work software solution maintains real-time risk intelligence that tracks aspects of the COVID-19 pandemic, including virus hotspots, travel restrictions, quarantines, states of emergency, production stoppages and resumptions, and civil unrest. The Return to Work solution aims to quicken contact tracing efforts by providing an automated approach to tracking an individual’s exposure to the virus at work by integrating calendaring applications, corporate travel itineraries, building access control and visitor management. The solution can create a channel for employees to complete wellness checks, which can be used to determine candidates prepared to return to work. Image courtesy of Everbridge
Find out more at www.everbridge.com
Infrared Cameras Incorporated
 Detects Body Temperature Abnormalities
Detects Body Temperature Abnormalities
The Biorisk Cloud Platform combines infrared technology and a cloud-based data management solution to aid organizations across industries report and manage biorisks such as COVID-19. The Infrared Cameras Incorporated (ICI) platform streams data from thermal cameras to ICI’s cloud platform to identify biorisk patterns and threats before they cause operational issues like facility closures or shuttering of distribution centers. The cloud platform, supported by Amazon Web Services, can be integrated into an organization’s current business intelligence and operational platforms. Image courtesy of ICI
Find out more at www.infraredcameras.com
Invixium
Reduces Contact Through Biometric Access Control
Invixium has integrated with AEOS by Nedap to deploy biometric capabilities in access control systems and reduce touchpoints at entries and exits. Access control administrators can enroll biometric data to cardholders that are continuously synchronized with AEOS. The touchless facial recognition solution aims to limit exposure to COVID-19 by reducing contact between users and operators. Image courtesy of Invixium
Find out more at www.invixium.com
OhmniLabs
 Sanitizes High-Touch Areas Without Human Contact
Sanitizes High-Touch Areas Without Human Contact
OhmniClean is an autonomous robot that disinfects utilizing the power of UV-C light. Intended for use in hospitals, schools, hotels and other environments requiring deep cleaning in high-touch, hard-to-reach places, OhmniClean aims to eliminate the risk of bacteria and viral transmission and can help disinfect a 3,000-square-foot space. The robot has motion sensors, remote switches and a safety system to help ensure teams are safe when working with UV light. Detailed cleaning reports are also available to verify and monitor the effectiveness of cleaning sessions. Image courtesy of OhmniLabs
Find out more at www.ohmnilabs.com
Truyo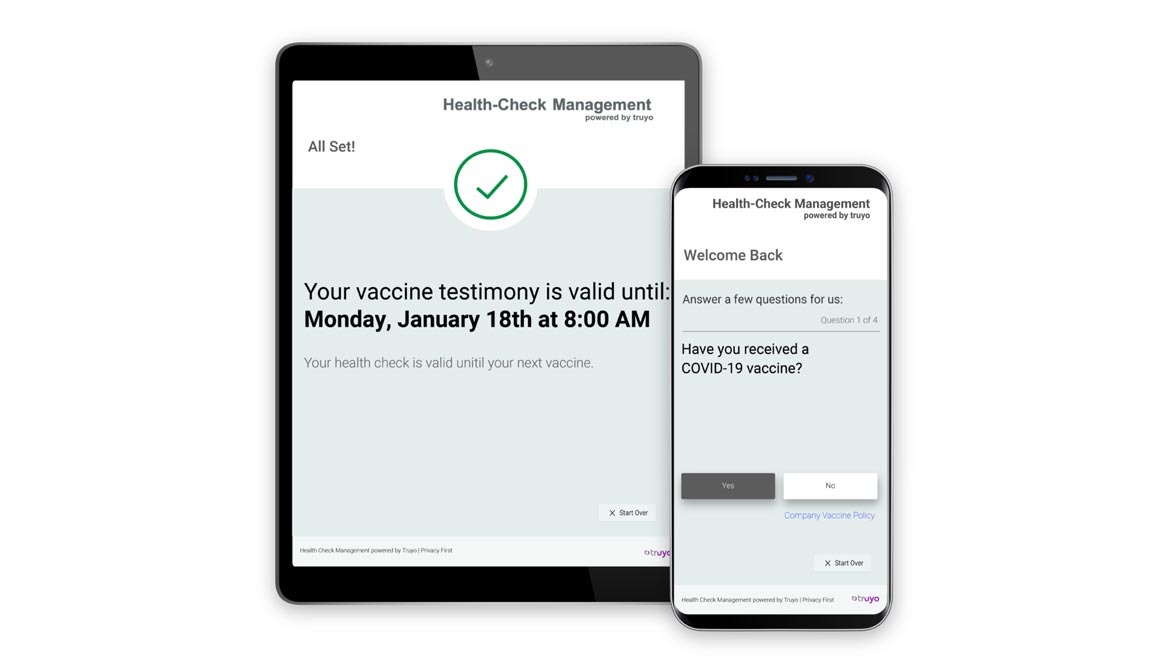
Tracks Employee Testing and Vaccination Status
Health-Check Management from Truyo and Egnyte can collect and maintain employee COVID-related information in accordance with emergency regulations. The software automates the collection of employee vaccination status and testing results and maintains personal health information in a secure environment to facilitate privacy compliance. Health-Check Management aims to set levels of access and restrict access to sensitive medical information and produce reports on the state of organizational COVID-19 testing or vaccination rates. Image courtesy of Truyo
Find out more at www.healthcheckmanagement.com
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






