How to defend against real estate wire fraud
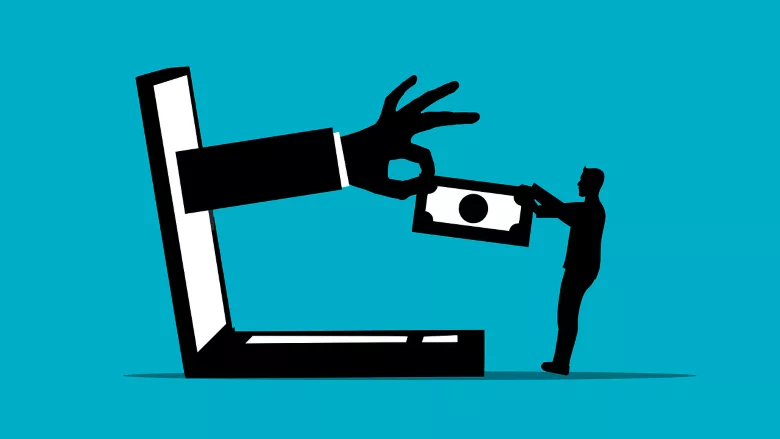
Over the past several years, real estate prices have exploded. The average home in the United States sold for $278,000 at the beginning of 2012, a number that spiked to more than $450,000 in less than a decade. While this trend has been a boon for real estate owners, it has a dark side: real estate cyber fraud has surged, and cybercriminals have developed increasingly sophisticated tactics for manipulating sensitive documents and stealing money in real estate transactions.
One of the most common cyberattacks in the real estate industry is wire fraud, which refers to cybercriminals intercepting payments from buyers to legitimate financial institutions. While cybercriminals often use business email compromise to carry out these attacks, they’re increasingly deploying malware capable of corrupting files on victims’ computers and altering documents such as wire transfer instructions. This means buyers, escrow agents, lenders and anyone else involved in real estate transactions has to be on guard against a broader range of attacks than ever before.
These are all reasons why it’s vital to verify before you trust when it comes to real estate transactions: check digital files against any hard copies available, confirm account numbers and other information with the relevant agencies and institutions, and recognize that some methods of verification (such as phone calls) can still expose participants to third-party risk, as other engaged parties could be relying upon manipulated documents.
An alarming trend in the real estate industry
Considering the amount of money involved in real estate transactions every day, it’s no surprise that cybercriminals view the industry as one big target. The FBI tracks annual losses from many different categories of cyberattacks, and the agency recently reported a dramatic increase in real estate/rental losses, from under $150 million in 2018 to more than $213 million in 2020. Real estate cyberattacks cost victims more than several other major types of criminal activity, including credit card fraud, corporate data breaches and government impersonation.
The perpetrators of wire fraud often rely on business email compromise (by far the most financially destructive type of cyberattack, costing victims more than $1.8 billion last year alone), which means they assume the identity of a real estate agent or closing attorney to trick buyers or their representatives into sharing sensitive information or transferring funds. However, cybercriminals are also infecting victims’ devices with malware that can scan their files for keywords like “wire instructions” and alter documents. For example, account and routing numbers can be changed to direct transfers of funds into fraudulent accounts.
As the number of attack vectors continues to rise, real estate buyers and professionals will need to apply the verify before you trust principle to a wider range of activities — from sending emails to reviewing documents.
How real estate wire fraud is evolving
Real estate wire fraud has become so ubiquitous that there’s a coalition of companies and industry groups dedicated to raising awareness about it. But since the Coalition to Stop Real Estate Wire Fraud was established, attacks have only increased — there were 11,300 victims in 2018, but more than 13,600 in 2020. One of the reasons wire fraud is proving to be such a stubborn problem is the fact that cybercriminals have discovered ways to bypass security measures, access sensitive information and steal ever-larger sums of money.
One of the reasons digital document manipulation is so disturbing is the fact that buyers and other real estate professionals can have safeguards in place (such as call-to-verify policies) and still end up as victims of wire fraud. For example, when home or commercial real estate buyers call loan officers to verify that they’re sending a down payment to the right account (a responsible practice that has likely prevented countless cyberattacks), this safety measure could be exploited by cybercriminals who may have altered a file on the officer’s device.
Even when banks or escrow agents have been using the same set of wire transfer instructions for years, they need to check account numbers and other information against hard copies and any other form of backup information available. Meanwhile, all other cybersecurity measures (cross-checking email addresses with legitimate entities, verifying phone numbers and login information and so on) have to be observed more faithfully than ever, as cybercriminals who carry out real estate fraud have proven adept at creating convincing spoofs and deceptions.
Putting “verify before you trust” into practice
Any time a large financial transaction takes place, especially when wire instructions are involved, both parties should adopt a verify before you trust approach: the recipient should verify details with the source and inside the document, while the sender should ask for this verification.
According to a March 2021 survey of title agents, more than three-quarters said the number of wire fraud attempts they experienced stayed the same or increased from 2019 to 2020. A staggering one-third of real estate transactions were targeted by scammers, while a full recovery of stolen funds was only secured in 29% of wire fraud cases. Still, the FBI was able to freeze $380 million of the $462 million in reported wire fraud losses in 2020 — a reminder that reporting suspected fraud as early as possible is critical to help the authorities interdict fraudulent transfers.
Everyone involved in a real estate transaction has to know exactly who they’re talking to at all times. Confirm identities by double checking contact information through official channels, refuse to click on links or attachments in unsolicited texts or emails, and verify in person whenever possible. Red flags should immediately be hoisted if a financial professional or anyone else associated with a real estate transaction is suddenly insisting that things have to be done quickly, or if there are any inconsistencies in their communications (from email addresses and contact information to the format of messages to signatures).
At a time when cybercriminals are getting better and better at circumventing these detection methods, verify before you trust has to be a core principle at all times. When everyone involved in the real estate buying process puts this principle first, the risk of wire fraud will plummet.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!








