The attack cycle, mass shootings and lone wolves: What companies should know

A mass shooting at the workplace is a nightmare for everyone involved. But for corporate security professionals, it means the injury or death of colleagues, executives or customers they are responsible for keeping safe. And the trauma of these attacks goes well beyond physical injuries.
The average gunshot victim is estimated to incur $160,000 in medical expenses, a figure that does not include the costs of rehabilitation and long-term counseling. For businesses, there are a staggering number of direct and indirect costs associated with workplace shootings — damage to brands, property, productivity, employee turnover and legal expenses.
Whether motivated by ideology, violence spilling from their personal lives, or workplace friction, mass shootings are often carried out by isolated individuals, so-called “lone wolves.”
In counterterrorism and law enforcement circles, lone wolf attacks are considered challenging to anticipate and disrupt. In contrast to coordinated attacks by groups, there are no cells to infiltrate and no communications to intercept.
But lone wolf actors leave clues about their intentions through several stages of the attack cycle. For corporate security executives, using data and protective intelligence to identify these clues is crucial for mitigation and prevention.
The concept of the attack cycle arises from counterterrorism cycles. Bad actors — terrorists — follow familiar patterns before, during, and after an attack no matter their motive. While this framework was developed for counterterrorism purposes, its concepts can be applied to crime prevention and other scenarios businesses may encounter.
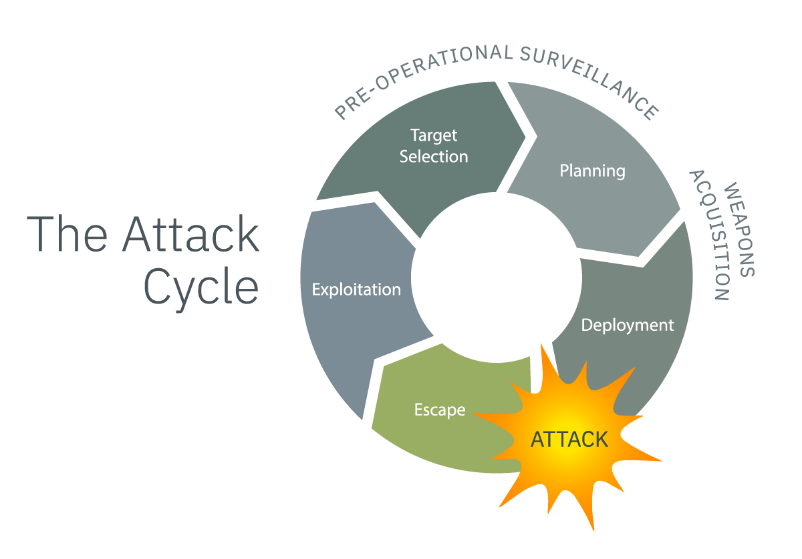
Image courtesy of Ontic
Together, target selection, planning, deployment, attack, escape and exploitation are the parts of the attack cycle. For physical security teams, the planning and target selection phases of attacks are the best opportunity to disrupt and interrupt.
We’ve recently seen this pattern play out in the arrest of an Ohio man charged with planning a mass shooting targeting women. Federal prosecutors say the man joined misogynist online communities, obtained automatic weapons, and conducted pre-operational surveillance at Ohio State University. His plot was only uncovered when police were called to his house for a disturbance. While serving time on local charges, his case was referred to federal investigators, who uncovered the scope of his planning through his computer searches.
Target Selection
During the target selection phase, threat actors look for physical sites to damage or people to hurt. That part is obvious. What isn’t obvious is how a particular target, like your company, aligns with the motives of a lone wolf actor. Security professionals need to assess whether their company is a potential target from several dimensions.
Counterterrorism researchers from Indiana State University found that 76% of lone-wolf terrorists announced their intentions before committing violence, often more than once. The researchers found that lone wolves used nearly every communications technology available: E-mails, text messages, Facebook postings and Twitter feeds, PowerPoint presentations and podcasts. Communications that cast a company in a negative light or seek to associate it with social ills should be closely monitored.
Hard and Soft
Security teams should find ways to harden their facilities as a means of discouraging or delaying attackers.
To that end, some (but not all) security measures at facilities should be clearly visible. You should also have the means to discover when people are observing your visible security measures. For example, guards and human spotters should be on the lookout for people “looking up” at cameras, and less visible cameras should be installed to cover blind spots where someone might observe security.
Some locations, however, can’t be hardened. Special events, parties and meetings are especially vulnerable. A May 2021 Department of Homeland Security bulletin warned of a perfect storm of extremist violence as pandemic restrictions ease. The report called out mass gatherings as desirable targets. Pay special attention to corporate events and social gatherings and consider whether their awareness may contribute to target selection. Rapid scans of guest lists for persons of interest can be done efficiently using software.
Disrupting Plans
Intelligence pros need years of training and tremendous amounts of discipline to learn how to conduct surveillance without showing their cards. Lone wolf actors rarely have the skill to do so. In practice, this means that there are several telltale signs that someone is conducting surveillance.
Untrained bad guys get nervous and jumpy. They act as if they’ve been burned, even when they haven’t. They often exhibit a poor demeanor — lurking in an area without a plausible reason for being there, showing a lack of “cover for status.” During my time as a special agent in the State Department, I’ve seen people duck behind parked cars or even hide behind telephone poles. If I wasn’t suspicious before, those seemingly comic moves certainly put me on alert.
Experienced countersurveillance agents rely on cover for status. Bicycle messengers make good cover because of their ability to move through traffic, as do the homeless. I had a countersurveillance colleague that could remain in a spot for days, so seemingly innocuous that other agents would drop money into his cup.
Automatic license plate readers are another vital countersurveillance tool. When linked with commercial databases, you may be able to associate a car that has passed your facility numerous times with someone who has previously come onto the radar — a technique known in the trade as the time and distance variable.
Large Companies are Wary
Lone wolf actors, motivated by socio-political beliefs and personal grievances, are the most significant domestic terror threat in the country, a joint report from the FBI and DHS has found.
A recent survey of 300 physical security and IT professionals at large companies found that, as a result of intelligence failures, 18 percent have dealt with an active shooter event at one of their sites in the first five months of 2021 alone.
While not all workplace violence is driven by extremist ideology, companies are paying attention. The same report found that since the beginning of 2021:
- 35% of executives have heard their CEO or leadership publicly express concern about physical security related to extremists.
- 42% of companies increased active monitoring of extremist views and physical threats on social media.
- 33% experienced increased physical threats and backlash tied to extremism, racial justice and political issues.
Unfortunately, it isn’t clear that the information ingested is disseminated throughout the organization. Nearly one-in-four security professionals said their organization had protective intelligence failures that resulted in missed threats or physical harm to employees.
Companies can disrupt lone wolf attackers, but it isn’t easy. They need tools and processes to integrate, analyze and disseminate information.
Social media monitoring, human resources teams, cybersecurity and physical security need to leverage the insights they have within the organization to make the whole more than the sum of its parts. Lone wolves provide clues, but they can be hard to spot and easy to miss. Sometimes, it takes many eyes and people working together from the same data intelligence to spot a single threat.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!







