Learnings from the Colonial Pipeline cyberattack: focus on the 98% of attacks, not the 2%!

For many years, the focus on securing OT environments has been on the imminent danger of a cyberattack upon critical infrastructure, in other words, SCADA/ICS attacks. Most of the concern has been on nation state actors like China, North Korean, Iran and Russia directly attacking and destroying our infrastructure.
It’s not just a Hollywood movie plot after all. It’s happened in real life. As documented in Zero Days, Stuxnet was developed by Israel and the United States to sabotage the Iranian nuclear program in 2010. Stuxnet made its way onto a private network via a pen drive, which injected malicious code onto PLCs (programmable logic controllers) used to automate the nuclear grid’s processes. Many organizations have used this Stuxnet FUD to promote the potential of SCADA/ICS attacks causing debilitating impact - disrupting our water supply, shutting down electricity or collapsing our stock market.
However, in a recent research endeavor, I examined cyber-attacks to OT over the last year (specifically to the manufacturing sector, but it applies generally) and found this - 98% of the attacks examined were everyday ransomware or other attacks typically fielded by enterprises, they were not specialized, targeted ICS/SCADA related attacks.
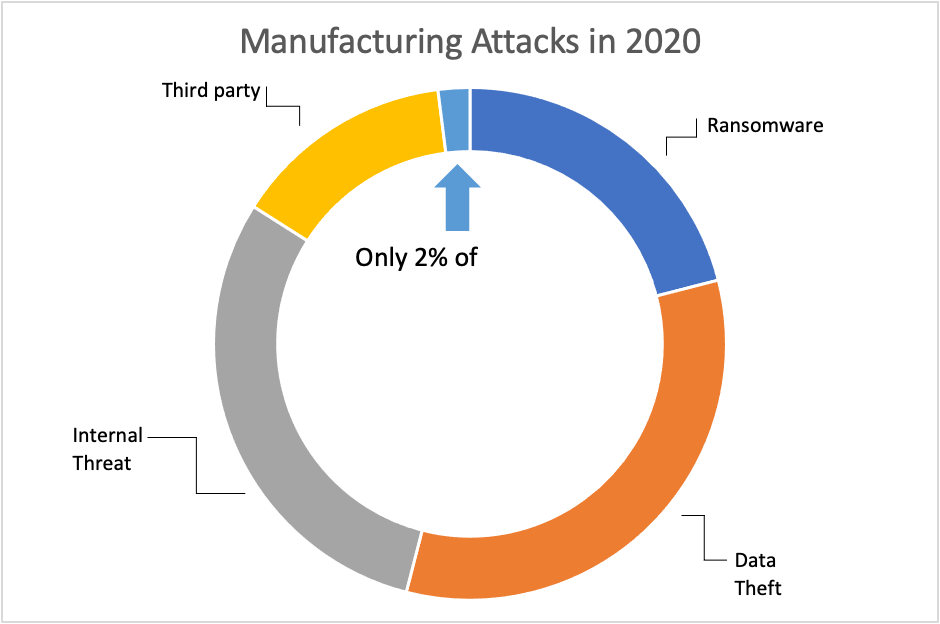
*Statistics compiled from IBM X-force 2020 Threat Intelligence Index, and Dragos Manufacturing Sector Threat perspective 2020
This does not in any way discount the danger of an attack to our critical infrastructure. What this research shows is that the main focus for securing OT environments needs to start with the IT (and IoT) environments. Most global energy companies and many other industrial enterprises are as large as many service providers. They have massive investment in IT infrastructure, backhaul bandwidth, and IT staff. Because of digital transformation, OT systems on the factory floor need to talk to IT systems (and IoT devices) in the carpeted area. That connectivity is essential to drive efficiencies, pinpoint competitive advantages, and optimize uptime. That same connectivity is what adversaries will take advantage of to compromise systems.
This was the case with Colonial Pipeline.
Energy and oil and gas companies like Colonial Pipeline typically adopt an “air gapped” security architecture with physical separation to prevent disruptions and to enable cyber resiliency. However, this is a case where a simple ransomware attack compromised the network in such a way that Colonial Pipeline found it necessary to shut down 5,550 miles of pipeline as a precautionary measure. This shows that physical separation and “air gapped” networks designed to protect the physical controls depend on IT systems that are ALSO integral to operations.
This is what I observed with other manufacturing/OT network attacks in my research. In the 98% of attacks that were non-SCADA/ICS, there were failures in risk identification (risk to operations), failures in the identification of what is a ‘mission critical system’ and failure in best practices to protect against common attacks. In many cases, the IT systems were impacted by an attack like ransomware while the OT systems were unaffected, and production could have continued. However, with IT systems down, this impacted billing, accounting, logistics, and other operational components critical to service delivery, thereby halting all production (i.e. an OT outage from IT). This means we need to change our perspective that OT is "super-critical infrastructure" while IT is more of the "nice to have back-office stuff." Both OT and IT security are equally important.
Cyber-Resiliency and the Converged IT/OT Environment
The sentiment of “Segment and Disconnect OT” just isn’t viable anymore in the age of digital transformation. CISOs and CIOS should take the Colonial Pipeline cyberattack learnings to build a business case and plan to secure their converged IT and OT environments, with the following best practices:
1. Make risk assessment a holistic exercise - Risk assessment needs to become a wholistic exercise where risk of availability should be part of the equation. The ‘what if’ question needs to be applied universally, not just to traditional operational technology but also to IT systems.
2. Identify security solutions that work across domains (IT, IoT, OT and beyond) - To build resilience across the entire organizations, the security solution to protect this converged environment needs to span the carpeted space and OT with a distinct ability to interact with traditional IT switches and firewalls. Gartner calls this “multifunction security platforms” in their recent Market Guide on OT Security.
3. You can't secure what you can't see. An effective security strategy must begin with a complete accounting of every connected device and real-time visibility into device behavior and risks. It's critical to continuously monitor device behavior and baseline their communications to identify malicious behavior and lateral movement. It is also important to be able to automate policies that limit devices to only access required for their role, i.e. Zero Trust least privilege access.
Organizations must take responsibility now for knowing what is connected to their networks, and take the steps necessary to secure every device (IT, IoT and OT) on their networks. For more best practices on ransomware, check out Ordr CISO Jeff Horne’s blog here.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






