Managing security on mobile devices through mobile certificate management
The pandemic accelerated the need for certificate management to enable authentication, encryption, and digital signature from mobile devices

Mobile devices are part and parcel of today’s increasingly distributed workforce. Laptops, smartphones, and tablets are provisioned by enterprises to increase employee productivity, while providing flexibility to work remotely. But when the pandemic struck, security teams across industries were challenged by the unprecedented speed and scale of the shift; prior to the pandemic, only 7% of U.S. workers had the option to regularly work from home, while today 42% of the U.S. labor force works from home full-time.
This disruption created great strain for IT security teams. Almost overnight, employees needed to be productive in a work-from-home reality where they were connecting to company networks, cloud applications, and email through potentially unsecured Wi-Fi networks. This challenge was compounded by the increase in employee BYOD devices, as already-overworked IT teams raced to ensure only authorized devices could connect to corporate assets. In turn, they have leaned into mobile device management (MDM), a type of security software to manage employee mobile devices. But still, gaps remain.
In today’s increasingly work-from-home paradigm, security teams need a simple way to manage certificates across multiple MDM platforms, and in some cases no MDMs, so that employees can productively access company networks, applications, and email.
Certificates secure identities across myriad devices
Public key encryption (PKI)-based certificates are the gold standard for digital signature and encryption, and serve as a strong and productive method of authentication for the array of mobile devices your workforce is using.
Digital certificates provide stronger security than passwords and are easier to use than one-time-password authentication. Passwords are easily stolen and costly to maintain; according to Gartner, between 20-50% of all help desk calls are for password resets. MFA was once heralded as a security panacea, but today the FBI warns against MFA
Conversely, digital certificates offer the strongest form of identity authentication and are an important part of Zero Trust architecture, a model of security where trust is never granted implicitly and must be continually evaluated. In fact, the U.S. Department of Commerce’s National Institute of Standards and Technology (NIST) recently named PKI a core component of Zero Trust architecture.
When the private key paired with the certificate is stored in a secure enclave, it cannot be duplicated in another device, ensuring only authorized devices can access corporate resources. With a password or OTP approach, you cannot be sure it is an authorized device. The user certificate, when paired with the device biometric or PIN, authenticates the user identity across all of the user’s devices for invisible, yet secure, access to corporate resources over EAP-TLS, Wi-Fi or TLS Web Browser sessions.
IT teams rely on traditional MDM solutions, but they remain complex and inadequate
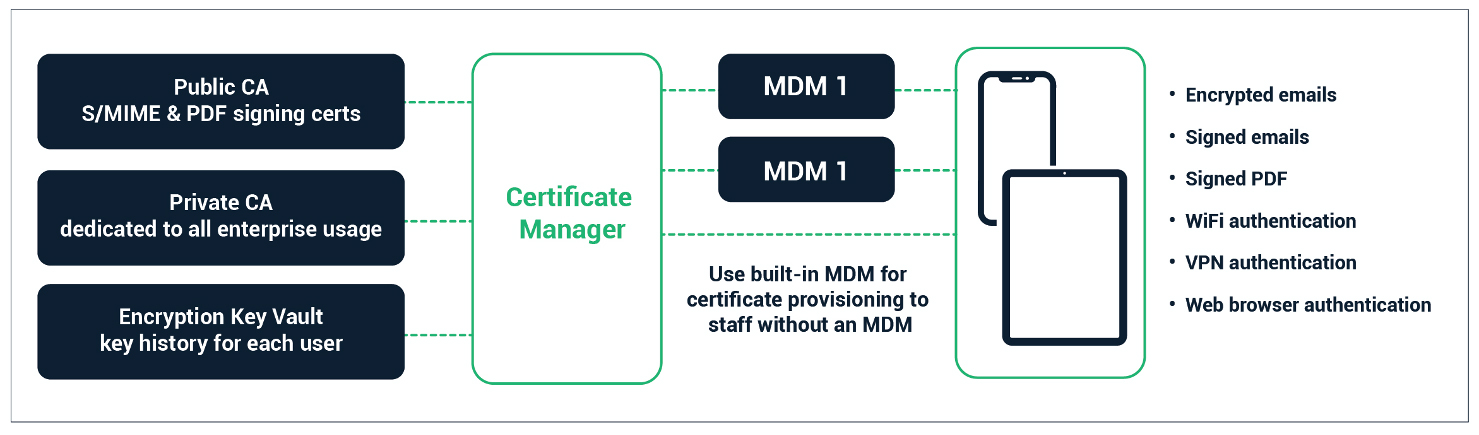
IT departments use traditional MDM software to monitor, manage, and secure employees’ many devices, from laptops to tablets to mobile phones. A large enterprise may use multiple MDM vendors. In an emergency, such as when Quantum computing compromises an RSA2048 key, they would need to run reports from all MDMs to identify and replace compromised certificates. For end-to-end email encryption, the mobile device needs the same private encryption key history on all their devices. Another scenario where traditional MDMs fall short is where enterprises have employees who are contractors from other companies and they cannot install an MDM onto their device. These same people need to access enterprise systems and therefore need digital certificates on their mobile devices.
Caption: “Mobile Certificate Management” software can be used to securely protect communications across a wide assortment of mobile devices. Photo courtesy of Sectigo.
Heterogeneous ecosystems warrant automation and single-pane-of-glass certificate lifecycle management
Relying on key management portals across multiple MDM and CA vendors is a labor-intensive process that drains already-lean IT resources. Consider the case of secure/multipurpose internet mail extension (S/MIME) certificates. These certificates require that the same keys are distributed across the multiple devices an employee may be using for email, and they require significant IT manpower to deploy, manage, and store the user keys to multiple devices.
To secure today’s expanding ecosystem of devices, IT teams need a system that provides both digital certificates and visibility into the full lifecycle of the certificates and keys in their environment. A single-pane-of-glass platform gives IT teams the power to automate certificate management — from discovery to configuration, provisioning to renewal and revocation — using standards like simple certificate enrollment protocol (SCEP) and Enrollment over Secure Transport (EST), all in a single dashboard. With the right certificate management platform, adherence to these standards is made easy in one, centralized interface.
IT teams today are working hard to keep pace with an ever-evolving enterprise ecosystem and threat landscape. At the same time, they must ensure uninterrupted and trusted access from a host of devices to the applications and services that employees require to do their jobs. The diversity of connected devices requires a simplified, automated approach to overseeing digital certificates to prevent gaps in service delivery. With centralized certificate management platforms, administrators can eliminate service disruptions through a dashboard that enables visibility into certificates, their expiration dates, and cryptographic strength, with a single glance.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






