Beyond the padlock: Essential steps for protecting websites

Businesses of all sizes have a lot on their plate when they create and maintain websites. This includes making sure the site is easy to use for visitors, that content is current, that all links work, that the site is optimized for SEO, that e-commerce processes are secure, etc.
But now, on top of all those operational requirements, businesses have to take care of cybersecurity, ensuring that their sites are safe for online customers and communities, resistant to hacking and as backed up as possible, should the site go down or experience an attack. This task list is not easy amid the evolving battle between those who want to secure websites and the cybercriminals who are trying to break them in order to steal money or data.
As the volume of attacks continues to rise, and the web becomes an even more critical face for sales and operations. website managers are tasked with navigating the array of website security tools needed to protect and backup their sites, as well as how to effectively implement them.
Five essential cybersecurity capabilities
Here are the five most essential cybersecurity capabilities required to protect and maintain a website:
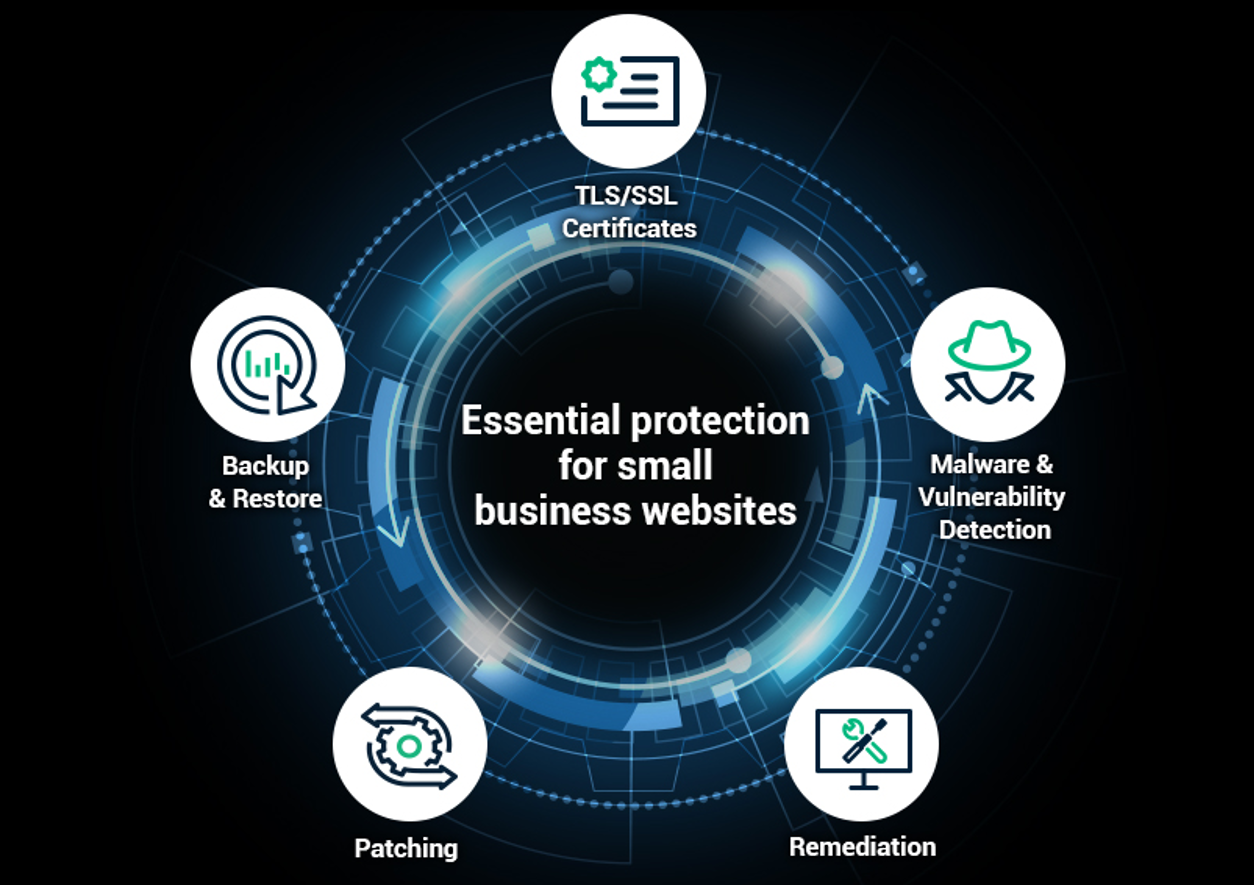
Five simple, automated cybersecurity technologies enable website managers and owners to achieve big-business web security and peace of mind, using small-business resources.
- Malware and Vulnerability Detection. “Detection” is more than just being alerted when something has already gone wrong. Website managers must be continually scanning for potential website vulnerabilities and be able to solve them BEFORE they can impact their businesses. In addition, despite your SEO efforts and web promotions, search engines will blacklist a website with known vulnerabilities, making it critical for website owners to be proactive about detecting potential issues before traffic drops. It is also critical that web teams be aware of potential vulnerabilities with the business site’s various components. For instance, a website’s content management system (CMS) or e-commerce platform may have known vulnerabilities that need to be rectified. There are numerous, easy-to-implement security products available that can help monitor websites and alert administrators to these potential issues before the site goes down.
- Patching. It is important to install and run technology that proactively patches known and new vulnerabilities before they can be exploited by cybercriminals. Having web security tools in place that can automatically scan and ensure patches are quickly installed can go a long way toward protecting your website from outside threats. For example, automated CMS patching can provide real-time threat protection that can prevent bad guys from attacking businesses running a WordPress, Drupal, Joomla, WooCommerce, PrestaShop or Magento site. Automated CMS patching can also prevent hackers from sneaking in between updates and stop zero-day attacks in their tracks.
-
Remediation. Once a threat has been detected, the next step is remediation—removing the threat. When exploring website security technology, identifying a product with the right remediation capabilities for business site is important. Website administrators need to use a tool capable of removing active infections from the website files, MySQL database, and other core components of the website.
It is also important that remediation is completed without disrupting functionality. You don’t want your website being taken down for maintenance every time a potential threat is detected. Fortunately, today’s remediation products are generally mindful of this essential continuity.
-
Backup and Restore. Insurance is key. Peace of mind comes from assurance that even if a threat slips through the cracks and damages a website, that the site can be easily restored. Version control software that enables businesses to back up and restore their website with just the click of a button is now widely available to those who recognize the importance of this technology. Many tools will even automatically create backups at certain intervals, making life as simple as possible for business owners.
Effective backup and restore tools are critical to any connected business, no matter how small. Even in a worst-case scenario where an attack cripples the entire website, the business remains just one click away from restoring what was lost. That peace of mind enables business owners to focus on the hundreds of other things they need to worry about and feel secure in the knowledge that their website is in good hands.
-
TLS/SSL Certificates. “Identity” is a critically important concept, especially online. Customers arriving at a business website need to have confidence that they are in the right place. Digital certificates (visible as a padlock in many browsers) indicate to customers that the site they are visiting is secure and that the information they enter—personal, financial, or otherwise—is being shared with an authentic/verified business, rather than a fraudulent site.
The rise of security automation has made it considerably easier to issue, renew, and maintain TLS/SSL certificates, meaning that small businesses can enjoy the benefits of identity security with minimal management. Multiple levels of SSL certificates are available through hosting providers or Certificate Authorities themselves. All products will alert website owners about the need to renew the certificate, and some even enable SSL “subscriptions” that ease the process. For web pages that collect sensitive personal data or financial information, it’s wise to upgrade from a Domain Validated (DV) to an Extended Validation (EV) certificate, which provides the highest level of authentication available.
Strong website protections help small businesses and their customers
As the stakes for cyberattacks grow, small- and medium-sized businesses must avoid putting themselves in a vulnerable position. Fortunately, as the threat landscape evolves, cybersecurity solutions, TLS/SSL products and hosting providers are evolving as well. The latest security protocols and technologies make it easier than ever to protect online assets from malware and data breaches with new suites of integrated products capable of everything from automatic certificate renewal to patching and remediation.
As highly effective website security tools become more widely available and affordable, smaller businesses are increasingly able to enjoy a level of protection on par with much larger companies. In addition, the rise of automation has put powerful detection, protection and recovery tools in the hands of even the most resource-constrained and vulnerable organizations. And while no single tool can protect against every possible threat, SMBs with effective threat detection, TLS/SSL certificates, remediation, patching and backup and restore capabilities will find themselves better positioned to successfully defeat whatever cyber threats the future may hold.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!








