How to Balance Supply and Demand within Corporate Intelligence Programs

A cursory review of the latest writing on public sector intelligence analysis reveals a great deal of soul-searching about emerging threats to the profession. One area of concern is a growing imbalance between intelligence supply and demand. The supply of intelligence is increasing while the demand is shrinking. Policymakers are more interested in making decisions based on information they read or see on the internet, it seems, skipping the intelligence middleman. Private sector intelligence programs also suffer from supply and demand imbalances that can prevent them from creating value for their companies or cause them to stagnate. The origins and symptoms of the imbalances for corporate programs, though, can be tricky to recognize. Are analysts producing too much or too little intelligence? Are security leaders demanding too much or too little? How do we even tell that there is a mismatch in the first place? A simple, four-quadrant framework can help identify imbalances and set programs back on track.
A Diagnostic Framework for Assessing Intelligence Supply and Demand
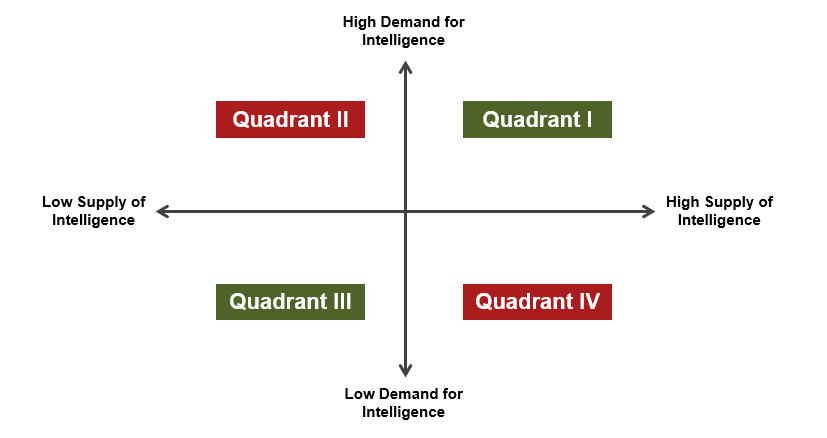
The diagram below can be used as a rough diagnostic tool to identify where current levels of supply and demand are, and later, where they should be. Imagine intelligence supply (products delivered by analysts) on the X-axis and intelligence demand (interest in intelligence by security leadership) on the Y-axis. Quadrant I and Quadrant III represent programs where supply and demand—whether low or high—are balanced. In such programs, security leaders get enough intelligence to answer their questions and not too much to overwhelm them. Intelligence analysts, meanwhile, can rest easy knowing that what they produce is meeting present needs and is being adequately absorbed by their organization. These quadrants are ideal because, all else being equal, the creators and the recipients of intelligence are satisfied. This satisfaction, in turn, leads to higher motivation among analysts, greater predictability of workflow, and directors who are willing to “go to bat” for their teams.
Source: Daniil Davydoff
In the other two quadrants, imbalances will create problems. In Quadrant II, for instance, leaders who have a high appetite for intelligence are not being given enough analysis. Consequently, they may think that the analyst team is not skilled or large enough for the task at hand. In Quadrant IV, analysts that are producing a large volume of content may become frustrated about their work going into a proverbial black hole and not being read. They may also worry about their inability to make an impact on security decision-makers.
In the long run, both the “shortage” and “glut” scenarios will prevent programs from reaching their potential. An intelligence team’s value will come into question and retention issues will arise. Worse, recession or changes in company directions may doom a program entirely. Bringing intelligence supply and demand back to balance is therefore important, but should the balance be in Quadrant I or Quadrant III, and how to move a program in either direction?
Addressing Intelligence Supply and Demand Imbalances
To solve identified imbalances, the first step is to establish whether the current levels of supply and demand came about purposefully or unintentionally. In Quadrant II, the low supply of intelligence may have been a deliberate choice of analysts who sought to be strategic about their deliverables. Alternatively, it could be due to under-confident analysts struggling to adapt to corporate needs or just a shortage of personnel or technology. In the same way, high intelligence demand may be driven by leaders who have come from intelligence backgrounds and seek to recreate the value of their old teams. Or it may be a poorly thought-through desire to keep up with the Joneses through production of “dailies” or “weeklies.”
The Quadrant IV scenario can be looked at in the same way. A high supply of intelligence may mean that analysts are efficient at delivering vast quantities of useful products, or that intelligence production has simply run amok. At the same time, low demand from security leaders may reflect a need for highly targeted assessments only, or it could mean an “old school” bias against what has been seen in the past as work that is too intangible.
The distinction between purposeful and unintentional is an important one because it points directly to the kind of solution needed to address the imbalance. In general, if the levels of both supply and demand were chosen purposefully, the answer is greater communication between the security leadership and analyst teams. The two sides need to arrive at an understanding of what the program’s purpose is and what the optimal level of intelligence production should be.
If the level of supply or demand is unintentional, however, other remedies are required. An under-producing intelligence team may need greater training or else staffing changes, supervisory hires, or external consultants may be necessary. Overproducing analysts, on the other hand, may benefit from guidance on strategic prioritization. Lest one think that analysts are always the problem, security leadership may sometimes need a bit of handholding too. Analysts can educate security directors on the downsides of the “kitchen sink” approach to alerts and analysis. Likewise, under-interested security leaders can be shown examples of work that will directly impact physical security or operations.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!









