2018 Security 500 Report: Metrics, Budgets & Accomplishments

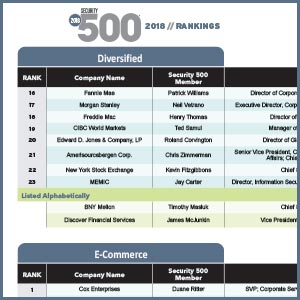
Welcome to the 2018 Security 500 report, which includes the 2018 Security 500 rankings and sector reports. Our annual Top 10 Trends will be officially unveiled in a webinar later this month.
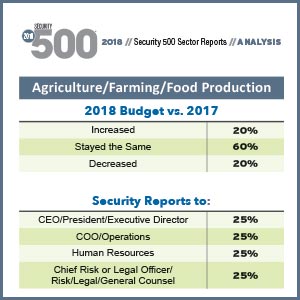
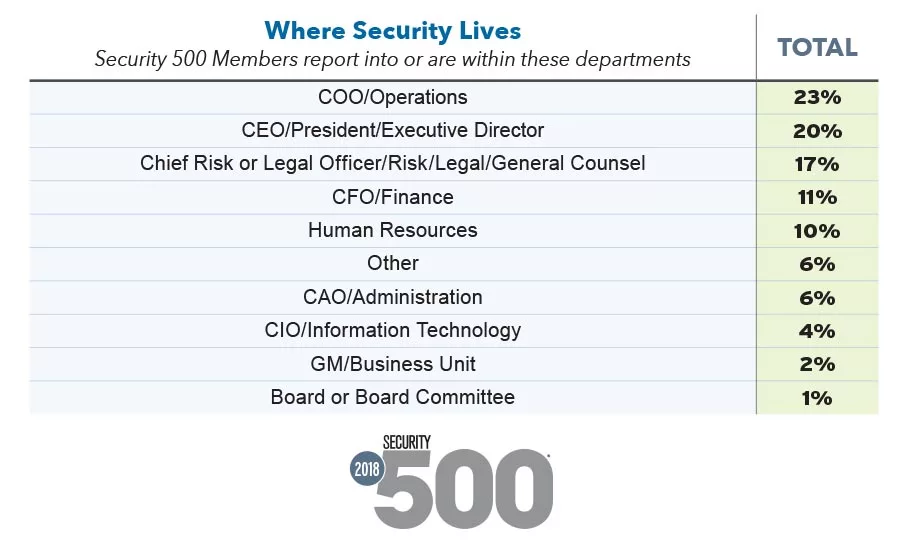
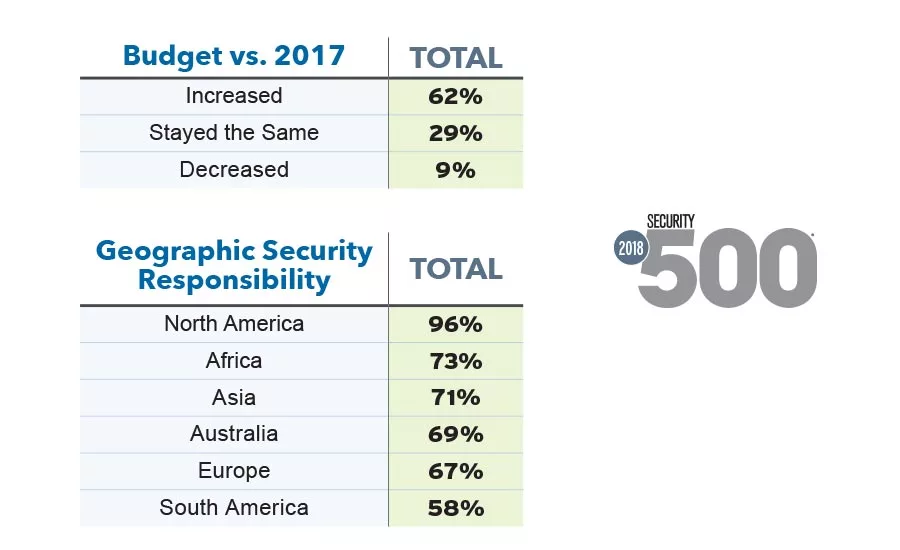
We’re excited to provide data on security budgets – 62% of Security 500 respondents reported budget increases from 2017 – in addition to data on where Security 500 Members report into within their enterprises, and a question about the use of a security metrics program that defines productivity, value creation and cost avoidance.
This year's Security 500 survey included questions about some of the successes that enterprise security achieved in 2017. The answers were impressive, and included:
- “Maintaining best in class standards and practices despite rapid growth in new lower cost locations while meeting new and existing regulatory expectations.”
- “Mandatory Workplace Violence (WPV) and active shooter response (Run, Hide, Fight) training for all employees.”
- “We were not victims of terrorist activity and we kept our employees safe while traveling.”
- “Reduction of loss through solid prevention program that resulted in $6.2 million in loss prevention.”
We also asked questions about the types of security technology that Security 500 Members will employ in their enterprises in the future. Some of those responses:
- A drone detection system.
- An Incident Response Program.
- An enhanced vendor and third-party risk management program.
A comprehensive list of successes, technology, and strategies/philosophy changes that enterprise security executives expect to implement in the coming year will be also be discussed in the Security 500 webinar on November 20, 2018. The webinar will be available on-demand until November 2019.
What security technology/technologies do you expect to implement in the coming year?
- Piloting several technologies to determine their capabilities and fit-for-use within our environment, to include wireless hand-held credential screeners, drone fleets, robots, credential kiosk in lobbies and other perimeter entry areas and smart camera software.
- Thermal cameras, turnstiles, man traps, virtual fencing with cross line detection and license plate recognition.
- Two-factor access control, expanded video storage and improved security at the perimeter.
- Stop the Bleed training for officers.
- A drone detection system.
- Addition of video analytics to our video management system.
- Increase our focus on students in our cybersecurity program, including hiring several student workers to be a part of our security team for the first time to help supplement our security operations center initiatives.
- Exploring access control components such as optical turnstiles in our public lobbies and metal detectors in our Emergency Department.
- Active monitoring of employee and non-employee populations.
- More social media monitoring technologies.
- Encrypted solutions on every security device or technology.
What strategy/philosophy changes do you expect to implement in the coming year?
- Implementation of an electronic visitor management system and requiring sex offender registry check and photo identification for all visitors, to include parent, vendors, contractors and others.
- Exercising Enterprise Security Risk Management (ESRM) in all security decisions.
- An increased effort to obtain external partnerships to allow us to further mitigate risk.
- An examination of how we respond to non-criminal matters, such as those when an individual is in crisis.
- Expansion of our Security Liaison program where we partner with a clinical team to support them in caring for our patients.
- Expanded active shooter awareness to include framework for implementing strategies such as ALICE training for employees.
- Education and deployment of an enterprise-wide security plan.
- Be more proactive – hunt for threats rather than responding to them after the fact.
- Continuing to add Intruder Deterrent Locks to all of our classroom spaces.
- Present a business case to expand the security/safety strategy to other business components of the enterprise.
- Improvement in guard skills and performance through greater compliance and salaries. The greater the core competencies, the greater the salary required, the greater the performance.
- Continued focus on process excellence, particularly around regulatory topics (privacy, DHS anti-terrorism standard), crisis management, including more robust plan testing.
- Transform some of the security services provided in the field to more strategic and less tactical everyday resolution of issues.
- Greater focus on training for international travel.
- Increased security and data protection measures to understand where the data is, how it is used, and how to best categorize it.
- Introducing a mass communication system to assist us in warning people of significant events occurring on campus in close to real time.
What was your security organization’s greatest achievement in 2017?
- The acceptance of the Global Security Operations Center as being a central point/clearing house of information for various business entities within the enterprise.
- 100% of all Security Officer staff received credentialing with the International Association for Healthcare Security and Safety.
- Contracted with local sheriff's department to provide armed security in the Emergency Department.
- Significant expansion of community policing to increase community involvement in overall community safety and awareness.
- Weathering Hurricane Harvey, and Winter Ice Storm Inga that arrived a few months after Harvey, including transporting nearly 70 physicians, nurses and medical technologies into the medical center, rescuing medical professionals from rising waters, distributing relief supplies to our own employees in need, responding to medical emergencies and crimes, and deployed extra officers to ensure the safety of our buildings.
- Rolled out an asset protection program in the SE Asia Region.
- Creation of a program to offer support to staff in caring for victims of violence.
- More than 2 million people safely attended events at our stadium in 2017.
- Movement to the cloud for physical access control and visitor management.
- Completion of a unified security system installation.
- Development and implementation of a firm-wide security awareness and education program that provides topical security content to support employees and customers, utilizing on-demand video.
- Developed a multi-disciplinary fraud and cyber risk mitigation.
- Significant support provided during 60 straight days of EOC activation in response to major hurricanes Harvey, Irma and Maria, a strong earthquake in Mexico and wildfires in the Western U.S.
- Protective Services secured approval and funding for access control renovation across the enterprise.
- For the first time we were able to conduct an Active Assailant exercise with classes in session.
- Creation of a Global Security Operations Center, successfully securing operations at the Korea Olympics and Russia World Cup.
- Took on five additional corporate retail locations out of state, on-boarded each location's management team, coordinating intrusion system and NVR upgrades, all while coordinating a major corporate office remodel and move concerning keys/cores and doors.
- The arming of our security officers.
- Identification and initiation of remediation efforts to reduce cyber risk to our company.
- Development of opioid addiction committee with key community members and action programs, including community outreach initiatives, which assisted in reducing drug related deaths by 30% from the January 2017 to June 2018 time period.
- In 2017 we chartered and implemented an executive level Risk Committee, charged with managing all risk associated with security of the organization. A metrics report program was created to keep the committee informed, and an enterprise integrated risk management for security program was established. The program was briefed to the membership and Board of the organization.
- Managed budget reduction while dealing with increase in total incidents.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!