From the Front Door to the Plant Floor

What makes a smart card "smart?"
For one, a typical card can hold about 72,000 bytes of data – about the equivalent of a 10-page word document. Compare that to traditional access cards, which can store only 200 bits of data. The data capacity of smart cards means they can hold multiple biometric templates, including fingerprints and iris scans. Smart cards are more convenient, more durable and, because they can’t be duplicated, more secure.
Large-scale manufacturing and processing facilities are putting smart cards to work in a number of applications:
Authentication
Stealing a photo ID badge and changing the photo is a common way for intruders to gain access to a building. When employee photos are stored on smart cards, the photo on the badge can be checked against the photo in the access card, which is secure and cannot be modified. In addition, fingerprints and iris scans can be stored on the card, providing additional confirmation.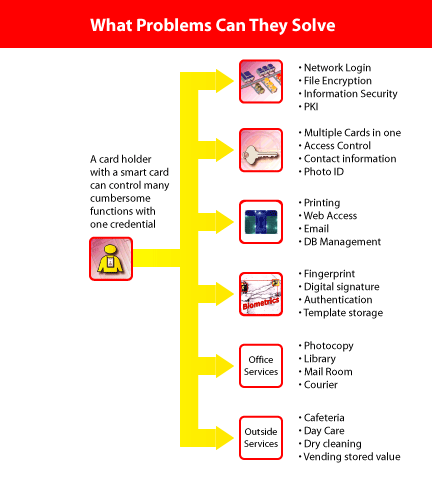
Data, system, process protection
Smart cards used for identification and access can also be used to log onto a PC or workstation to perform tasks, access data or manipulate key building systems or manufacturing processes. If a particular supervisor’s approval is required for an employee to log on or make a change, that supervisor’s fingerprints can be stored on the employee’s card. Thus, the card reader knows to expect a second card swipe validating the first – and a particular set of fingerprints – before allowing the employee to access the system.Of particular importance to homeland security is the ability to track and profile the routines of employees based on smart card use. Security system alarms can be activated if an employee’s card use becomes erratic or out-of-the-ordinary.
Smart cards are also helping facilities assure routine safety and keep employee training up-to-date. An employee who hasn’t been trained in certain processes or procedures (or whose training is out of date) can be denied access to areas that required that training – clean rooms, for example. In addition, companies can link access to the onsite presence of certain personnel.
Mustering, emergency response
Suppose a large-scale emergency did occur at a facility – how would you ensure the safety of individual employees? Some facilities are placing static or remote card readers at designated "mustering" or gathering points throughout the facility, thus providing a way to identify employees who are missing and possibly injured. Other companies have established checkpoints throughout their facilities, so the number and identity of employees in a particular area of the facility is always known. Individual health information – for example, allergies and blood type – can be placed on smart cards as well, making it readily available to emergency response personnel.In the future, as homeland security legislation continues to mandate tighter facility control, smart cards will gain wider acceptance as a tool for integrating and tightening physical and logical security.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





