Privacy Tug-o-War


The controversy swirled faster when some citizens and legislators started to object to the use of so-called red-light cameras and video surveillance in nursing homes - what some call Grannycams.
With the spread of video and biometric technologies, used in public by law enforcement but especially when the technologies combine, the cries over privacy invasions and Big Brother have grown louder.
So loud, in fact, that the Security Industry Association (SIA), at a recent press briefing with a representative from the International Association of Chiefs of Police (IACP), called for reason when it comes to life safety benefits of security technologies. The fear is not so much that the critics will halt police use of video surveillance in public but that the objections would evolve into federal, state and local regulations that could hamstring video and biometrics by business more generally. In California and elsewhere, legislation has been proposed to reign in video surveillance.
In some ways, of course, the cat is already out of the bag.
Security systems that combine video and facial biometrics are in the Trump Marina in Atlantic City and the Stratosphere casino in Las Vegas. Law enforcement agencies in Los Angeles and Santa Ana, Calif., have used the combined technologies. And the Winter Olympics in Salt Lake City and Summer Games in Athens may employ such systems.
The IACP estimates that more than 60 communities already have red-light camera systems to automatically document cars that run red lights.
And some legislators, responding to calls to make nursing homes safer, have proposed regulations requiring video surveillance in those facilities.
But back in Tampa, when the city implemented the video-biometrics combo on the streets, the drumbeat of criticism hit a new high.
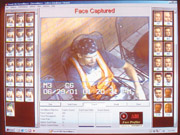
There, facial recognition firm Visionics Corp., and partner Advanced Biometric Imaging helped the Tampa, Fla., Police Department integrate FaceIt facial recognition technology into an existing video surveillance system the city had in its Ybor City entertainment district.
The FaceIt system automatically scans the faces of people passing in front of the 36 cameras and uses those facial images to instantly match against a database of photographs of criminals. The database is maintained jointly by the Hillsborough County Sheriff and the Tampa Police Department. When fully loaded, the database will contain 30,000 images.
Respecting Privacy Concerns
According to Visionics, the application follows "industry-established privacy guidelines and existing laws governing use of personal data by public agencies."For example, there is clear signage posted throughout the area indicating that "smart CCTV" is in use. The images in the database are those of known offenders. And non-matching images are discarded from the system once the comparison has been concluded.
Tampa's coupling of video surveillance and facial recognition biometrics drew the ire of the Law Enforcement Alliance of America (LEAA), suggesting that the application "represents a violation of every American's 4th Amendment right of privacy." Says LEAA Executive Director Jim Fotis, "Law enforcement officers depend on the trust and support of the community they protect. When police are perceived as being part of the big brother scheme that these cameras represent, their relationship with the law abiding citizens of the community is damaged."
Fotis also hinted that his organization, with 65,000 members and supporters and a coalition of law enforcement professionals, may help "introduce legislation at the state and Federal levels to ban the use of these systems altogether."
This summer, during the dust-up over the Tampa video-biometrics application, the SIA, an industry trade organization, held a press conference with Thomas Seamon, CPP, chairman of the Private Sector Liaison Committee of the IACP, to defend the Tampa set-up as a reasonable life safety application. At the event, the maker of the facial recognition system called for federal legislation to ensure ethical use of the technology and to assure people that their privacy is being protected. Previously, the IACP Committee had partnered with the SIA on the development of guidelines for public use of video surveillance systems more generally.
At the press briefing, Seamon, commenting on the public pilot projects using facial recognition to enhance the capabilities of CCTV systems, said, "The facial recognition technology alone is neither good nor bad. As with all technology use by the police, it is important that sound policies and procedures govern its use and that the capabilities and application of the technology are explained and discussed with the affected public."
Pointing out that the use of cameras in public areas "merely enhances the vision of the police officer on patrol," Seamon added that the "use of facial recognition technology in some way is akin to the diligent officer who familiarizes himself with the mug shots of repeat serious criminals who live on or frequent his beat."
At the same press briefing, Richard Chace, executive director of the Security Industry Association, was even more pointed. "It is time," he said, "to stop focusing solely on how this technology could be potentially abused, and start talking about how this technology can be positively used in a responsible and effective way."
Chace added, "This technology is about public safety and life safety. It is an invaluable tool for law enforcement to ensure we have safe communities in which we raise our families."
Ironically, while some are protesting the alleged invasion of privacy of video surveillance and biometrics, it is privacy that's driving growth and bringing positive attention to many security approaches.
Responding to consumer concerns, U.S. Federal agencies and state governments as well as governments worldwide have enacted or soon will enact stricter privacy legislation. Laws, such as the one the guarantees confidentiality of health insurance records, aim at making organizations accountable for the personal information they gather and retain.

Biometrics Goes Mainstream
In a report, World Biometric Technologies Markets, the consulting and research firm Frost & Sullivan is bullish on biometrics. So is research firm International Data Corp. (IDC), which predicts business and government security buyers will increase their biometrics spending from just $166 million in 1999 to $1.8 billion by 2004.At present, governments purchase a majority of biometrics-based systems. Fingerprint systems and, to a lessor degree, other biometric approaches are popular with law enforcement, corrections and high security government operations.
However, dominance by government users of biometrics should change in the near-term as more business and institutional buyers adopt the technology. Viisage is working with Graphco on a system called FaceTrac which aims at pubic transportation, corporate and home security markets. The trend is especially seen when it comes to computer, network and Internet access applications. For instance, earlier this year, Iridian Technologies, with its iris recognition technology, received certification from Computer Associates in an eTrust Single Sign-On program, which eliminates the need for workers to manage multiple passwords.
Still, some security buyers see a biometrics price hurdle. A Gartner Dataquest study, Pointing the Finger at Biometric Technology, contends that outside the U.S., there is little or no concern about price and that because of the rising security concerns worldwide, biometrics is about to go mainstream, according to Dore Perler of SENSE Holdings, a biometric provider.
Also "the emergence of new standards could demolish a long-standing obstacle to industry growth," says Prianka Chopra of Frost & Sullivan. "The biometrics industry, once plagued with interoperability issues, has combined forces and agreed on a common platform."
Recently many biometric manufacturers agreed and released what's called the Biometric API standard or BioAPI, which facilitates communication among applications.
The accuracy of various biometrics-based systems also is an issue. Past generation systems had a level of acceptance and rejection errors of concern to some security buyers. Even today, with improvements in the technology, there are people who don't "work" with certain types of biometrics. Professor James Wayman of the College of Engineering at San Jose State University, has been quoted as saying that "most biometric devices have error rates of at least 1.5 percent."
Still improvements continue to be made. Just recently, the Defense Advanced Research Projects Agency gave Visionics $2 million to improve the company's facial identification technology so it can be use by the military and intelligence agencies.
There are various partnership projects that bring together biometrics and door access controls. For example, DoorTek Corporation, the San Antonio maker of access control systems, now incorporates Identix's V20 fingerscan readers into its DoorTek access system. Using a Wiegand interface, the biometrics readers integrate with an existing proximity card system.
Also similar to the early days of access control, there are many players in the biometrics field reflecting both the variety of approaches-finger-scan, hand geometry, iris recognition, voice verification, face recognition, signature verification and retina recognition-and the ease of entry. Some vendors own patents, thus limiting the number of companies for certain approaches. "Eye" biometrics is an example. However, over the past several years, there has been entry by numerous finger-scan companies.
Still the biometrics field is now maturing.
Some approaches have made solid gains in certain applications. For example, immigration agencies tend to use hand scanners to identify and simplify entry of frequent business and government travelers at airports worldwide. Some banks now use eye scanners to identify customers at ATMs. And some financial service companies use voiceprints to identify investors when they log into their accounts by telephone.
Red-light Red Hot
While using primarily still and video photo technologies, red-light cameras are creating their own controversies. Grassroots objections and Congressional criticism, based on privacy and fairness, aim at stopping red-light cameras.The Insurance Institute for Highway Safety has spearheaded scientific research about the effects of red-light cameras, finding they not only deter red light running but also reduce intersection crashes, including collisions involving injuries.
Each year more than 800 people die and an estimated 200,000+ are injured in crashes that involve red light running. Total deaths in such crashes numbered almost 6,000 during 1992-98. More than half of these deaths were pedestrians and occupants in other vehicles who were hit by the red light runners. Another 2,779 deaths occurred in the vehicles running the red lights. During the same time period (1992-98), about 1,500,000 people were injured in such crashes.
Researchers found a 68 percent reduction in front-into-side crashes involving injuries in Oxnard, Calif., after camera enforcement began in 1997.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






.webp?height=200&t=1632081700&width=200)


