Product Spotlight
Product spotlight on mobile security solutions

With travel mostly back to pre-pandemic levels, mobile options for security are of growing importance. The protection of devices and employees is a top priority.
Security magazine highlights mobile and portable security solutions, including alarms, phishing prevention and communication devices.
Bitdefender
Protect company and BYOD devices from phishing
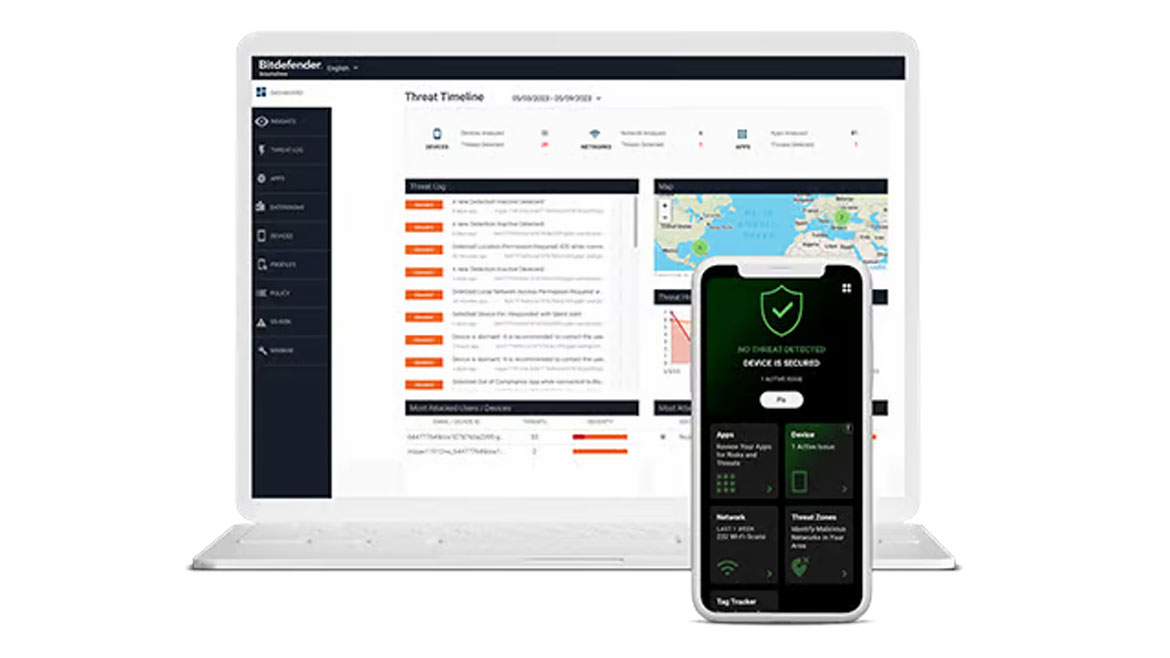
Bitdefender’s GravityZone Security for Mobile ensures safe and secure access to corporate data, safeguarding both corporate-owned and BYOD devices from modern attack vectors, including zero-day, phishing and network attacks, by detecting both known and unknown threats. The system offers on-device anti-phishing protection on all supported platforms (iOS, Android) and on-device, local VPN for real-time processing of traffic without relying on an external service, thereby effectively preventing phishing attacks. Image courtesy of Bitdefender
FIND OUT MORE AT BITDEFENDER.COM

Connecta Mobile
Integrate security into daily functions
Connecta Mobile is hardware designed to keep financial information and other sensitive data confidential with 256-bit data encryption. The device will also keep physical movements hidden and usage patterns invisible to avoid unwanted spying and profiling. All voice, text and data transmissions to and from the device are encrypted to prevent spying and eavesdropping. Image courtesy of Connecta Mobile
FIND OUT MORE AT CONNECTAMOBILE.COM

Lookout
Wirelessly contact personnel in an cmergency
The Dispatcher II from Lookout is a flexible, wireless alarm panel that is used as a wireless emergency call system. The Dispatcher II can be used with a variety of sensors such as motion detectors, door/window contacts and vibration sensors to suit user needs. Each sensor, when triggered, broadcasts a user-prerecorded message over the user’s radio system. Text messages and emails can also be sent. Any personnel (officer, deputy, administrator, principal, etc.) with a radio can hear and respond to a broadcast message immediately. Image courtesy of Lookout
FIND OUT MORE At LOOKOUTPORTABLESECURITY.COM
McAfee
Continuously detect phishing attempts
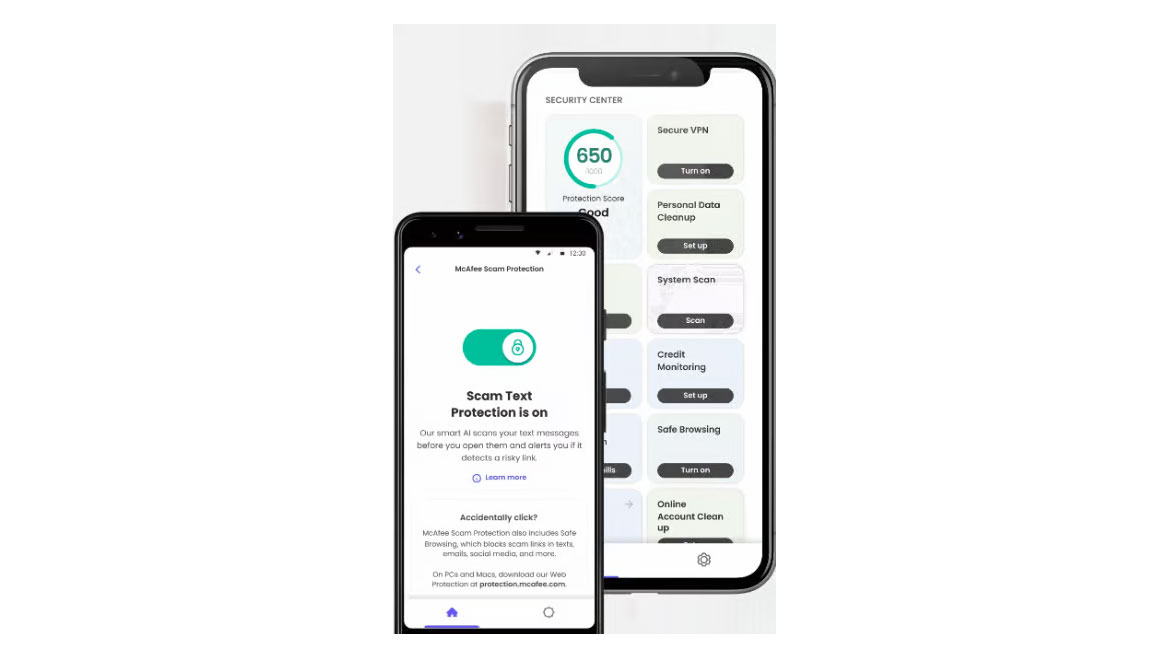
McAfee scam protection is designed to monitor personal info like email accounts, phone numbers and more. The system will scan any sent links for potential scams and alert users if one is found to prevent phishing attacks. If any breaches are found, the program will notify users and show them potential actions. The system includes anti-virus protection and a virtual private network (VPN) to help protect personal data on mobile devices. Image courtesy of McAfee
FIND OUT MORE AT MCAFEE.COM

Sentrysafe
Protect items while traveling
The Master Lock Compact Safe from SentrySafe is designed for “on the go” security. The safe is built for small spaces such as vehicles, dorms, campers and boats. It is designed to secure cell phones, wallets, keys, iPods, GPS units and other compact items that are vulnerable to theft. The safe works well for travel when traditional security measures may be unavailable. Image courtesy of SentrySafe
FIND OUT MORE AT SENTRYSAFE.COM
Symantec
Monitor and protect networks from threats
Symantec’s SEP Mobile can integrate with an organization’s mobile device management/enterprise mobility management (MDM/EMM) to add active threat identification at the device, app and network-levels. SEP Mobile offers basic MDM capabilities such as setup configurations, passcode lock, remote wipe and reporting on jailbroken/rooted devices. SEP Mobile can leverage third-party VPN integrations to disallow non-compliant devices from connecting to corporate networks while under attack or while the mobile user has entered into a high-risk zone identified by SEP Mobile. For companies without a mobile VPN solution, SEP Mobile can automatically route sensitive traffic via SEP Mobile VPN to secure communication when a device is in a high-risk zone. Image courtesy of Symantec
FIND OUT MORE AT DOCS.BROADCOM.COM

Tattletale
Wirelessly sound emergency alarm
Tattletale’s Panic Keychain Pendant provides peace of mind up to 1000 feet away from the base unit. The pendant can be used in schools, retailers, and other sectors to protect employees. The pendants are individually named, allowing police responders to know where the panic function was used and respond appropriately. Image courtesy of Tattletale
FIND OUT MORE AT TATTLETALE.COM

Transcend
Detect and alert users to threats
The Transcend portable alarm base unit and sensors are built for security under extreme conditions. Each base unit can manage up to 500 wireless sensors within a half-mile radius. That radius doubles with a signal booster. The base unit and sensors cannot be tampered with once they are activated. Even when the power goes out or unplugged, these portable alarm systems continue to function off of 20-plus hours of battery backup. The system also doesn’t have any accessible wires to cut. Image courtesy of Transcend
FIND OUT MORE AT TRANSCENDSECURITY.COM
Trend Micro
Detect malware for secure file transfer
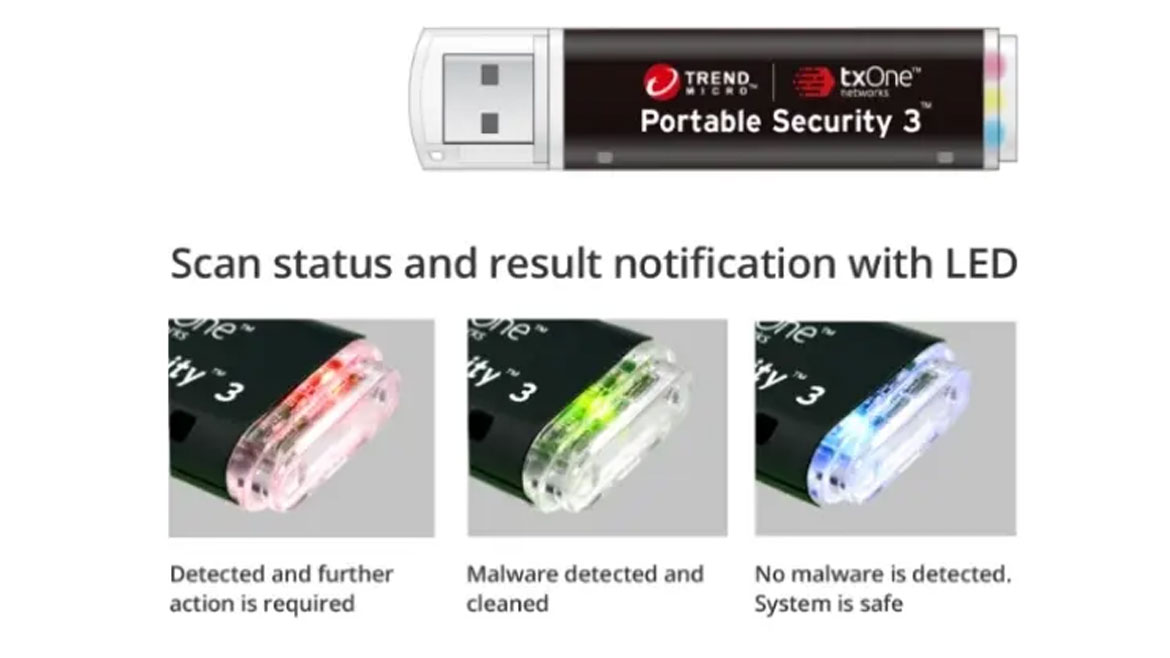
Portable Security 3 is a USB flash drive designed for antivirus scans. Use the tool at a checkpoint to prepare partners, vendors or consultants coming onsite with a pre-scan. Before guests connect their potentially infected laptops or USBs to an industrial control system (ICS) network or assets, security leaders can plug in Portable Security 3 and follow the intuitive on-screen instructions to seamlessly scan and secure devices. The built-in LED lights indicate whether malware has been detected or eliminated and if further investigation is required. The device also includes 64 GB of secure storage equipped with AES-256 hardware encryption. Image courtesy of Trend Micro
FIND OUT MORE AT TRENDMICRO.COM
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






