The year in ransomware: Key targets, extortion tactics, and what to do

While the exact number of victims is not known, it is estimated that more than 205,000 U.S. firms have been compromised by ransomware in 2019, while other research reports a 715% increase in global ransomware reports year-over-year for the first half of 2020.
Kroll’s incident response casework has also seen the number of ransomware attacks steadily rising. Nearly 14 months ago, Kroll started to identify a steep increase in ransomware attacks among its incident response clients. Fast forward to nearly the end of 2020 and not only are incidents becoming more frequent, ransomware operators have implemented tactics that often make it much more difficult for companies to respond and recover. In October 2020, ransomware was the top reported incident in over 45% of Kroll’s intake.
Professional services, healthcare and education organizations top ransomware targets in 2020.
In 2020, there have been ransomware attacks against organizations of all sizes across industry sectors. A high number of attacks, however, have primarily targeted three sectors: professional services, healthcare and education.
Professional services covers a broad swath of service-oriented businesses, such as real estate, accounting and law firms. Many are small to medium-sized businesses, and as such, are often considered attractive targets by ransomware operators who identify that these firms may not have the security defenses of larger organizations.
Healthcare organizations have been also highly targeted, even prior to the COVID-19 pandemic. In Q2 2020, Kroll saw a slight drop in ransomware attacks against healthcare organizations as national and state lockdowns rippled across the globe. At least one threat actor group, Maze, even went so far as to say they would quit targeting healthcare organizations during the pandemic. Such promises only went so far. Two days after that announcement, Maze posted data on their actor-controlled ransomware site (“shaming site”) that it stole from a vaccine research facility. In Q3, Kroll has observed the frequency of healthcare attacks is again on the rise. Kroll’s review of our October attack trends revealed a 75% increase in targeting against healthcare organizations, suggesting there was indeed an increased pattern of targeting against healthcare providers in October 2020.
Kroll has seen ransomware operators especially focused on the education sector, an observation which is corroborated by open-source reporting. From public school districts to trade schools, colleges and university systems, ransomware attacks have not only disrupted education for millions of students and staff, but also placed sensitive data at risk. In one highly publicized case, an attack reportedly resulted in the death of a patient when ransomware operators struck a medical center instead of its affiliated university that was the intended target.
Extortion through exfiltration ramps up pressure to pay amid regulatory complexities.
The exfiltration and publication of stolen data is a new trend that has become common practice in 2020. In Q1 2020, Kroll observed that only 22% of its clients were struck with a ransomware variant from operators known to exfiltrate data and publicly post it if ransom demands are not met. By Q3, such variants accounted for nearly one out every two Kroll ransomware cases.
Prior to these tactics, responding to a ransomware attack was often seen as a straightforward path between two options: restore from backups and don’t meet ransom demands or pay to obtain the decryptor to restore systems. Operational disruptions and financial considerations were often internalized, with public disclosure minimized or avoided altogether. Now that a ransomware attack may also necessitate a data breach response, organizations must ensure they are fulfilling their regulatory duties to inform clients and customers of the event in a timely manner.
Determining whether data was truly exfiltrated is not that straightforward. Victims have been told data was exfiltrated and yet no compelling proof was ever provided. Another scenario is when there’s evidence that treat actors have accessed data, but after review, the victim organizations finds that it is not considered sensitive data, e.g., personally identifiable information (PII), that would trigger a data breach response. Accomplishing all of this within today’s complex regulatory environment, with tight notification timeframes mandated by law, has enormously complicated an organization’s decision-making.
Recent advisories from the U.S. Treasury's Financial Crimes Enforcement Network (FinCEN) and U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) have also served as reminders that ransom payments carry regulatory implications, which organizations may have forgotten to consider in the midst of a crisis.
Threat actors quick to exploit pandemic-related work-from-home remote access.
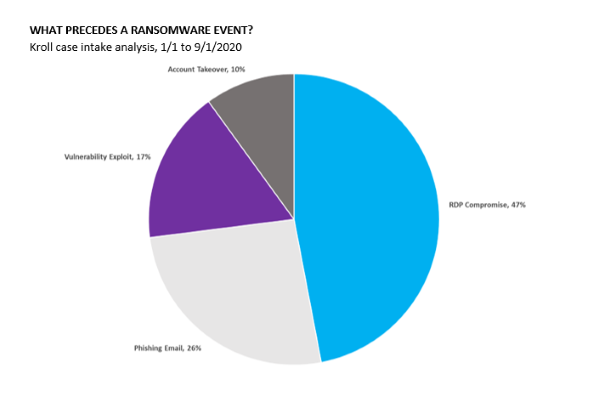
Remote desktop protocol (RDP), Microsoft’s proprietary network communications protocol, and virtual private networks (VPNs) have been frequent points of access for ransomware groups. In fact, recent research by Kroll observed that threat actors leveraged RDP in nearly half (47%) of Kroll’s ransomware cases so far in 2020. The massive transition to the work-from-home model that took place in the wake of COVID-19 immeasurably helped ransomware operators by making their attack surface that much larger. As information security teams had to pivot within days or weeks to a fully remote environment, ransomware operators looked for holes in RDP configuration or for vulnerabilities in VPNs that had not been patched.
Steps to take now before ransomware strikes
In Kroll’s experience, effective ransomware preparation is a blend of human-centered and technology-enabled strategies. Following are several best practices your organization should consider implementing as part of your overall cyber defense strategies:
Human-centered strategies
- Educate staff and continually raise awareness on cyber security topics, particularly phishing emails. Kroll has observed cases where the response to a phishing email has led to ransomware deployment in a matter of a few hours.
- With the guidance of legal counsel, leadership should consider governance questions in advance, such as how to address the potential regulatory ramifications of exfiltrated data or purchasing decryptors.
- Develop and regularly update your incident response plan and establish an incident response team with the knowledge and capabilities to carry out necessary tasks in the event of a cyber crisis. Consider having the team participate in a tabletop exercise at least annually to ensure they understand their duties and to identify gaps, uncertainties or other issues.
Technology-enabled strategies
- Regularly perform back-ups and, if possible, encrypt and isolate them from the rest of the network.
- Consider investing in endpoint detection and response solutions that enable 24x7 monitoring and response capabilities.
- Segregate sensitive data and regularly conduct data mapping inventories to understand your exposure in the event of a ransomware attack with data exfiltration.
- Keep current with patching software for all your systems. Institute a process, complete with stringent timeframes and accountability, for applying patches. You can sign up to receive the latest news on critical common vulnerabilities and exploits here.
The role of cyber threat intelligence
Threat intelligence can help active incident response/investigation and after the incident. Here’s how:
- Dark web threat intelligence can be used during the response to help identify malware variants and their associated actor group or validate threat actor claims of data exfiltration.
- Post-incident monitoring can provide visibility into ways exposed data can facilitate a wide range of other harms to your organization. These have included competitors leveraging your exposed trade secrets or intellectual property for unfair advantage; potential extortion of patients of victimized healthcare organizations; and targeted spear phishing or thread hijacking campaigns leading to wire or other financial fraud.
- Threat actors are also known to post vulnerabilities they discover in your environment on various niche dark web forums. These can leave the organization open to further attacks by actors who can move faster and perhaps even more stealthily since they know exactly how to get in and where to go.
As ransomware actors spin “value-added service,” commoditization portends more attacks in the future.
The commoditization of ransomware likely portends more attacks ahead. From Kroll’s broad experience investigating ransomware cases, we have seen how any organization in any industry can become a victim. Preparing for a ransomware attack today is imperative.