Product Spotlight
Product spotlight on security analytics

Security analytics can help security professionals not only improve risk mitigation, but also inform decision-making.
Security magazine highlights a few security analytics technologies that can help leaders gather new sources of business intelligence, add value to the organization beyond security, and enhance security measures with artificial intelligence (AI).
Alcatraz AI
Provides Facial Authentication Through AI and Analytics

Alcatraz AI’s Platform V2 enables third-party access control system software integration to help security stakeholders enhance their security posture. The platform leverages AI and analytics with touchless or multi-factor authentication, tailgating intelligence and video to improve physical security strategies. The platform enables software integrations to enterprise platforms, such as the Tyco Software House CCURE 9000 security and event management system from Johnson Controls. The Alcatraz API provides users flexibility if they require tighter integration between Alcatraz and their access control system. Image courtesy of Alcatraz AI
Find out more at www.alcatraz.ai
Ambient.ai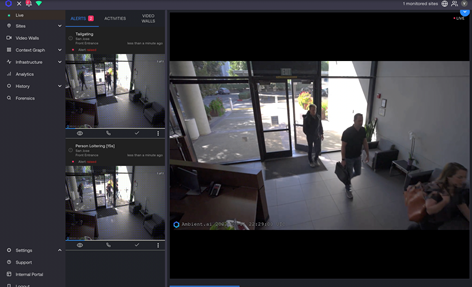
Offers Threat Detection and Response Capabilities
Ambiant.ai announced new threat detection and response capabilities to its computer vision intelligence platform, including the ability to identify weapons like firearms and knives and the precursors to high-severity incidents like unauthorized entry and crowd commotion. The update adds 25 new behaviors to a threat detection library so security and operations teams are alerted to threats and can intervene before incidents escalate. Early indicators of high-severity incidents, including sudden egress, tailgating, perimeter breaches, and more, can help security teams to intervene and increase their ability to prevent escalation. Image courtesy of Ambient.ai
Find out more at www.ambient.ai
Axis Communications
Offers AI-Based Object Detection
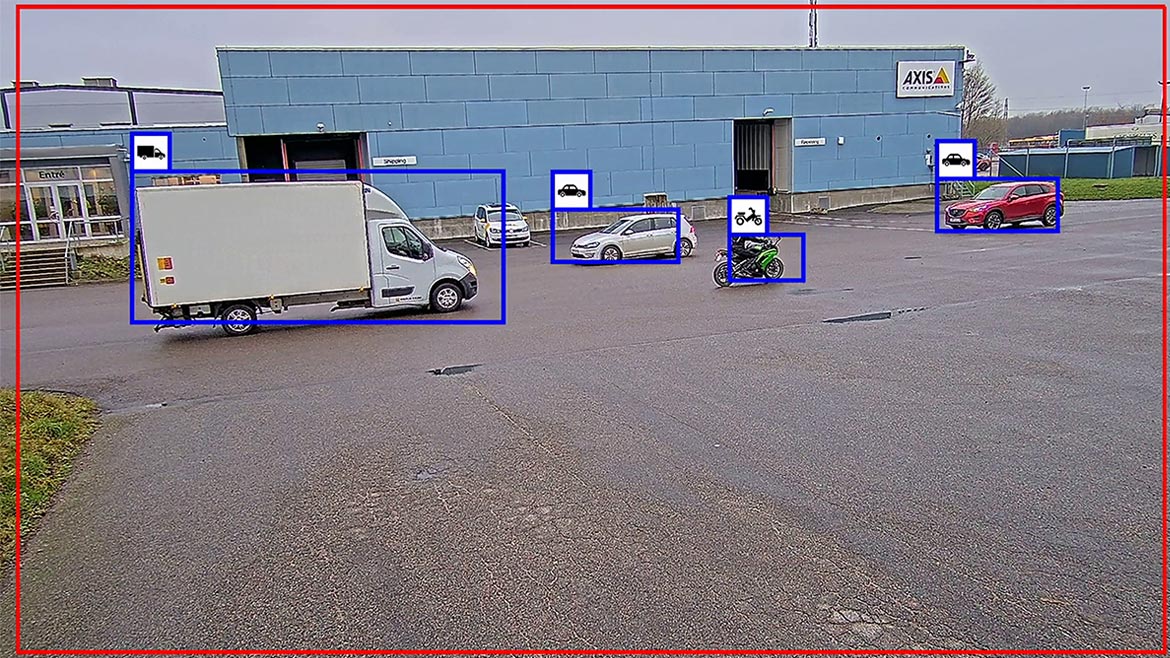
Axis Object Analytics is an AI-based video analytics solution that detects and classifies humans and vehicles. Usable in both indoor and outdoor situations, it is designed for monitoring to help provide users with business intelligence. With the interface, users can set up scenarios tailored to their monitoring needs and define behavioral conditions to trigger an event. Axis Object Analytics can also run multiple custom detection scenarios simultaneously. Axis Object Analytics’ time-in-area feature can detect when an object stays in a monitored area longer than a user-defined time, which is beneficial in maintaining the safety and security of any space. Axis Object Analytics comes preinstalled on compatible Axis network cameras. Image courtesy of Axis Communications
Find out more at www.axis.com
Azena
Turns Security Cameras Into Insights

The Azena platform for smart cameras provides AI-enhanced video analytic applications designed to run directly on a smart camera. Azena’s camera operating system enables smart cameras to run a variety of apps that can be downloaded to the camera and changed. With the platform, end users can monitor store flow to analyze and optimize merchandise lay out; scan crowds to identify people in a crowded area and get alerted if someone falls or is behaving unusually; improve traffic by detecting unauthorized parking and use license plate recognition to detect specific vehicles; get instant alert for threat at sites, including when detecting firearms or drones flying too close; and more. Image courtesy of Azena
Find out more at www.azena.com
BriefCam
Enhances Security Operations
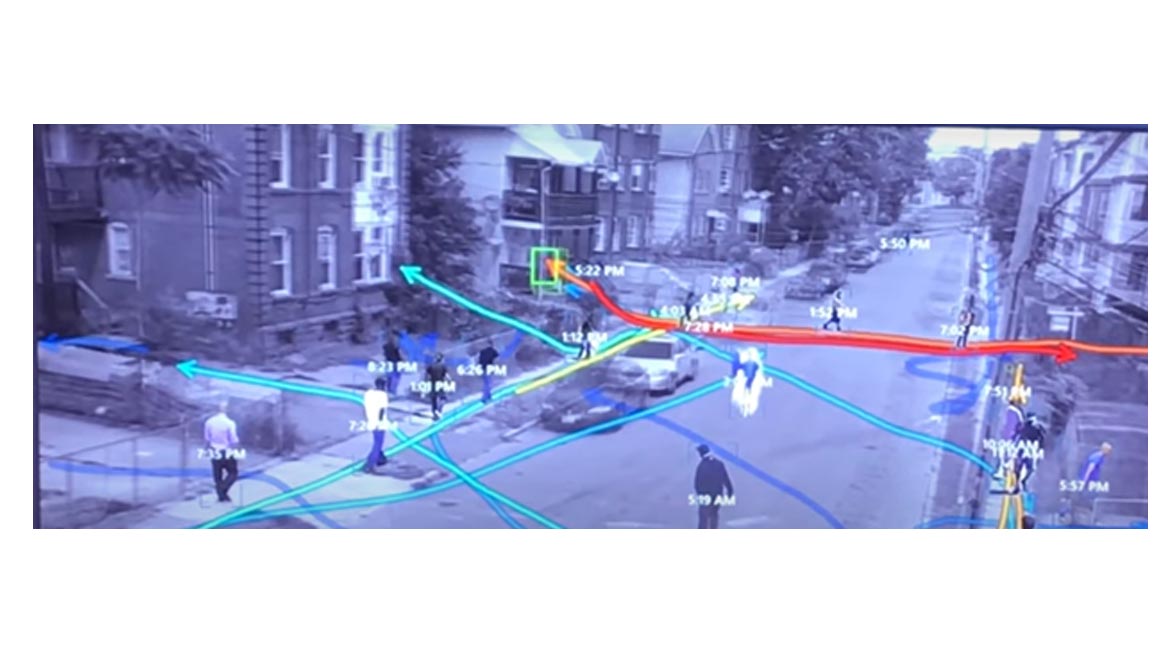
The BriefCam video analytics platform can help users enhance the value of their video surveillance system. By visualizing foot traffic patterns, bottlenecks, queues and crowding trends, demographic data, and staff and user engagement stats, the technology can help retailers, hospitality providers and others with their security operations. The video analytics platform provides insights for accelerating investigations, increasing situational awareness, and enhancing operational intelligence. In addition, video analytics can help improve user efficiency, safety and security, providing data intelligence for understanding user journeys, identifying inefficiencies, and developing solutions that drive user experience. Image courtesy of BriefCam
Find out more at www.briefcam.com
Camio
Delivers Security and Business Insights
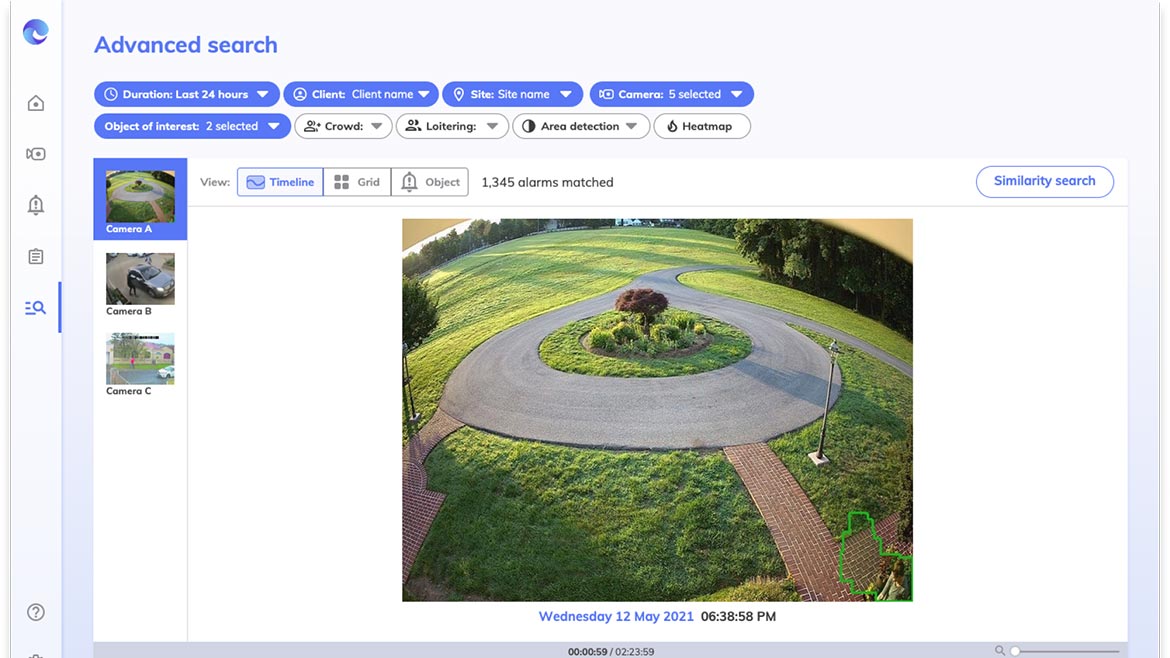
Camio uses standard IP cameras, AI and natural language video search to provide real-time analytics and automated alerts for proactive security instead of passive evidence collection. Camio analytics can help with unauthorized access detection — automated tailgating, door held open, door forced open — through integrations with Lenel OnGuard, OpenPath, AMAG, Brivo and CCure 9000, and other access control providers via open API. People, vehicles, color, direction, bicycles and optical character recognition, which allows the camera to recognize text like FedEx, UPS, Prime, produce trucks and license plate characters are other examples of analytics by Camio. The video search platform includes occupancy counting and dwell times to calculate how long people or vehicles are in specific zones to reveal common patterns or highlight unusual activity. Image courtesy of Camio
Find out more at www.camio.com
Calipsa
Helps Security Operation Centers Conduct Investigations

Calipsa’s enhanced video search offering enables security operation centers to conduct security investigations. The forensic software, Investigate Uploader, allows users to upload video files to the Calipsa platform, where its algorithms review the footage for genuine activity before presenting a summary of results. The security technology leverages AI and cloud-based forensic tools to conduct criminal investigations. The technology transforms real-time streaming protocol (RTSP) video into a series of frames showing objects of interest. The Similarity Search feature allows users to upload an object of interest which Calipsa’s algorithms use to search for objects of similar appearance in the uploaded video. All forensic video results will be summarized in a video that can be shared with stakeholders. Image courtesy of Calipsa
Find out more at www.calipsa.io
Identiv
Improves Security and Situational Awareness
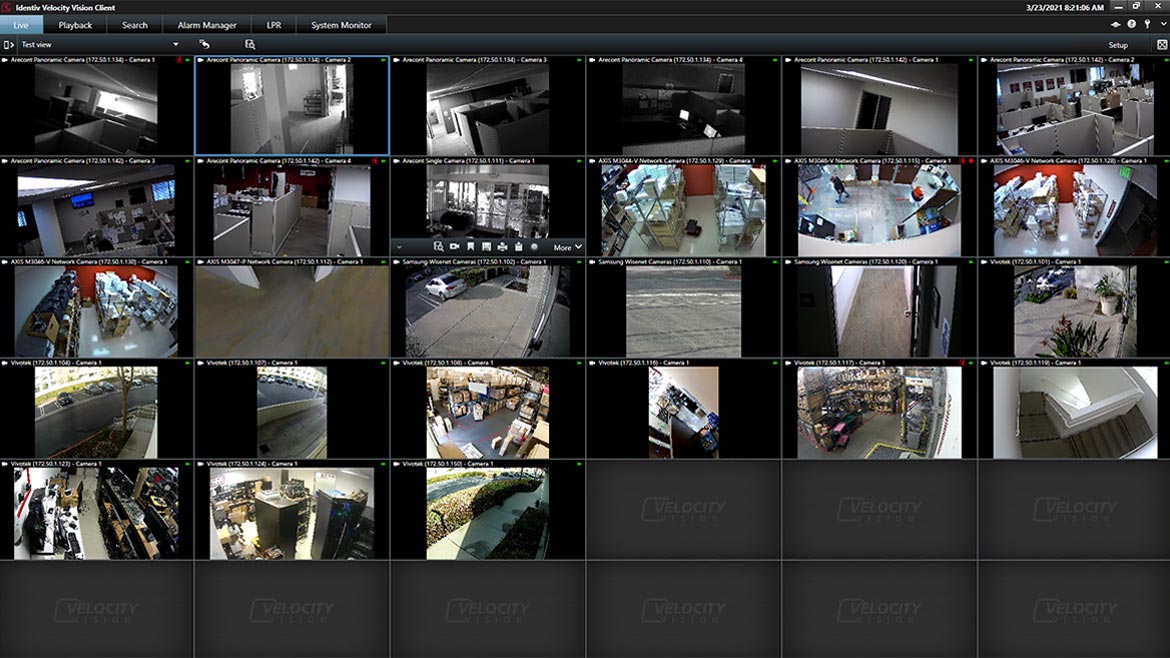
Identiv’s Velocity Vision is a unified, open-platform video management system (VMS) built to provide a data-enabled security solution that delivers intelligence and improves security operations. The open platform learns and automates security over time by working with existing investments and providing situational awareness. In addition, the open API platform supports thousands of devices, over 8,500 camera models, and combines with more than 15,000 ONVIF-compliant solutions. Velocity Vision works with security technologies, such as AI, GPS, access control, and building management. Image courtesy of Identiv
Find out more at www.identiv.com
i-PRO
Helps Security Officers During Investigations
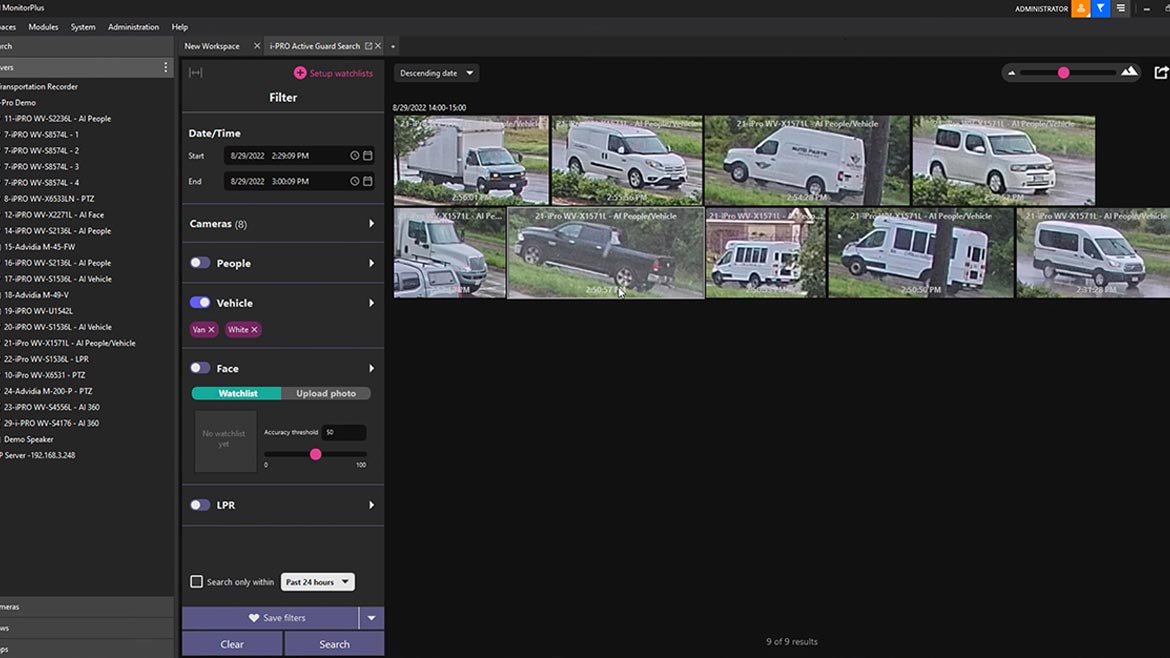
i-PRO Co’s latest version of Active Guard plug-in can help turn video management systems (VMS) into search engines. The version adds support for Milestone Systems’ X-Protect and i-PRO’s ASM300 software and features a number of search attributes and enhancements that can help security officers conduct real-time and post-event searches. It allows users to manage AI analytics from i-PRO cameras and allows users to set up search parameters based on a number of search attributes, including gender, age, clothing color, facial characteristics, vehicle color and direction, and more. Operators can register specific characteristics in their watch lists and the VMS will send them alarms whenever a match is identified to enhance situational awareness. The same process can be set up for data mining of events during forensic investigations. Image courtesy of i-PRO
Find out more at www.i-pro.com
Salient Systems
VMS Incorporates Analytics and Intelligence 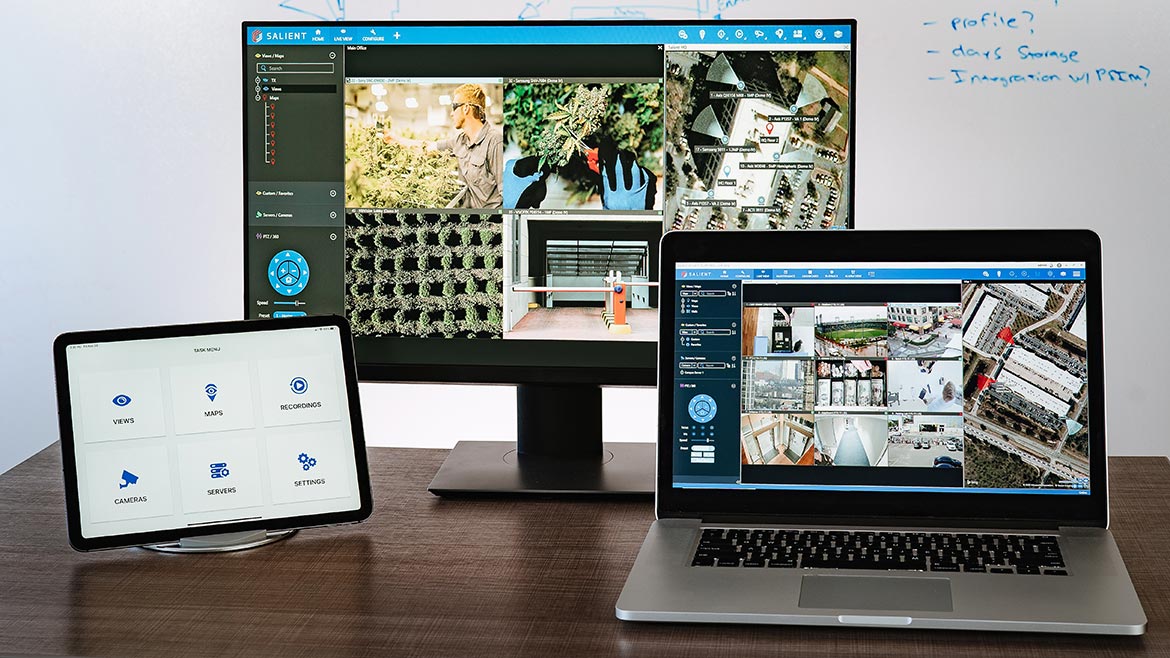
The open platform video management system from Salient Systems enables integration with video analytics features from alternative vendors or software systems and is customizable to the needs of the end user. The CompleteView video management system allows organizations to view, record, search and manage video data. Users can access live video, playback and export recorded video and control cameras with PTZ functions from their phone or web browser for improved remote management and monitoring. In addition, CompleteView provides enhancements such as the creation of storage pools with improved backup, overflow capabilities, and camera-based retention policies, including predictive storage analytics. Image courtesy of Salient Systems
Find out more at www.salientsys.com
Vintra and Milestone Systems
Adds AI-Powered Video Analytics to Cameras or Video Streams
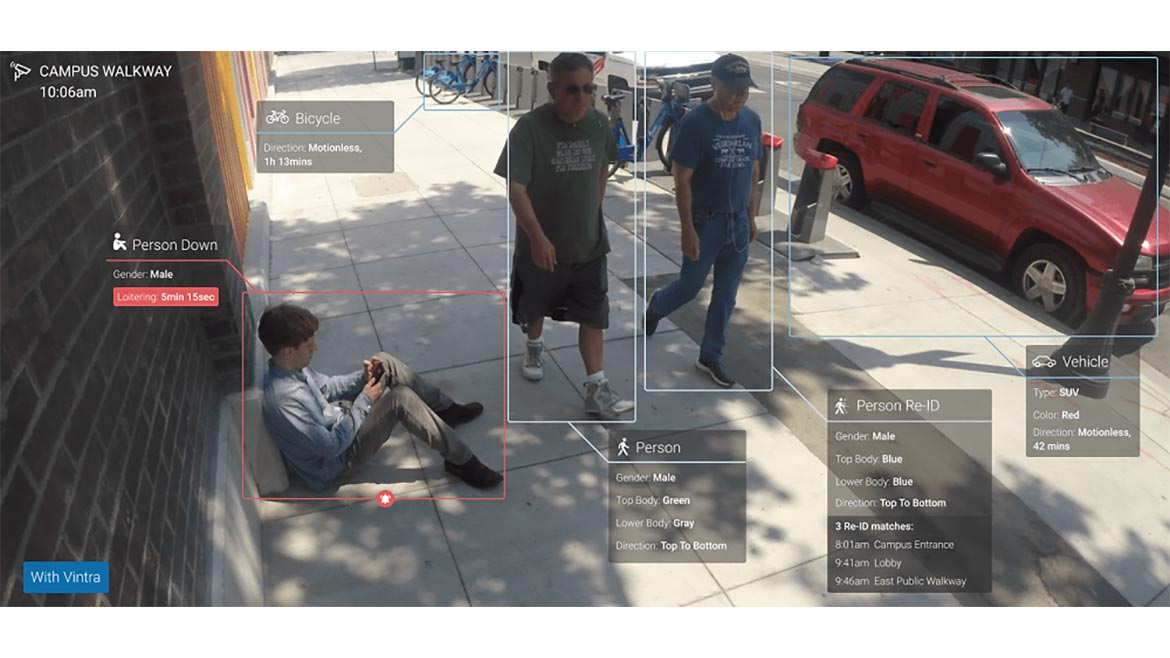
Vintra Fortify, a video intelligence solution, is now integrated with Milestone Xprotect, a video management software. The integration provides connectivity between the two security technologies to help users better manage their full video experience. Milestone XProtect users can add AI-powered video analytics to any fixed or mobile camera or stored video, giving them the ability to apply analytics to specific cameras. The rules engine within Vintra Fortify enables a combination of alerts to be produced, featuring “smart muting” to train the system over time, minimizing false alerts. Vintra Fortify also features pattern analysis technology that helps users locate individuals or objects across multiple video streams, providing information regarding the journey of that individual or object. Image courtesy of Vintra and Milestone Systems
Find out more at www.vintra.io or www.milestonesys.com
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





