Creation of a customized college student cybersecurity awareness online learning solution

Many businesses, agencies, for-profit and non-profit organizations have implemented cybersecurity awareness training programs for their staff. This makes perfect sense given the importance of the last line of cyber defense existing with a person. Although businesses have been wise to administer cyber awareness training, it is equally essential for such a practice to occur for students in higher education. As students enter the realm of pursuing their said and interested degrees, they will most definitely be using technology in both the academic setting and in their private or personal lives. Students are often very busy with their studies, perhaps also working to supplement their education, involved in sporting and other extracurricular activities, and with this time constraint can make them vulnerable to cyber threats. This short write-up will outline a short case study of a developed cybersecurity defense and awareness training system for students at Kean University. The created and ultimate technical solution was engineered by D2 Cybersecurity, a firm that partners with educators and government agencies to create industry environment-appropriate and comprehensive training solutions.
Although cybersecurity awareness training can be valuable to all students, a survey on the topic found that it can be particularly effective among non-Computer Science or Information Technology majors. The reasons are many, but the reliance on technology as students for their coursework and their personal affairs can be valuable to share with family and friends.
Kean University Student Cybersecurity Awareness Training Solution
All incoming Freshman, as well as transfer students to Kean University, are presented with a cybersecurity awareness training module as part of their transition to the university. This timing is appropriate as students begin their journey and will most certainly rely on technology in their learning. Additional cybersecurity awareness resources are made available to the campus community and the external community on the Center for Cybersecurity resources website.
The particular modules in the training can be adjusted and have recently been modified to reflect the following five key or core foundational and relevant cybersecurity awareness or hygiene topics:
- Phishing and Ransomware
- Web Browsing and Social Media
- Passwords
- Mobile Security
- Public Wi-Fi and Home Networks
Selection on the current key learning modules were selected based on the most prevalent variety of malicious attacks and threats that can be experienced by students.
In addition to educating and bringing awareness to understand the variety of threats that exist in cyber, the developed training solution provides recommendations for students to consider should they end up a victim. For example, if a student became the victim of a Phishing attempt, suggestions for the next immediate steps are provided to help the student with approachable guidance. This same Phishing exploitation could involve immediately changing passwords of compromised accounts; updating security settings, contacting the institution and Information Technology administrator, and possibly notifying a major credit bureau.
The customized solution is presented to students for approximately 45 minutes, depending on the length of time required to complete the interactive assessments peppered through the training. The solution is engaging in providing videos, cartoons, photos, and bright graphics that are both culturally appropriate for a diverse population but specific to the needs of college students. In one study, it was suggested that using well-thought-out exercises relevant to the students’ experiences and appropriate with their level of cybersecurity knowledge can make a positive difference in their awareness.
Overarching Benefits of Student Cybersecurity Awareness
There are many benefits to students and all those around them regarding understanding cyber threats through awareness and employing proper cyber hygiene. Bringing a focused set of content topics on cyber defense and awareness strategies will help students to be well prepared while engaged in coursework and other college-related activities. In turn, with student’s better cybersecurity prepared and aware, the schools and colleges of the students will be in a better frame than if the students were not put through awareness training. Additionally, as the students embark on their desired careers, they will most certainly include the use of technology, and it is expected that they understand the importance of data protection and cyber defense.
Cybersecurity Training Technical Implementation
The current web-based training system is hosted on a Windows-based server utilizing the Open-source Moodle Learning Management System. Updated training modules were created and available using HTML5 to permit use on a variety of browsers and devices (tablets, smartphones, desktops, and laptops) and exclude the need for such add-ons as Flash. The system is administered with staff in the Center for Cybersecurity at Kean University. Tasks often associated with the training provisioning are ensuring all incoming freshman, as well as transferring students, are configured to receive automated emails with instructions for logging into the site and gaining access to the training modules.
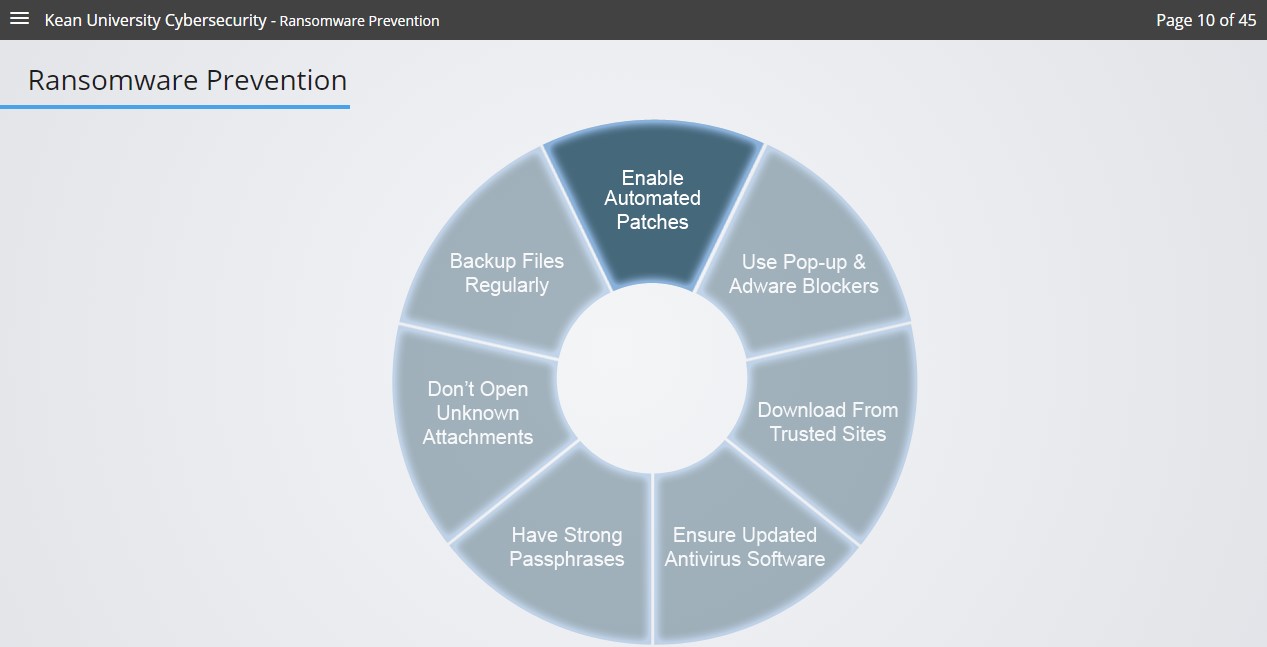
The inclusion of interactive screens will contribute towards a mixture of learning content and keep the student engaged. In Figure 1 below, the created solution encourages students to click on a segment to gain further knowledge surrounding Ransomware prevention.
Figure 1. Ransomware prevention interactive screen.
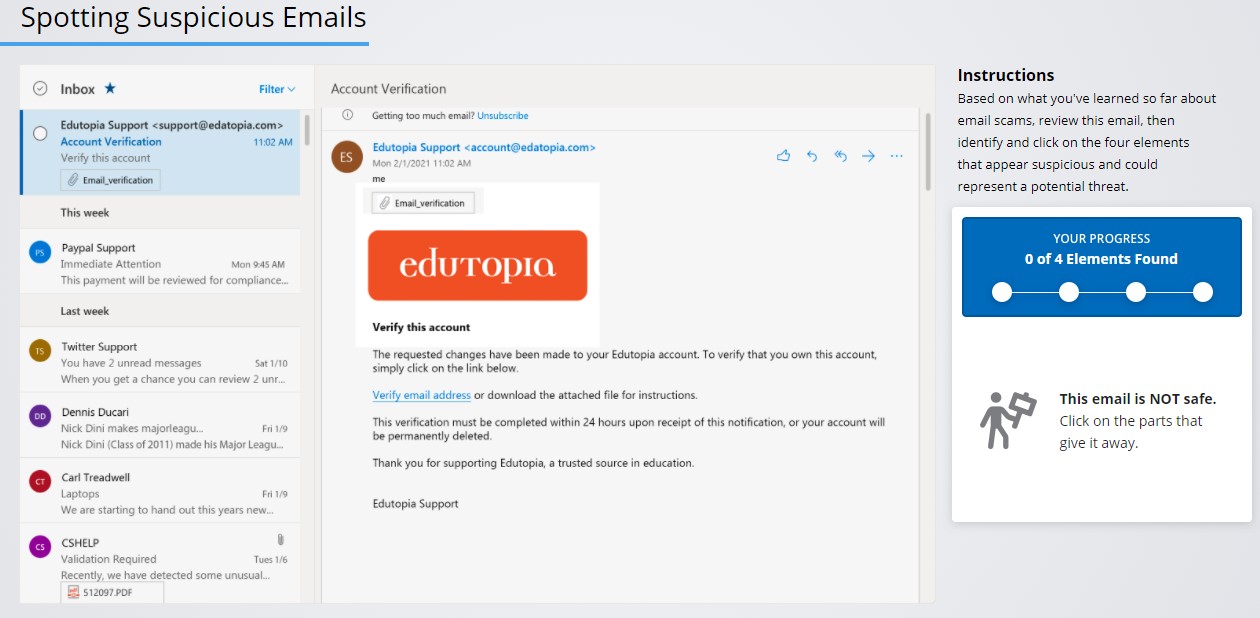
In another interactive example, Figure 2 demonstrates a suspicious email and challenges the student to click on four elements that are considered suspicious and represent a potential threat.
Figure 2. Scam email identification of elements.
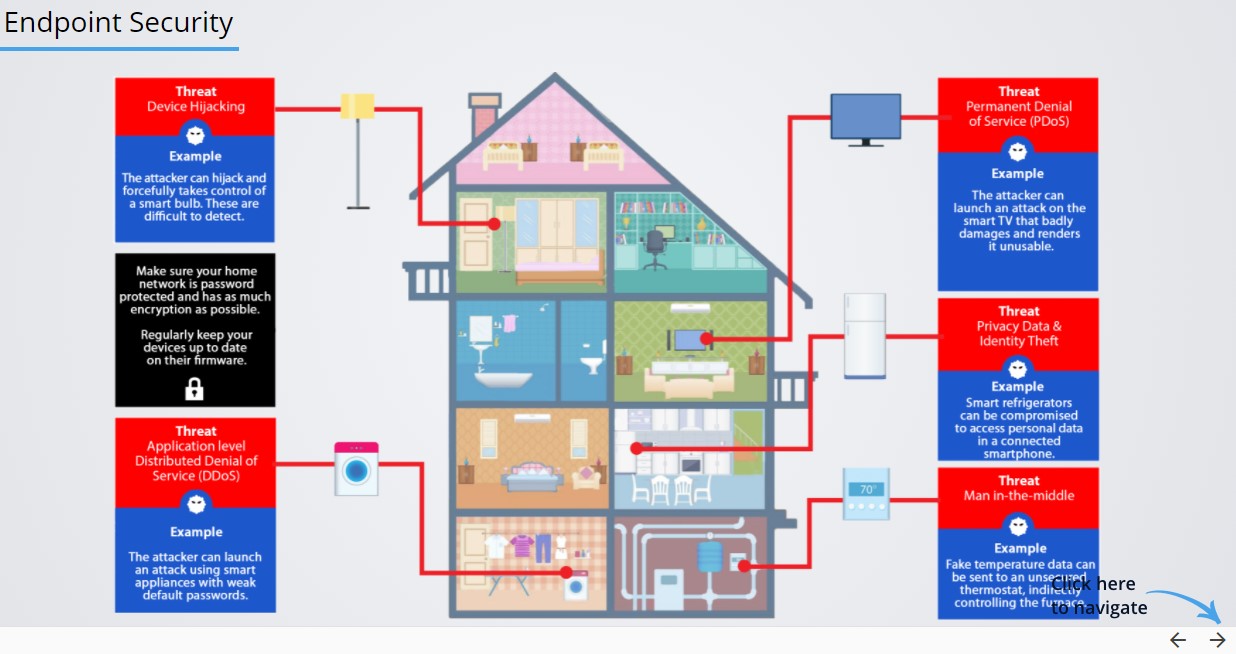
Given the incredibly fast pivot to taking courses from home or away from the classroom as a result of the COVID-19 pandemic, threat content related to technologies more often used at home, such as Wi-Fi, routers, smart devices, and mobile devices, is included in the solution.
Figure 3. Protecting and awareness of smart device threats.
Relevance of Student Cybersecurity Training Outside of Awareness
Having in place a cybersecurity awareness outreach training program in place can add value in areas outside of protecting the students and university. For those institutions pursuing the National Security Agency Center for Academic Excellence in Cyber Defense designation, there exists a requirement to demonstrate evidence of a sound cybersecurity posture and plan. A suggestion for such evidence is to reveal the institution’s plans and practices for employing awareness training. Providing staff and students with the necessary resources and easily available will provide towards this need. In other potential examples, any organization going through an internal or external assessment on cybersecurity or information security will undoubtedly include the topic of staff, employee, and possibly third-party cyber awareness training and will only add positive value for those reviewing the practices of the audited firm.
Conclusion
The current cybersecurity education and awareness market include many different vendor products from which to choose. Such solutions can meet a variety of organizational needs. Regardless of the solutions selected by educational institutions, it will be important to keep the content updated, relevant, and engaging for the student population. Having the ability to customize a solution for college students is important, and will resonate with this population if aligned with technologies the students may be using. For example, current students have become familiar with cryptocurrency, and thus, having cybersecurity awareness training that includes at least some content on the topic will add value.
Taking cybersecurity awareness further, formal academic programs in cybersecurity exist in the Kean University Criminal Justice programs in the College of Business and Public Management as well as the Information Technology and Computer Science programs in the College of Natural, Applied and Health Sciences. Calls have been made to promote universities and, specifically, business schools to mandate core cybersecurity training and privacy protection in their programs and not just computer science. Over the past several semesters, one common observation made by the author is the trend of students taking introductory courses in Cybersecurity from many disciplines, including Psychology, Communications, STEM, and Computational Science and Engineering. This is a valuable addition to a student’s background, regardless of their chosen academic and career aspirations.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!








