Access control systems (ACS) data can help organizations get back to the office

<a href="https://www.freepik.com/photos/business">Business photo created by tirachardz - www.freepik.com</a>
We don’t know the full impact that COVID-19 and our response to it will have on our future. But we do know that it has already changed our lives. From the ways we interact and socialize to how we appreciate medical teams and delivery people, things are different. While many of the changes have been accompanied by very real hardship, they have also allowed us to re-examine situations and processes.
As countries roll out vaccines, organizations are planning for the new normal. Many are asking questions they’ve never considered before. In addition to trying to determine how long they will have to manage occupancy rates to reduce the risk of transmitting the virus, they’re also thinking about where employees will work and how.
Once it is safe to do so, will employees return to the office full-time or will companies opt for hybrid scenarios in which some time is still spent working from home? And how will organizations be able to make informed decisions that are safe for their employees and respect their bottom line?
Use data for occupancy management
Now is a good time to re-examine how we work. We can no longer assume that the best scenario is to have everyone in the office Monday to Friday from 9 to 5. But making changes will require that organizations think about right-sizing their real estate portfolio to match the number of people going to the office at any given time.
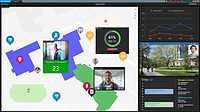
Occupancy management has been top-of-mind for over a year. Ensuring that space doesn’t exceed government thresholds has been important for mitigating the spread of the virus. Moving forward, organizations that are using their access control systems (ACS) for people counting can take advantage of the data they are collecting to help with office management.
By deploying an office management solution that aggregates and analyzes the data from existing ACS systems, organizations can leverage what they already own to better understand how employees are using space within their facilities. Working with pre-set thresholds, this type of solution can determine how frequently an individual comes into the office and how long they stay. Then, with this data presented visually on a dashboard with clear metrics, an organization can get an accurate picture of how their facilities are being used, which can help them achieve a smaller footprint in the future.
For example, an office management solution could compare how many employees are coming into work on different days of the week as well as determine peak days on different floors. With these insights, organizations can determine how many employees require permanent or shared desks to then make informed decisions about how much space they actually need.
Automate procedures and processes
Organizations can also use ACS data to quickly change and automate standard operating procedures (SOP) to help control how people move through their facilities. At the beginning of the pandemic, organizations developed SOPs in response to government guidelines to ensure proper physical distancing, effective screening processes, and proper surface cleaning protocols. However, with guidelines rapidly evolving, it has become difficult for many to quickly adjust their traditional SOPs and then effectively train staff on the new procedures to follow.
A collaborative decision management system makes it easy to update SOPs for an individual facility or an entire organization. This eliminates the need for constant training and ensures compliance as the system guides operators through new processes. More advanced systems can also allow an organization to automate workflows. For example, using ACS data, a system could automatically alert personnel that bathrooms in a specific area need to be cleaned in response to changing occupancy levels.
Focus on protecting systems and privacy
Cybersecurity will continue to be a major concern as organizations develop their back-to-the-office plans. When employees began working remotely, the value of implementing a defense-in-depth strategy became clear. The first step in this strategy is to partner with vendors who have a proven track record of developing solutions that mitigate against the risks of cyber threats.
Next, organizations must continuously monitor their networks and devices for possible signs of a breach and have a clear plan of action for when a potential breach is discovered. Additionally, they should also engage in other security best practices, which include ensuring that devices have a strong password schema to protect against unauthorized access and that firmware is always up-to-date.
Finally, it is important to remember that gaining actionable insights from the data collected by a physical security system requires paying close attention to privacy. The ability to keep individuals anonymous on video through masking and using redaction tools is key. Solutions that are developed with privacy in mind can help organizations continue to protect individuals as we move into the new normal.
This article originally ran in Security, a twice-monthly security-focused eNewsletter for security end users, brought to you by Security Magazine. Subscribe here.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!