How to maximize traffic visibility with virtual firewalls
Few cybersecurity components are as familiar as the next-generation firewall (NGFW) for enterprise protection. Despite this ubiquity, it is common for security teams to operate their NGFW in a suboptimal manner. The TAG Cyber team has observed, for example, that many enterprise teams operate their NGFW more like a traditional firewall. This can result in a reduction of traffic visibility, which in turn degrades prevention, detection, and response.
The reasons for such degraded firewall operation will vary, but a common issue is the flexibility of managing and supporting the powerful features in an NGFW. It is obviously easier to enable a minimum of firewall features, and this is especially common in environments where the security team might be under-staffed. A promising approach that can help address this challenge involves use of a so-called virtual firewall.
Most security professionals consider virtual firewalls as a tool for protecting private and public cloud workloads and applications, but the reality is they have all the same features as physical appliances. When deployed fully, virtual firewalls can scale encrypted traffic inspection across distributed networks, establishing the visibility necessary for reliable threat protection, even in today’s challenging security landscape.
Perhaps more importantly, because virtual firewalls are implemented in software, the set-up, maintenance, support, and operational requirements for security administrators will be necessarily lower than for their physical counterparts. For this reason, we recommend and make the case below that virtual firewalls are an excellent option to help close visibility gaps for enterprise traffic inspection, analysis, and response.
Rising Traffic Encryption Levels
Evolved from original five-tuple security devices pioneered by companies such as Checkpoint and Cisco, the NGFW continues to serve as an architectural chokepoint for securing organization resources, even in the presence of shifts to more software-defined virtual perimeters. For many teams, the purchase of a commercial firewall platform can easily rise to the top of their overall cyber security portfolio budget spend.
Most commonly, this involves running the firewall as a conventional packet-oriented device versus taking full advantage of application-level inspection and filtering capabilities. Security experts refer to this approach as operating the firewall at layer 3 (routing) versus operating at layer 7 (application). Making matters worse is that an increasing percentage of end-to-end traffic, both into and out of an enterprise, is now encrypted using secure sockets layer (SSL) or transport layer security (TLS). While this is effective at preventing data in transit from being disclosed to unauthorized adversaries, it complicates the task of collecting and interpreting data to make security decisions. The resulting lack of visibility degrades a security team’s ability to take proper action.
Conventional vs. Virtual Firewalls
To address this visibility challenge for encrypted and cleartext traffic, virtual firewalls provide unique advantages for modern multi-cloud environments. First though, it’s important to consider the pros and cons of both conventional and virtual firewalls.
Budget
Comparison of virtual and physical firewalls must include examination of their respective deployment and operation approaches. Each type has its respective procurement advantages. For example, physical firewalls are more attractive in environments with ample capital budgets, whereas virtual firewalls – as software – might be better suited to teams preferring to use operating expense.
Management
Similarly, each type of firewall will have its management advantages in a typical enterprise architecture. Physical firewalls have had the advantage, for many years, of lending well to the management of chokepoint-style gateways, often where the corporate local area network (LAN) meets the Internet. Virtual firewalls, in comparison, are better suited to cover the distributed aspect of modern software defined perimeters in hybrid multi-cloud architectures.
A virtual firewall specifically supports network policy enforcement, traffic inspection, and rule-based filtering in a virtualized environment. It will inspect packets or offer higher-level application security using policy rules to coordinate ingress and egress traffic between virtual machines (VMs) or cloud-hosted workloads. As one would expect, virtual firewalls are deployed as software, which makes them easier to provision, maintain, manage, and afford.
Figure 1. Physical Versus Virtual Firewall Coverage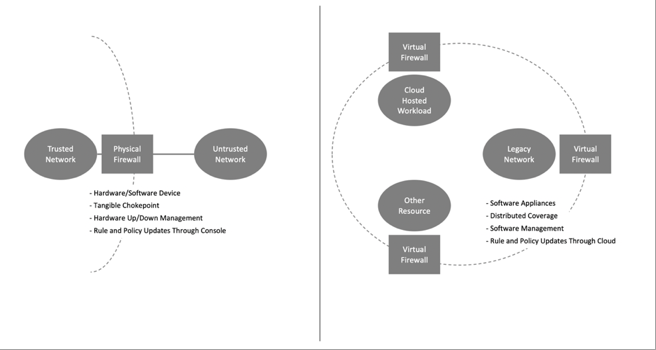
Because virtual firewalls are just software, they introduce many different options for their integration into the environment – including how they work with local switches, routers, servers, and other network elements. Virtual firewalls can be deployed in so-called bridge mode, where they reside in the network path to process traffic, or they can be embedded in a hypervisor kernel to inspect and manage communications into and out of a VM.
Operation
The traditional advantage of physical firewall platforms is their ability to reside in the actual network path between internal and external resources. This can provide better means for matching up a firewall architecture with the performance and load characteristics of an environment. Furthermore, firewall platforms as separate devices will not impede the performance of any other workload running in a shared virtual environment.
Virtual firewalls, in contrast, often require software-based control, perhaps by the hypervisor, of all routing and switching traffic. This allows for much greater flexibility of operation and for a more coordinated orchestration of policy, filtering, and monitoring. Furthermore, a virtual firewall might be embedded into an existing device such as a load balancer that might support virtual extension. This offers the best of both physical and virtual operation.
The Advantages of Virtual Firewalls
The biggest advantage of a virtual firewall, however, is its support for the obvious dissolution of the enterprise perimeter. Even if an active edge DMZ is maintained through load balanced operation, every enterprise is experiencing the zero trust-based extension of their operation to more remote, virtual operation. Introducing support for virtual firewalls, even in traditional architectures, is thus an excellent forward-looking initiative.
An additional consideration is that cloud-based functionality requires policy management for hosted workloads – and virtual firewalls are well-suited to such operation. Operating in a public, private, or hybrid virtual data center, virtual firewalls can protect traffic to and from hosted applications. This can include connections from the Internet, or from tenants located within the same data center enclave.
One of the most important functions of any firewall – whether physical or virtual – involves the inspection of traffic for evidence of anomalies, breaches, or other policy violations. It is here that virtual firewalls have emerged as offering particularly attractive options for enterprise security teams building out their threat protection. This is thanks to two features:
- First, the distributed traffic inspection offered by virtual firewalls results in highly scaled visibility of the software-defined boundaries supporting segmented architectures.
- Second, the centralized orchestration indicative of virtual firewalls in zero trust networks enables improved tailoring of firewall functions across all protocol layers.
Greater Traffic Inspection with Virtual Firewalls
The inspection advantage is rooted in the distributed nature of virtual firewall network coverage, as well as the ease with which they can terminate and inspect encrypted traffic. This network traffic inspection by virtual firewalls is complicated in modern networks by the growth of encrypted traffic, designed to reduce disclosure risk. Application-level firewalls are particularly susceptible to this visibility problem, because encryption becomes more prevalent across additional layers of the protocol stack. The specific risk is that within SSL/TLS encrypted connections, one might find both legitimate traffic and malicious content. Since the role of the firewall is to enforce policy between trusted and untrusted entities, it will not be able to fulfill this obligation to prevent malicious content if the contents of a connection cannot be identified. This is the basis for the technique known as full or deep SSL inspection.
To optimize both plaintext and encrypted traffic inspection at the firewall, and to ensure proper scaling of this function for enterprise networks of different sizes, virtual firewalls typically include functionality to terminate and inspect encrypted traffic. This is not something that instantly comes to mind for a network architect who equates virtual firewalls with the protection of private and public cloud workloads and applications.
The reality instead is that virtual firewalls have the same features as their physical counterparts. With a method of using virtual instances built out into arrays, network architects can actually build up enough inspection scale to deal with the traffic inspection requirements of a gateway. This results in the best of both worlds for virtual firewalls: Expanded scale across distributed networks and support for encrypted traffic termination and inspection.
Centralized Management of Virtual Firewalls
The management of traditional firewalls has always required special administrative tools that provide a practical means for writing policy rules, collecting logs, and dealing with outages. Because traditional firewalls operate at checkpoints between trusted and untrusted networks, their management can only be done in-band through the networks over which traffic passes, or out-of-band through clumsy side connections.
A huge advantage of virtual firewalls, given their flexible deployment and operation, is that management can be done from cloud-positioned virtual platforms which can orchestrate policy management and other administrative functions. This is often provided by the virtual firewall vendor, but it can also become embedded in separate management and workflow tools from commercial vendors. Interestingly, the hosting of virtual firewall capabilities on existing devices running cloud operating systems – including load balancers or servers – offers a creative means for deploying virtual firewall support without having to make large changes to existing networks.
Virtual Firewalls Ensure Threat Protection
There is no escaping the reality that SSL/TLS encryption levels are on the rise. We wouldn’t want it any other way; this encryption protects sensitive data from interception and dissemination. At the same time, though, inspection of traffic for anomalies, breaches, or policy violations is becoming increasingly challenging. Gaining full visibility might be expensive or cumbersome with conventional firewalls. However, with the distributed nature of virtual firewalls, security teams can quickly, easily and affordably scale traffic inspection without making huge network architecture changes. Even better, these virtual firewalls can be managed centrally, using a familiar, cloud-like interface. With these benefits, organizations with legacy enterprise networks will likely gravitate to this type of virtualized firewall hosting in order to ensure reliable threat protection.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






