Pharmaceutical industry sees increase in mobile phishing encounters

Lookout's newest Pharmaceutical Industry Threat Report shows attackers have turned to spear phishing campaigns to steal employees’ login data or deliver malicious payloads to their mobile devices to compromise the infrastructure of pharma companies.
Malicious actors are focused on mobile phishing because they can use any of the hundreds of apps the average person has on their mobile device. Attackers can socially engineer targets on a personal level through social media apps, messaging platforms, games, and even dating apps. An attacker will target particular individuals, including heads of research, manufacturing plant managers, sales leaders, or company executives, to gain privileged access to the data they want.
Lookout research shows that there have been multiple reports of foreign adversaries targeting pharmaceutical industry executives with mobile spear phishing attacks. Both the National Cyber Security Centre in the U.K. and the Cybersecurity & Infrastructure Security Agency in the U.S. issued advisories to organizations involved in the COVID-19 response to shore up their security practices.
Since most employees use either a smartphone or a tablet, or both, to access data within their infrastructure, the risk surface is widespread. To help protect and secure iOS, Android and ChromeOS devices, IT and security teams have used the NIST Special Publication 800-124 as a framework to develop their strategy to secure mobile devices.
The rate at which devices encounter mobile phishing, app threats, device threats and risky networks is increasing. Here are some findings from Lookout telemetry from almost 200 million devices and over 125 million mobile apps:
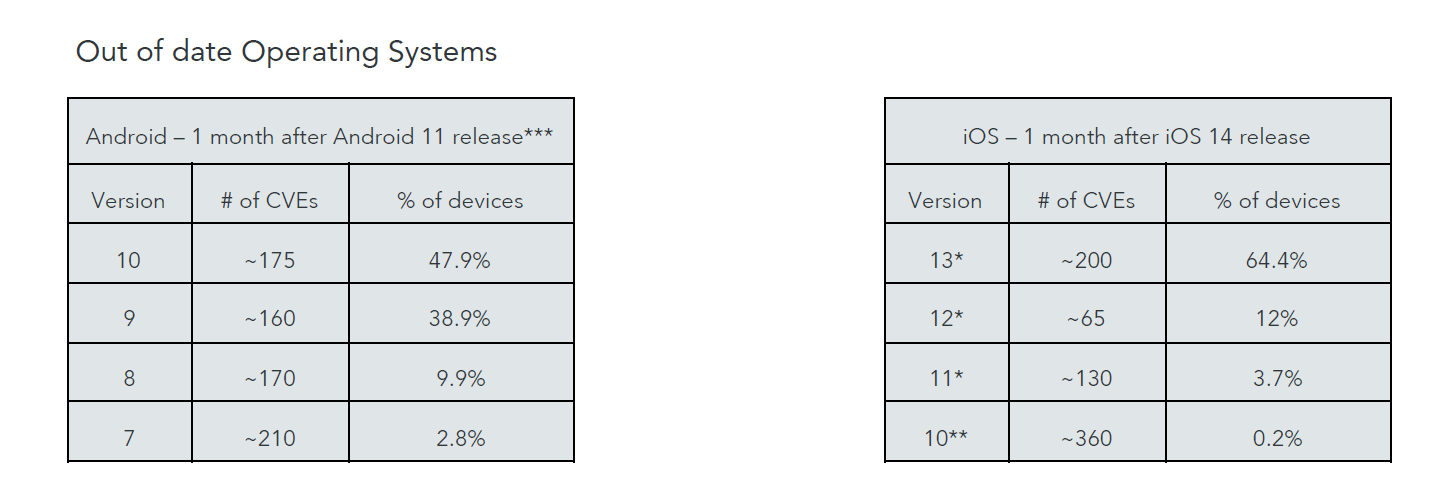
According to Lookout, while operating system CVEs (Common Vulnerabilities and Exposures) are patchable, there are still some obstacles to overcome such as:
- CVEs are known exploitable vulnerabilities attackers can actively target to take over a device or surpass its built-in security measures.
- Patching usually requires action by the mobile user to update the device.
- If an employee is running an old OS version, they’re walking around with a doorway to your organization’s data in their pocket.
capabilities. Only with visibility into endpoint and app vulnerabilities will you know exactly where vulnerabilities exist and when
they need to be updated to prevent those vulnerabilities from being exploited by threat actors," says the research.
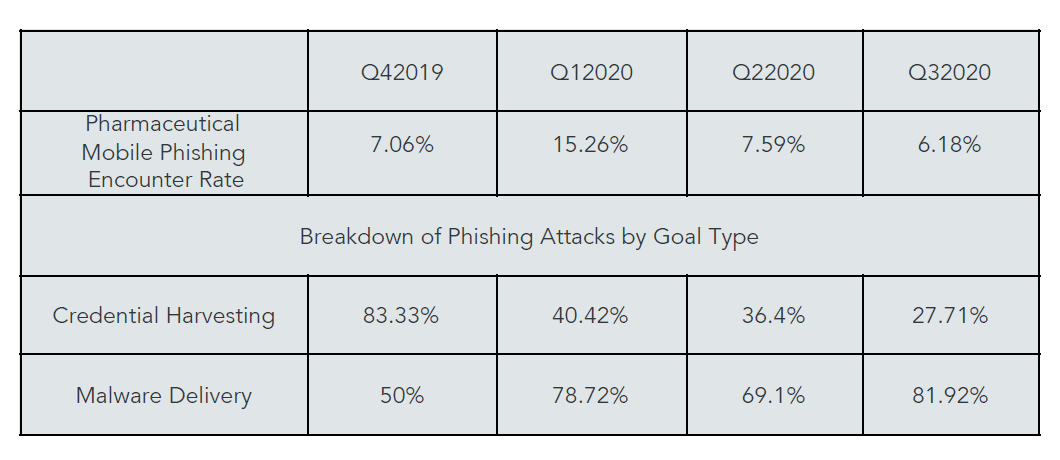
- Attackers are investing in more complex malware delivery methods and using phishing links to deliver malware to the device.
- Social engineering can convince an employee to download a sideloaded app just as well as it can convince them to enter their login credentials in a fake site.
- Successful delivery of spyware or surveillanceware to a device could result in longer-term success for the attacker.
- Attackers want to be able to observe everything the user is doing and look into the files their device accesses and stores.
To help protect mobile devices from cyberattacks, Lookout recommends pharmaceutical organizations use modern endpoint protection solutions that can detect mobile threats in apps, device operating systems and network connections while also
protecting against credential harvesting and malware delivery attacks through phishing.
For more information, please visit https://blog.lookout.com/pharma-report-3-out-of-4-phishing-attacks-attempt-to-deliver-malware
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!








