The Dangers from Knife and Weapon Slashing
On Monday morning, April 18, 2018, an 8 year-old boy left home with a kitchen knife and walked into his central Minnesota elementary school. Minutes later, he slashed three fellow pupils, ages 8, 9 and 13 years.
It was an example of how once again, a perpetrator doesn't need intense knife training to cause damage to others, and homeland security professionals or enforcement agents must accept that anyone carrying a knife represents a real danger, even if he/she appears that they don't have a clue as to what they are doing.
Those who know how to effectively use a knife understand that with knife combat, stabbing and blood loss will not necessarily and quickly incapacitate an attacker. Combat expert and author Michael Janich has done excellent research on this topic, and after careful analysis of forensic data, modern trauma medicine and consulting with experts on this subject matter, Janich’s research concluded the same sentiments.
In an article, “The Realities of Knife Stopping Power”, Janich discusses a case where a combatant received 50 stab wounds and still managed to fight for five minutes before collapsing due to collective blood loss.
In a self-defense situation (or in a situation where your operation requires you to incapacitate an assailant), every second counts. If you wound an attacker, but he still has the ability to do the same to you, you still may die.
When/if someone is knowledgeable enough and his intention is to immediately incapacitate you, it's important to understand human anatomy.
To hold anything in your hand, such as a baton, CS gas or shield (if you are a police officer), the muscles of your forearm contract and pull on the flexor tendons, which pass through your wrist and are attached to your fingers. If someone cuts or slashes the tendons or the muscles that power them, this connection is broken and your hand will no longer be able to close or to hold your baton, CS gas, shield or anything else.
This concept applies to all muscle groups, tendons and limbs. If someone cuts or slashes the key tissues responsible for moving a limb, the attacker would most likely disable or at least severely hinder your limb’s function. Sometimes this is referred to as "biomechanical cutting."
Therefore, your flexors tendons or muscles of the forearm, the biceps and triceps muscles of your upper arms, and the major quadriceps muscles just above the knee, require reliable and effective protection from a deliberate attack or cut.
Just above the knee, where the muscles narrow and connect to the patellar tendon, this area is typically covered by a just single layer of trousers material. It is a comparatively large target, and if someone is close enough to reach your body, that person will clearly also be close enough to reach your quadriceps. Cutting this target is called "mobility kill", and it means that you will no longer be able to effectively defend yourself.
Although many will claim that this approach doesn’t work, historical evidence from sources suggests differently. Perhaps the best-known reference comes from the Filipino martial arts. Their key tactic is called “defanging the snake”… or targeting the attacking limb to destroy its structure and function. According to their symbolism, the weapon is the “fang” and the arm wielding it is the “snake.” Removing the fang from the snake immediately eliminates the primary threat to the defender -- the attacker’s weapon.
In the traditional Filipino knife arts, one of the prime objectives is to cut the attacker’s wrist or forearm. The goal is to sever the flexor tendons that connect the forearm muscles to the fingers, destroying the attacker’s ability to grip his weapon. Cutting the muscles on the inside of the forearm can produce the same effect.
Can you see the risks involved when confronted by someone wielding a knife? Most are concerned about being stabbed, but many trained specialists might have other plans, and that’s when slash resistant clothing makes sense.
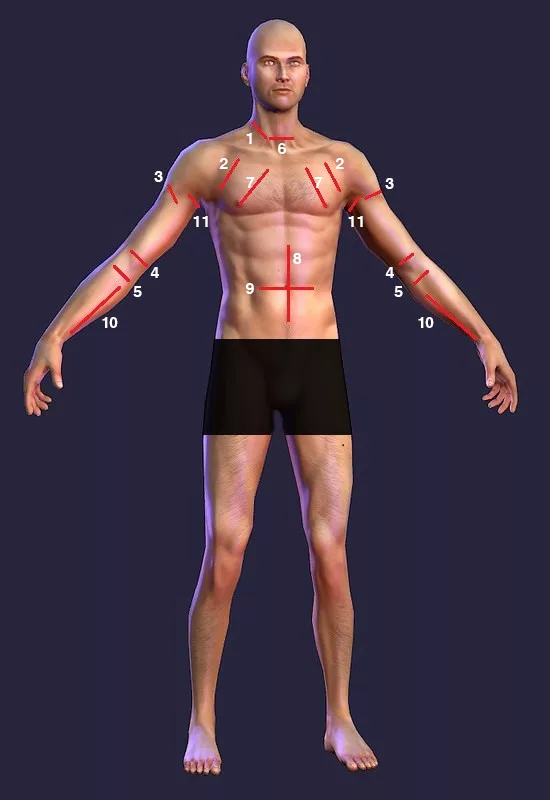
Please refer to the photo included with this article to understand the most vulnerable "slashing targets." Each "successful" cut or slash can or will either lead to rapid blood loss and subsequent death (most likely caused by shock and blood loss, or dramatically decrease your mobility.) The photo does not feature all targets, but is a selection of some of the key targets of the front of a human torso.
- The side of the neck and throat just about even with the Adam’s apple. This area contains the Carotid Artery and Jugular Vein. If either is cut the attacker will bleed to death very rapidly. The Carotid is approximately 1.5″ below the surface of the skin, and if severed unconsciousness, will result in death in approximately 5-15 seconds.
- A powerful cut to the outer side of the Pectoral muscle can potentially sever the cephalic vein, which will bleed profusely.
- A powerful cut across the front of the Deltoid muscle may sever the cephalic vein.
- A slashing cut across the biceps can disable any motion of the arm and can cause rapid blood loss.
- A slashing cut across the inside of the elbow joint. In addition to the numerous veins, this area also contains the ligaments that enable motion in the forearm.
- A horizontal cut across the neck and throat will not only sever your Jugular Vein and cause death, but will also cut the trachea and ligaments that control movement of the head.
- A powerful slash across your Pectoral muscle will destroy your ability to throw punches with any power.
- A powerful vertical slash, leading to the penetration of the abdominal wall, will result in loss of motion and possible disembowelment.
- A powerful horizontal slash to the abdomen, leading to the successful penetration of the abdominal wall, will result in loss of motion and possible disembowelment.
- A more than one-inch penetrating slash to the inside of the forearm between the radius and ulna bones will sever the radial artery (this artery runs across the top of the radius bone 2-4 inches behind the base of your thumb). Severing the radial artery can result in unconsciousness in as little as 30 seconds, and death in as little as two minutes.
- The Brachial artery runs along the inside of your arms. This artery is deep, but severing it will result in unconsciousness in as little as 15 seconds, and death in as little as 90 seconds.
We are extremely passionate about safety, and our mission is to let the world know that personal safety can be improved dramatically without compromising the ability to effectively operate and function.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!







