Mobile Device – Where Logical and Physical Come Together
Security executives and enterprise officials can use tools to physically protect mobile devices as well as the information contained in them. One example is software-based “black-listing” applications.
Mobile users do not have to carry photo and video cameras, laptops, address books or other necessities -- nearly every option is available in one tiny device. Offering many more options than those of previous generations, devices like smartphones combine some great capabilities offered by computers, photo and video cameras and phones, making a busy life more manageable than ever.
WHAT KIND OF THREATS
But what threats do business and consumer users encounter when they own and carry mobile phones? One of the biggest worries is loss or theft, and, most importantly, the loss and misuse of business or personal data with it.
Many mobile users enter secure information such as security data, bank account numbers and passwords, contact information or business correspondence. There are ways to better protect that information. For example, software packages for Windows Mobile Pocket PC protects mobile users’ data by locking it against unsolicited access. The mobile user can enter unlimited private phone numbers and letters, keeping all important information in one safe, easy-to-access place, always at hand.
At the heart of such an approach is a diversity of unique information forms and easily customizable templates. Mobile user’s security, business and private data -- such as passwords, credit card numbers, user names, codes, PINs, addresses, travel information, insurance policies, software keys, and more -- can be securely saved and protected. Information cards can be arranged in folders, with the ability to create new ones when necessary. In the example above, a desktop agent synchronizes data between the mobile device and PC.

Krishna Laudenslager is a technical writer based in suburban . Katia Shabanova is with Paragon Software Group.
CSOS DEPEND ON MOBILE DEVICES
Of course, chief security officers and their staff members still rely on a mobile device as a telephone. There are drawbacks to being instantly accessible. The mobile user can be reached any time of the day or night by unsolicited phone calls or SMS messages. How many times a day do we receive unwanted phone calls, wasting time and sometimes disturbing important meetings or activities?
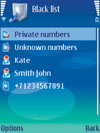
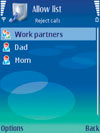
There are now options protecting the mobile user’s privacy and saving time, while also offering that much-needed peace of mind. For example, one important category of software allows mobile users to block all unwanted callers by adding phone numbers to the “black list,” either permanently or for a set period of time, or to create “white” lists -- special contact groups whose phone calls will be allowed to be received while all other calls are rejected. Users can also choose a “reject” action that will automatically send callers a prewritten text message, all fully customizable and simple to use.
The application allows users to professionally
manage and reject all types of incoming calls from intrusive people, private or
unknown callers, and to temporarily block all calls except those the mobile
user designates. The unwanted calls will be recorded and can be viewed on the
application’s call log. Such an approach also allows a floating indicator on
the phone’s active standby screen showing the name of the list in use and
numbers of missed
phone calls.
Security has always been an issue with business and personal computing, but it has become increasingly important for mobile users in security and business operations and who have become reliant on such gadgets.
SIDEBAR: Mobile Devices Turning into a Financial Wallet
And then think of the security headaches.
First, naturally, in , but coming to a hand near you. Cellular telephones and especially smartphones are turning into a way to buy things.
There is no swiping. With just a keystroke or two, a person can purchase everything from boiled soy beans and digital cameras to a flash drive or a three-course dinner. It’s the ultimate in convergence between a telephone and a credit card.
The next step? Mobile, multi-functional devices such as smartphones will turn into a door access card, too.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!




