Nine Things You’re Not Destroying But Should Be
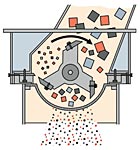
Inside a disintegrator, a rotary-knife mill shreds waste until the particles are small enough to drop through a screen with a mesh size (as small as 1/8”) chosen in accordance with the waste type and the customer’s security needs.

Used computer innards and keyboards make their way up the conveyor to the hopper of one of the country’s largest disintegrator.
So, kudos to all of you responsible people who do the right things to protect your business from information theft. You have figured out paper; but what about other threats you might not be aware of? What about all those electronic records floating around your security office or the CEO’s office? If you are not dealing with them, paper is the least of your worries.
As computers and other electronic devices become obsolete sooner due to new technology, disposal of sensitive information is of serious concern. Just one hard drive or CD can contain thousands of files, and when a digital file is “deleted,” the information actually remains on the computer’s hard drive, CD or diskette, as do deleted e-mail messages and records of all online activity.
These days it all can be recovered with sophisticated tools.
This is worth remembering before donating old computers to a school, for example. In some cases, old computers are removed and resold by the vendor who installs the replacement computers.


Computer parts and other metal waste end up as “E-scrap,” some of which can be recycled. A large disintegrator reduces metal to strips (left) that can be run through another disintegrator and pulverized to tiny bits (right) for added security.
PROPER DISPOSAL
The accompanying chart lists some obvious and not-so-obvious items that could cause significant problems if not disposed of properly. All of these items can be made harmless by one of three methods:- Shredding – Reducing to small strips via a paper shredder or similar device.
- Degaussing – Using powerful magnets to permanently eliminate data from magnetic media.
- Disintegration – “Mechanical incineration” that continually cuts items into smaller and smaller pieces until they are unrecognizable and unreconstructible.

Adjacent to the disintegrators, bins of materials awaiting destruction are stored inside locked cages at a high-security destruction facility in Westboro, Mass.
another source.
Data security is an ongoing process, but by being aware of threats and understanding destruction options, you will be in a much better position to protect your business and yourself.

To handle destruction of computer and communications equipment as well as sensitive objects, chief security officers can turn to outsourced services with special, heavy-duty equipment. For example, Security Engineered Machinery (SEM) just opened a facility specializing in the destruction of sensitive electronic records. Monitored with 17 video cameras, it accepts waste from businesses and government agencies throughout the United States. All of the facility’s equipment has been approved by the U.S. National Security Agency.
SIDEBAR: Consider Outsourcing Destruction Needs
At first, enterprises such as financial institutions and healthcare facilities, often beholding to regulations and privacy compliance requirements, brought in outside services to destroy paper-based records. The outsourced firms use specially equipped trucks and certify compliance.But with the advent of computer media, a new way of outsourced destruction has emerged. One example: Security Engineered Machinery now destroys sensitive electronic records for businesses and government agencies throughout the United States. The company’s new high-security destruction services facility is next door to its main office in Westboro, Mass.
“This is a major step for us, but we are just responding to a growing demand,” SEM President Peter Dempsey told Security Magazine. “You see it on the news every night -- losing confidential digital information can mean identity theft, corporate espionage or even a risk to homeland security.”
All of the facility’s equipment has been approved by the U.S. National Security Agency. The cost and size of SEM’s powerful disintegrators would exceed the budgets and space limitations of the companies that send a multitude of items to the new facility for secure destruction. The rotary-knife mills in these machines make short work of computer hard drives (or even whole central processing units), CDs, DVDs, diskettes, microfilm, credit cards, ID badges, audio and video cassettes, circuit boards, PDAs (“Palm Pilots” and the like), cell phones, x-rays, flash media (digital camera “thumb drives,” etc.) and key tape. Everything ends up as “E-scrap” -- unrecognizable shreds that can be as small as 1/8” in diameter.
Prototypes and off-spec batches of toys, clothing and pharmaceuticals go into the same disintegrators, to keep proprietary product specifications out of the hands of “dumpster divers.”
Fully bonded and insured, SEM monitors the entire operation with 17 video cameras around the clock, seven days a week. Customers who drop off their items in person are invited to stay and watch the destruction. Those who ship their items to SEM can watch on a designated Web site. Some customers even track their shipping crates with GPS systems.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!