ePassport, eSecurity, eehPrivacy
For identification technology, whether public or private, the goal has been verification of identity at the cost of some convenience. But what about privacy and real security?
Not so suddenly, enterprises and their chief security officers must balance increased security with concerns centering on privacy and hacker intrusions.
A case in point: Gemalto last month receives an order for the U.S. Electronic Passport when the United States Government Printing Office (GPO) placed its first order with the company, following Gemalto’s electronic passport technology qualification completion. The GPO and U.S. Department of State evaluated the solution at their testing facilities and confirmed it fully satisfies the agency’s requirements for privacy protection, security, durability, manufacturing yield, and transaction speed and communications performance. The GPO, on behalf of the U.S. Department of State, plans to incorporate the electronic capability in all new passports to be issued in 2007. The United States produced over ten million passports in 2005.
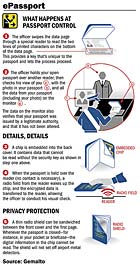
The electronic passport (e-passport) technology includes a secure operating system software running in a large capacity contactless microprocessor chip. The chip is embedded in a module that is highly resistant to damage and then is integrated into the passport booklet cover.
Chip Info
The computer chip in the passport will contain all the information that is now printed on the document’s data page including a digitized photograph of the passport owner. The text data and the photograph can be read with a contactless reader at a border entry point and the electronically provided data can be compared to the information printed in the passport at issuance. Not to be confused with RFID, secure personal identification devices using contactless smart card technology have built-in and active security and encryption capabilities to protect information access and communications. More than 30 nations worldwide have already pledged to adopt passport technology that conforms to an international standard for electronic identification data.
Some have raised security concerns.
A recent security conference hosted by Black Hat suggests that biometric e-passports used in the UK and other countries can be hacked. The demonstration exposed a vulnerability that could potentially allow criminals to clone embedded code and enter countries illegally.Luke Grunwald, a security consultant with DN-Systems in Germany, demonstrated how data stored in the passport could be transferred onto bank chips, which could be implanted in forged passports.
But according to Randy Vanderhoof, executive director of the Smart Card Alliance, “The smart card industry does not see a security threat for electronic passports when data can be copied because the data can’t be changed or altered. Even if someone could copy the information on your chip, it doesn’t achieve anything, because that information is locked. It can’t be changed. It’s of no use to anyone else because your picture is on the chip and they’re not you. It’s no different than someone trying to use a lost or stolen passport. The whole program is designed to eliminate the risks of anyone altering or using someone else’s passport credential, and it does.”
The objectives of this global program were to make passports virtually impossible to counterfeit and prevent anyone other than the passport owner from using it. The e-passport program achieves that in two ways:
RFID Conflicts
Beyond e-passports, there continues to be legislative fights over radio frequency identification systems.A number of proposals in California introduced by State Senator Joe Simitian, has grabbed the attention of the security industry. In a letter to the Senator recently, the executive director of the Security Industry Association, Richard Chace, said, that the Security Industry Association (SIA) respectfully expresses its opposition to Senate Bill 768, the Identity Information Protection Act of 2005, and related legislation (Senate Bills 432, 682, and 1078) that could severely impede the use of Radio Frequency Identification (RFID) technology. SIA is an international trade association and leading voice for more than 340 manufacturers, distributors, and integrators of electronic and physical security equipment.
“SIA and its members agree there may be some legitimate concerns about the use of RFID technology in certain applications. However, we strongly believe these legislative proposals could have dire unintended consequences on technology used to ensure the validity of identification credentials. The legislation could set several dangerous precedents: The legislation seems to assume that technology innovation is static; in reality, problems are addressed quickly through the rapid technological evolution for which our industry is known. SIA is concerned that your legislation could lock in a set of criteria that will be obsolete and actually less safe than what technology could make available tomorrow.
“In our opinion, the aforementioned Senate bills give the appearance of favoring particular technologies by banning or restricting the use of RFID to very specific applications. This is neither a customary nor advisable purpose of legislative activity.”
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





