Making the Cut

New anti-terrorist measures include the recording of biometric information at ports of access to a country. For example, the U.S. records facial information in addition to fingerprinting and photography of every person that enters through its international airports. Other countries are sure to follow the American example.
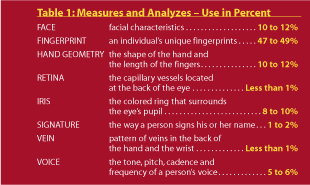
Not every biometric identification technology is as popular as its counterparts, as seen in Table 1. But though the field is still in its infancy, many people believe that biometrics will play a critical role in future computers, especially in electronic commerce. Personal computers of the future might include a fingerprint scanner, for which different genetic identities could be granted various levels of access – the ability to use credit card information to make electronic purchases, for example.

Rapid developments
Technology and development in the many areas of biometrics are moving at a rapid rate, driven largely by the security needs of the federal government. But an increasing abundance of varied solutions is not the answer; the stability of a technology with actual use of standards in an application will produce the best results.
In the field of biometrics, development has taken large strides to produce faster, more accurate, portable and affordable systems. As application providers speed to produce the next best system with new biometric technologies, standards and interoperability tend to just exist in the background as compliant in the application. However, no real use of it exists other than enterprise-type systems offered by a handful of application providers.

Although biometrics technology has been used in private sectors for quite some time, Sept. 11 spurred heavy investigation into such technologies. The fast rise of identify theft in recent years is also driving the biometrics market. In response, countries around the world are embedding facial and fingerprint characteristic data on passports and even driver’s licenses. As identification and/or verification by biometrics becomes a necessity, a concern over privacy and personal space will continue to echo in this field.
Process changes
When looking at the big picture, processes will need to be put in place for incorporation of biometric technology to make it easy to use with confidence and trust from the end user. Even though the technologies record only characteristic data with a high encryption, multiple registrations due to different systems will discourage the end user from having their characteristic data recorded multiple times or stored in multiple locations.
Numerous pilot tests have also been notorious for holding back expansion into real world implementations of biometrics. There is a fine line between acceptable pilot testing and actual emergence of a solution. Proper steps are being followed to minimize the work when making changes to a system, but nothing beats real-world results. Many application providers are geared up and prepared to make appropriate changes, but an actual launch of these systems need to happen.
Biometrics is very dynamic. For example, people’s fingerprints are unique, but every time a finger is captured there are other external factors that change the condition during capturing. Therefore, it is difficult to choose a sensor that will work every time when that particular finger is placed on a sensor. An acceptable performance standard should be proposed and met by technology providers, while a reasonable tolerance should be accepted by those seeking biometric solutions. Without an understanding of the technology and its proposed standards, rather than adopting a system, potential users simply end up repeating the test cycle indefinitely.
As systems are adopted and standards fall in place, two major concerns are becoming apparent: the protection of data, and the need for a strong legislation defining how data will be used by governments and corporations. Both considerations would require the development of a certificate of authority for those able to register a biometric into a common database.
End users can play a significant role in the future of biometrics by way of education and awareness. Although biometrics technologies are relatively easy to use, they only become so when they’re familiar. Often, end users need only simple devices to ease the application of biometrics. For example, a simple notification for entry applicants to wipe residue from their fingers could make the difference between a successful biometric access control system and a high-tech complaint generator.
End users will also play a significant role in deciding which devices make the cut. Buyers should weigh all the trade-offs between price and value (security) of a product. Biometrics is part of high technology and thus should always stay competitive without a decline in security. But end users need to know what to expect when they are evaluating such systems. Apples need to be compared to apples. If a system is drastically less costly than another system then most likely the end user should expect a performance difference between the two. End users also should learn more about their vendors and qualifications. Familiarity of standards will protect end users from being locked into a specific technology and allow them to define the shape and use of biometrics for future generations.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





