Home » penetration testing
Articles Tagged with ''penetration testing''
Can You Measure Your Building’s Penetration Risk? - Part 1
Part 1 of a 2-part series on security entrance metrics
January 31, 2017
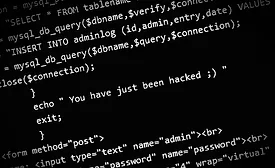
Simulates Attacks on Networks to Test Responses, Security Levels
Red Team from NTT Security
December 1, 2016
Sign-up to receive top management & result-driven techniques in the industry.
Join over 20,000+ industry leaders who receive our premium content.
SIGN UP TODAY!Copyright ©2026. All Rights Reserved BNP Media.
Design, CMS, Hosting & Web Development :: ePublishing