The hidden environmental costs of VPN gateways

Image via Freepik
In networking, we often discuss routing, packets, protocols and latency. It’s always been our lifeblood and our passion. Another area we are passionate about is hardware. A new router, firewall, switch, or network appliance will elicit numerous debates and send us into a world of what if? What if I deployed this box to my network? How would it impact it? Would it make the network faster? Would it make my job easier? Now, one topic we don’t discuss is the “green” impact of this new box.
Our networks are complex and costly; truth be told, they impact the world around us. Let’s take a look at the journey of an employee, Amy, who is part of the hybrid workforce. Her day begins in her home office, which is located at the kitchen table of her house. Every day, Amy must use the corporate VPN to access the applications she requires to complete her job. Her journey looks like this.
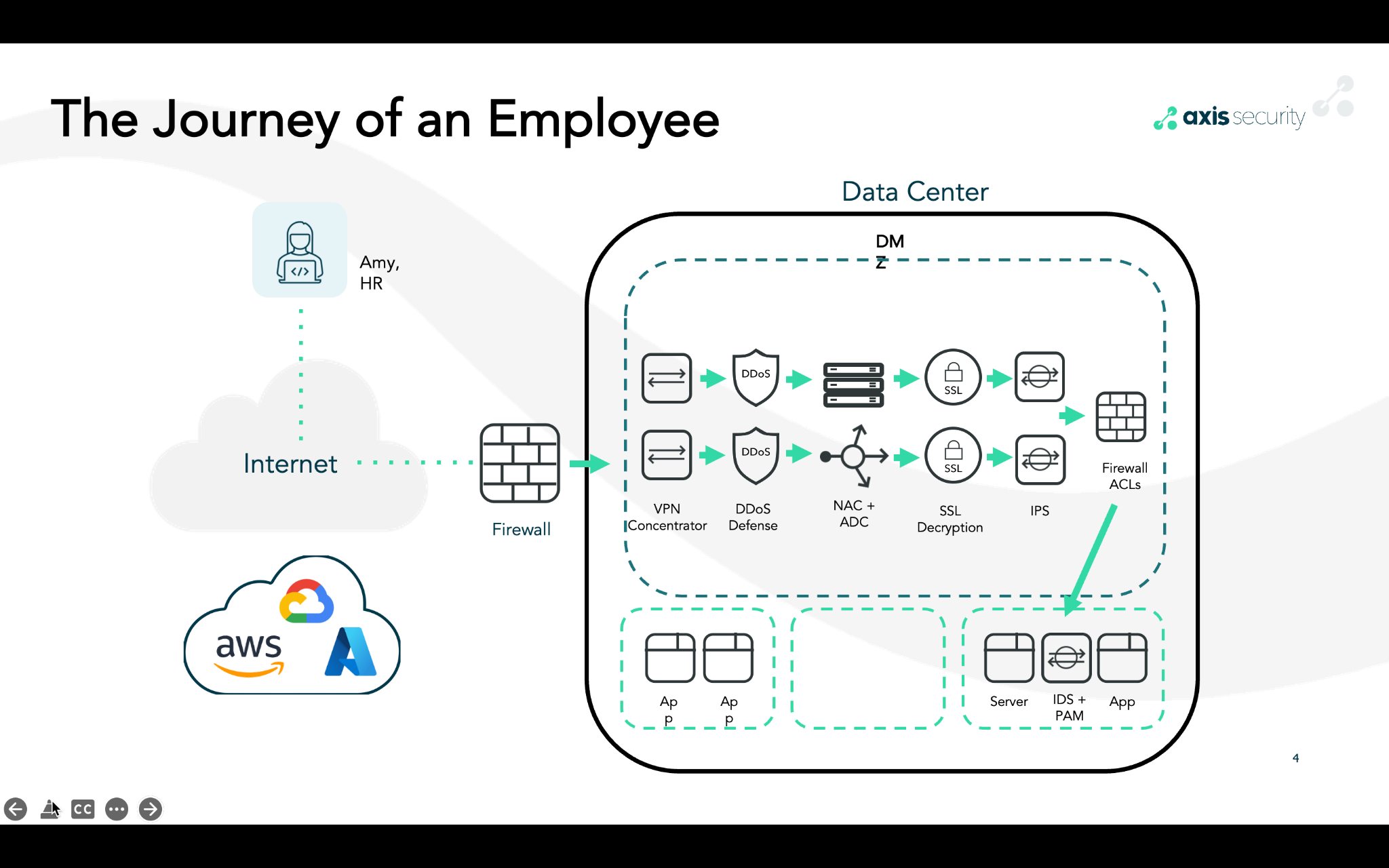
Amy must run a virtual gauntlet of IT network and security hardware appliances. Typically, this may include a series of seven systems, each with a redundant twin for high availability.
So, what is the impact of these 14 boxes on our planet? Let’s break it down.
Amy’s point of entry is the data center firewall. Typically the firewall is the second most power-consuming device. For our scenario, we will select Palo Alto Networks PA-5430 firewall. The power ratings for this device come in at 630 watts. Since our design is redundant, we will need two of them. Therefore, the total for the two is 1260 watts.
Next up is the Denial of Service appliance. This time we will go with a product from Cisco Systems. The selection will be a Cisco the Defense Pro 20. Its power requirements are rated at 320 watts. Again, we will need two for high availability, so the number is 640 watts.
NAC and ADC are next on the path. While there are appliances in this area, we will leverage Cisco ISE. While we could build this out a number of ways, let’s keep it simple and call it two servers running a dedicated application. Power requirements will come in around 850 watts per server. Again, we need two, so 1700 watts is our total for NAC and ADC.
On to the SSL. For the SSL decryption, we will go back to Cisco. The Cisco Firepower 5555 is our most efficient solution at 134 watts at peak. We need two, so 268 watts is our number.
Now comes the IPS system. Again, we will go with a Cisco Firepower product, the 9300 appliance. Unlike the Firepower 5555, the 9300 is power-hungry at 1000 watts for both.
And we are almost done. One more firewall to go! Again, we’ll go back to Palo Alto Networks. Add a pair of PA-5430 at 1260 watts.
Now that we’ve completed Amy’s journey from a network and security appliance point of view, let’s add up our power budget and determine the power costs and, most importantly, the impact on the planet.
The power budget comes to 6,128 watts at peak. Based on a cost of power at .32 per kWh, at 24 hours a day, creating 146 kW/h per day (aka 53,681.28 kW/h per year), our total per datacenter cost comes to $17,178 each year — just in electricity costs. This doesn’t include Manufacturing costs either.
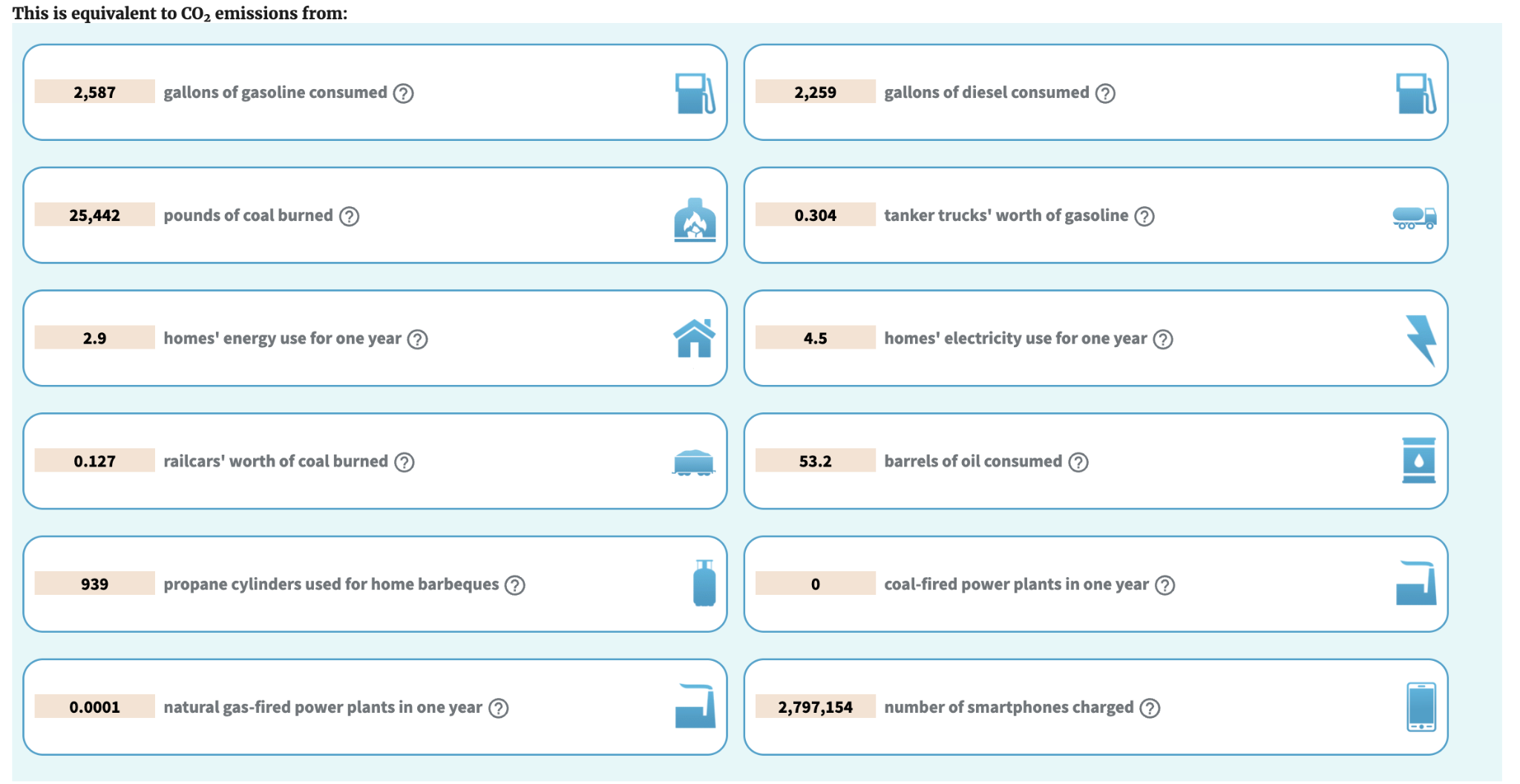
But what is the total carbon impact? We used the free Greenhouse Gas Equivalent calculator provided by the EPA and found that 53,681.28 kW/h per year is equivalent to 25.6 tons of Co2 per datacenter! That is equivalent to what 27 acres of U.S. forests sequesters per year. Check out some other interesting equivalencies below.
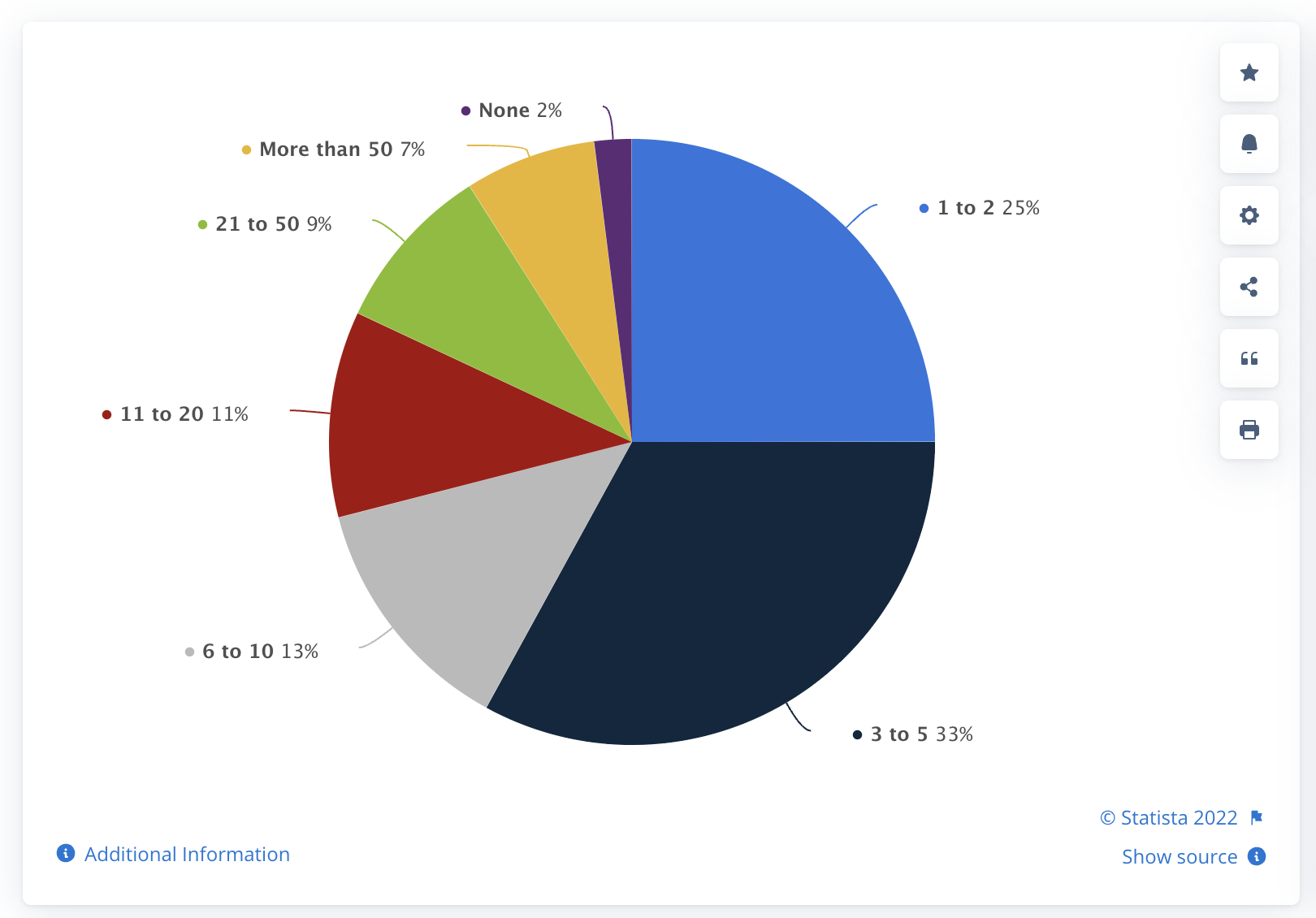
A report commissioned by Statistica found that 73% of companies have 3 to 5 data centers in use. 40% of companies have six or more.
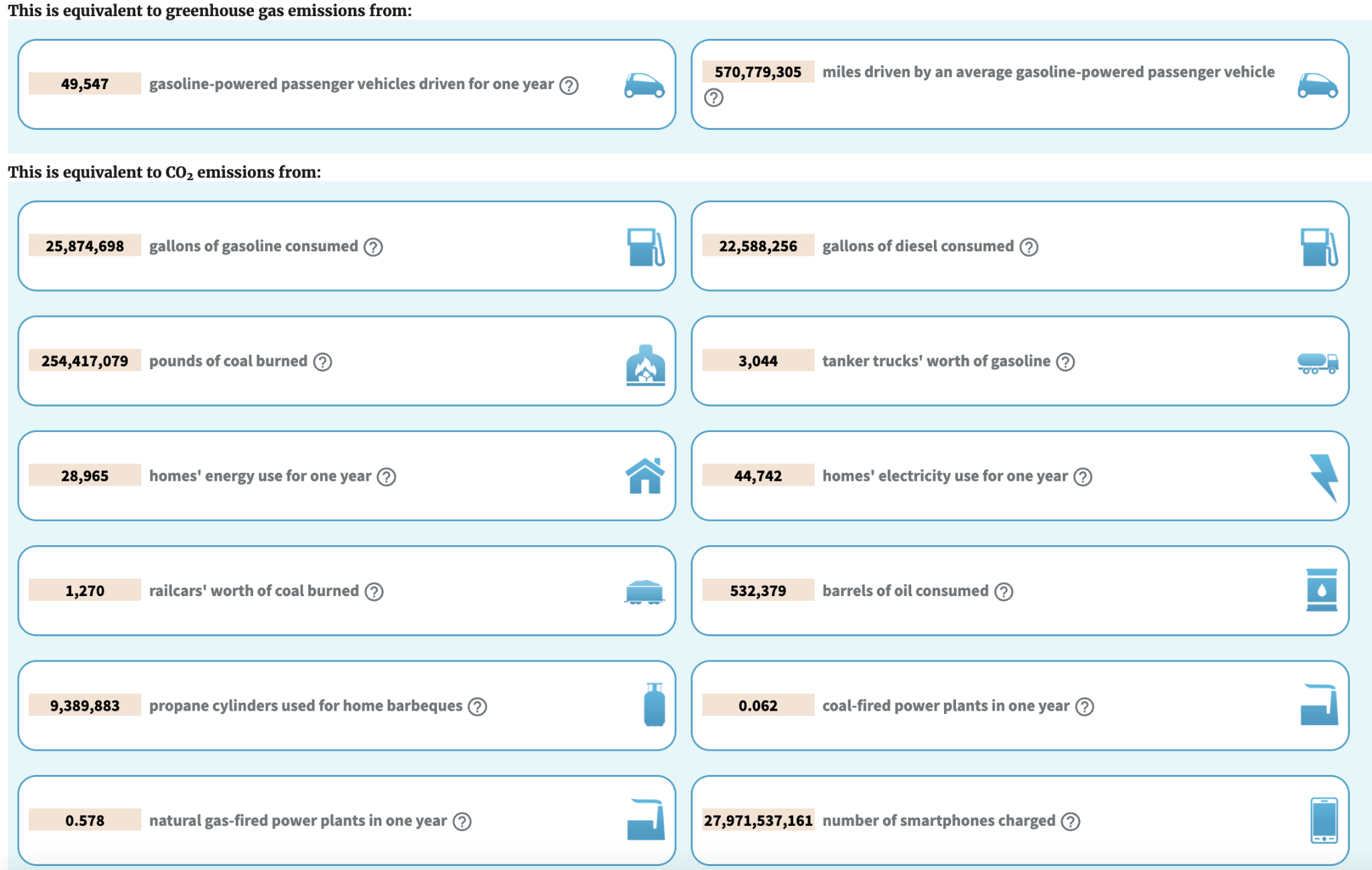
So if we assume 5 data centers for each Fortune 2,000 company (most will likely have more), the electricity costs alone for the VPN gateway would be $85,890 per year (again, only for electricity). The environmental impact would be 128 tons of CO2 emissions. Times that by 2,000 Fortune companies, and that’s 253,475 tons of CO2 emissions. The equivalent to the carbon sequestered by 272,129 acres of U.S. forests.
That’s a lot of green, for too much green. It’s time to say bye to hardware-based VPN and move to new cloud security technology. A move from VPN to the cloud is beneficial not only from an operational, security, and digital experience perspective but from an environmental impact perspective.
*Images courtesy of Axis Security
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





.webp?height=200&t=1744084367&width=200)