Effective SMB security on a budget

Image from Pixabay
All too often do small to mid-sized businesses (SMBs) find themselves in need of security risk management immediately following an incident. These reactive organizations don’t have an internal security risk management capability and often require help with short-term security needs.
Building toward a long-term security strategy is key to protecting an organization. Small to mid-sized organizations typically only have a need, and the budget, for a single security role. Therefore, this role needs to be filled by a security generalist with experience across a broad range of security-related programs.
There are many strategies lone SMB security managers can employ to create and maintain fast-developed and financially sustainable security programs that mitigate risk, protect employees, promote situational awareness, preserve culture and build resilience.
I have designed the below security risk management model specifically for SMBs. This system of programs is designed to be scalable, cost effective and quick to implement by a corporate security manager with three to five years of experience. The diagram below shows the essential programs that should make up the security risk management system for a SMB.
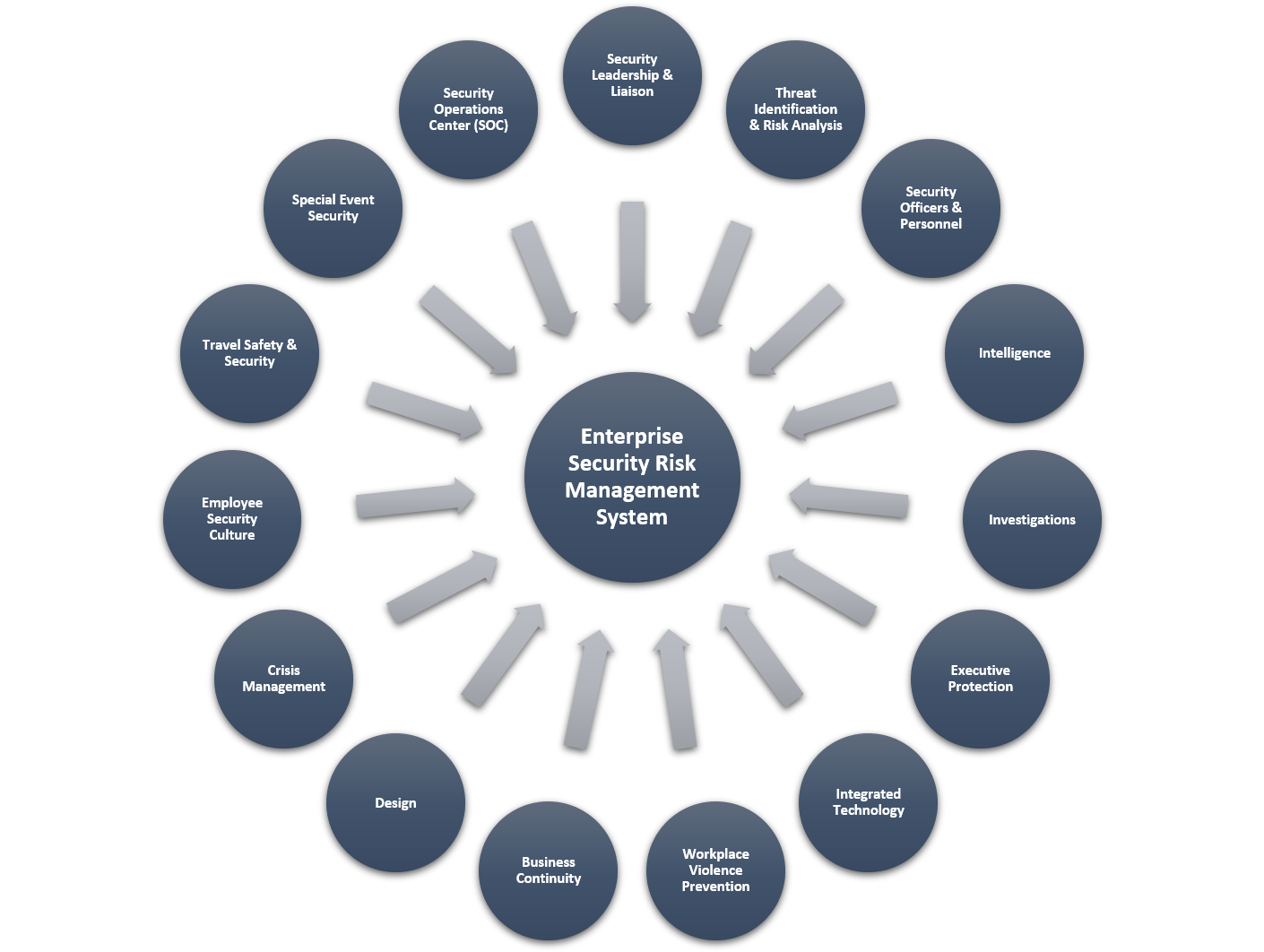
*Click the image for greater detail
Image courtesy of Turner
SMBs with a single security manager are often constrained by tight budgets and need to be creative in how they mitigate the risks presented by identified threats. Getting started with programs shown in the above diagram can help benefit SMB security. Let’s look at three topics in depth — security leadership and liaison, workplace violence prevention, and employee security culture.
Security leadership and liaison
More so than ever before, SMB founders and leaders are being held accountable by their employees to provide a safe work environment. The reputation, brand and culture of a company are at stake if they fail to recognize and act on the signs and symptoms that a security threat may be materializing in their places of work.
SMB leaders work tirelessly to create a unique and rewarding culture for their employees, and therefore steps should be taken to protect it. One of those steps is hiring a security leader who will work tirelessly to become one of the most trusted, reliable and responsive individuals in the organization. An effective security manager empowers employees to become security advocates throughout the business.
In addition to strategic relationship building inside the SMB, security managers should strive to build relationships and liaise with outside agencies, such as law enforcement and first responders. Most local law enforcement agencies, both large and small, have personnel who are responsible for liaising with the community. These personnel are often more than happy to meet, learn about the company's needs, and offer services such as training or assessments. Additionally, having law enforcement officers familiar with your site is helpful if they ever need to respond to an emergency situation, as knowing the layout beforehand can benefit the outcome of an incident.
Developing relationships with federal law enforcement often comes with greater resources not available to local agencies. Building these relationships comes with the added benefit of being in position to directly report a crime that falls under federal jurisdiction, whether it is cyber or violent, criminal or terrorism-related. Government resources such as agency memberships and fusion centers can help businesses gain valuable threat intelligence that could affect their enterprise.
There have been many examples of companies benefiting greatly from these relationships. In some cases, companies have reached out to their contact at the FBI immediately upon discovering they have become victimized by a business email compromise (BEC). The FBI was able to assist them in recovering funds (often large amounts) believed to have been lost.
Workplace violence prevention
An SMB workplace violence prevention program should be built on three pillars — policy, training and technology. Let’s look at each one in turn.
The creation of policy is a low-cost, impactful and sustainable activity essential for a workplace violence prevention program. Security managers should partner with the HR and legal teams to determine what policies are already in place. Is there a zero-tolerance policy toward workplace violence in any form and at any level of severity? Are there anti-harassment and discrimination policies, substance abuse policies, business conduct and ethics policies, electronic communications and computer use policies? If policies that govern workplace violence reporting and incident response don’t exist, then the creation of those policies should be the security team’s top priority.
In terms of training, security managers should arrange behavioral analysis; Run, Hide, Fight; CPR/AED; first aid; and security awareness training sessions. Finding a local police department to conduct train-the-trainer sessions with the security manager can help reduce the costs associated with training, such as bringing in outside consultants and instructors.
In addition to general employee training, the security manager should ensure that they and their own team keep up with regular, specialized security training as well. Sessions geared towards threat assessment and risk management can benefit security teams while working to prevent workplace violence.
Alongside training, security technologies can aid teams in identifying and preventing workplace violence. Technology such as threat and gunshot detection systems can help reduce response times if a security incident takes place. Security systems that use artificial intelligence (AI) can help the security team automatically detect shots fired.
Employee security culture
One of the primary objectives when leading security operations is to give employees the knowledge and resources necessary to take as much responsibility for their own safety and security as possible. Often the experience and expertise needed to build security awareness is already present in the organization — you just have to know where to look.
More so than ever before, raising security awareness needs creativity and outreach — mandatory annual in-person or online security training is not enough. Even with robust support from HR, getting 100% compliance with mandatory security training is very difficult. The likelihood in this scenario is that online training is rushed and clicked through quickly, or even if employees cannot fast forward, they are paying little attention to the training or have it running in the background while they complete other tasks. But mandatory security training should not be dismissed entirely — there is a place for it in many industries, particularly critical infrastructure where compliance with security training and standards is non-negotiable, and where there is the appetite from HR to hold employees accountable for non-compliance.
However, there are other ways to raise security awareness in SMBs without resorting to mandatory awareness training. One such way is to build relationships with the internal communications and marketing teams within the organization. These teams have the creative expertise to help spread the security team’s message across in a way that will permeate the organization and resonate with employees.
When pushing a security awareness message to employees in the modern SMB, security has 5-8 seconds to capture the attention of their audience and get the message across. A stale poster instructing employees to say something when they see something just isn’t enough these days.
Partnering with the internal communications team to create engaging, fun and poignant security messaging can lead to a wider adoption of security awareness. Thinking outside of the box can lead to more engaging security awareness messaging — create short, animated videos of employees keeping a clear desk, finding out where their nearest emergency exit is, or knowing who to call in the event of an emergency. Animations, videos, artwork or sound bites can all be effective in getting security messaging across to employees.
If an SMB doesn’t have internal teams to leverage for help, there are other ways to get creative with security messaging. Reach out to local colleges with graphic design, marketing, brand management, or video production courses to see if any students may be interested in doing a project with the security department for course credits or a small fee.
Another outreach strategy that can be particularly effective in SMB workplaces is a security team pop-up at strategic locations around the office, preferably near congregation areas. One particularly successful pop-up involved offering employees the chance to enter into a prize draw if they stopped and had a sticker attached to the back of their ID badge with the security operations contact information on it.
The above are just three examples of how small security teams or lone security managers can implement high impact, fast developed and financially stable initiatives. More so than ever before, security leaders are being asked to do more with less. Therefore, they need to be innovative in building programs that are going to reduce the risk of threats materializing at their places of work.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!









